The US suspends its cooperation with Russia on ransomware criminals amidst the brutal war the Russian government wages against Ukraine, State Department spokesperson told Sputnik.
“The Russian government is engaged in a brutal and unjustified war against Ukraine, so our channel on criminal ransomware actors is not active,” the spokesperson said.
On Thursday White House notified about the decision the Russian government, Russian Security Council Deputy Secretary Oleg Khramov said in an interview with Rossiyskaya Gazeta.
The notorious ransomware gangs in the world
And while we mentioned the theme it would be interesting to talk about the cybercriminals of this particular kind as well. In recent years the ransomware criminal ecosystem has grown to be a real threat to the users around the world.
But it’s always interesting what’s behind the curtain. And we found some quite interesting info on what you can call them the mafias of the cybercriminal world.
And they for real can be called mafias because of how well organized they are and what sums of money they extort from their victims.
Some of them has now been in the field for years while some of them just recently gaining their fame. This particular kind of cybercrime has evolved from some of the simplest things to now the whole Evil Corporations kind of thing.
Here will be named just a few names but we are pretty sure you’ve heard them somewhere.
What statistics say about ransomware gangs?
Now ransomware criminals largely target high profile business, public sectors and infrastructure operators other than individuals. According to cryptocurrency researchers Chainalysis, in 2020 ransomware victims paid in total up to $350m growing by 311%.
This is an ever improving professional industry with vast networks of affiliates whose job is to make research on a victim, infiltrate and hold negotiations while in the center of all is the gang who develop and operate the malware; but there’s a parity either they work as a ransomware-as-a-service (RaaS) or attack victims directly.
Ransomware-as-a-service or RaaS means that malware operators instead of using the malicious software by themselves they sell it to other cybercriminals to use.
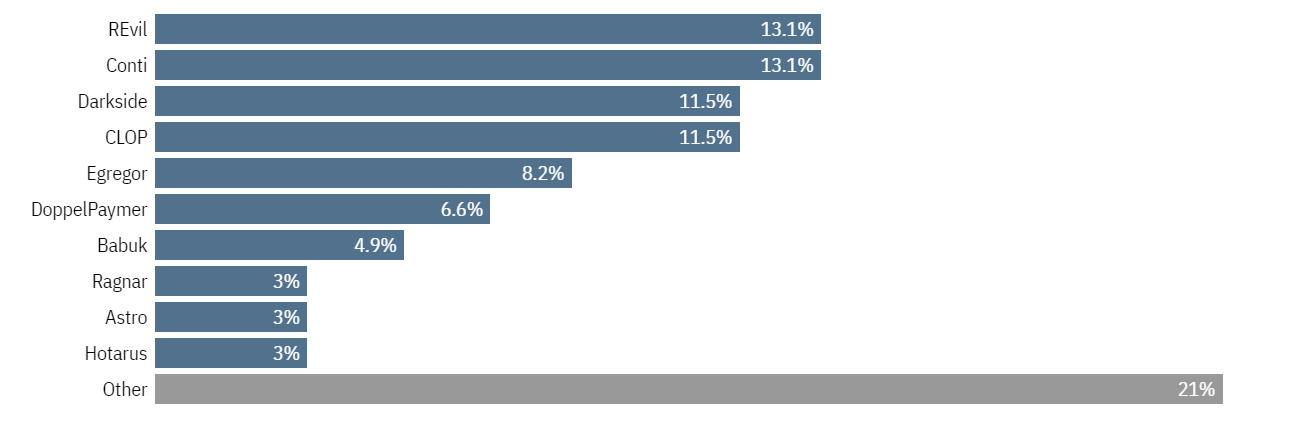
Last year security provider BlackFog made an analysis of the distribution of the malware used in ransomware attacks the same year; the analysis reveals the top ten ransomware gangs in 2021.
Even though the identities of the group members for the most part are unknown, their methods of operating and the scale of the activities are quite impressive.
So the analysis shows the next: in the period from January to May 2021 incidences of ransomware variants as a % of threats detected belong to REvil and Conti as being the most common threat variants in 2021.
Conti (Also Called IOCP Ransomware)
Among the ransomware criminal groups Conti is one at the top of the list. The FBI states the group has conducted over 400 cyber attacks on organizations around the globe. And their demands go up to $25 million.
Although being the best of the best doesn’t mean the group guarantees to give back your files. Cybersecurity specialists say instances when this group refused to give back files even when the victim paid the ransom are not rare.
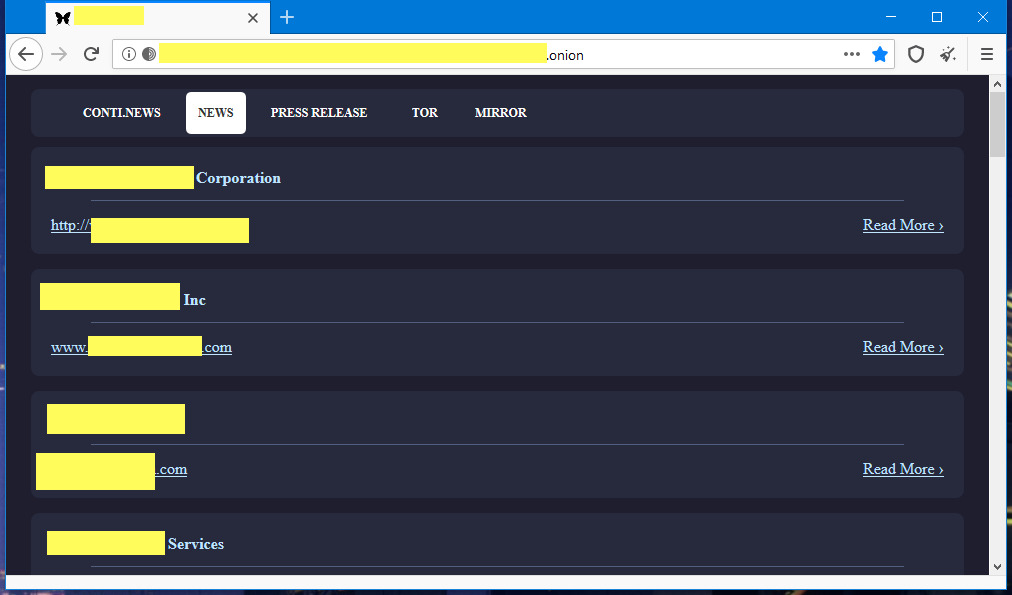
The group has one of the “finest” portfolios of victims among ransomware threat groups including Florida’s Broward County Public Schools with $40 million ransom demand, Irish Health Service Executive causing major delays in patient appointments.
Conti also attacked a government agency in Scotland and government board in New Zealand.
Conti is renowned for employing the technique of double extortion. This means they not only encrypt the data but also steal it so in the future they will have the possibility to threaten the unwilling to pay the ransom victims.
The biggest leak Conti made was from Advantech, manufacturer of chips for IoT devices. 3 GB of data were leaked on Conti’s dark web site.
Apart from this leak, the gang also leaked 20 files of info from Scottish Environment Protection Agency (SEPA) adding that it was only a small part of what was actually accessed by the group.
REvil (Also Called Sodinokibi)
According to the articles by Dark Reading, in the period from January 2021 to July 2021 REvil was the most common ransomware variant having conducted 25% of ransomware attacks.
REvil is a private ransomware-as-a-service (RaaS) group which is also responsible for several infamous ransomware attacks on the world’s largest scale.
This group shows no less ruthlessness than the previous one. According to an article by Cyber Talk, the REvil ransomware group targeted at least 360 US-based organizations. In total the gang has also earned over $11 million.
Among the victims of the group are the energy company Invenergy, software provider Kaseya, tech giant Acer, meat supplier JBS and Apple’s supplier Quanta Computer Inc.
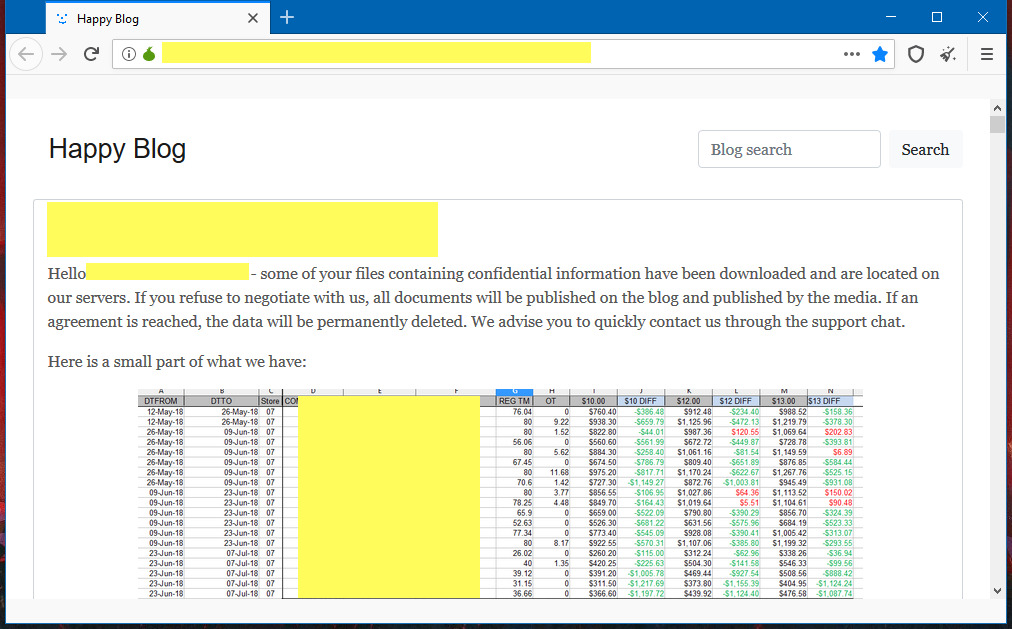
REvil gang also uses a double extortion technique to encrypt and steal the data at the same time. It gives the criminals additional pull to force victims to pay the demanded ransom. Those who refuse to pay will have their data leaked on the gang’s Happy Blog site. Already several companies around the world have their data publicly available on it.
DarkSide Ransomware Gang
Originating from Eastern Europe this ransomware gang at the very start made itself the name. First time it appeared in August 2020.
DarkSide operates as a ransomware-as-a-service (RaaS) and has already targeted multiple organizations across 15 countries. The unusual and peculiar thing about this gang is that it once donated stolen $10,000 to charity.
The gang members try to position themselves as ethical hackers stating that they do not target specific organizations like health, critical infrastructure, governments, schools, etc.
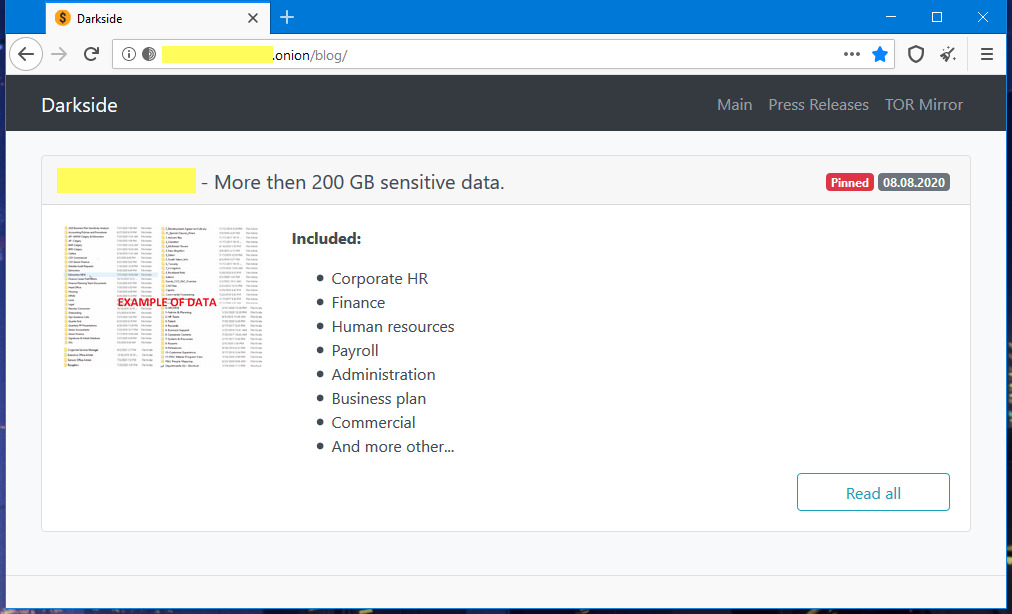
And one more surprising thing is that the group maintains even “customer service” that should ensure the proper restoration of the victims’ systems after the ransom has been paid.
But promoting themselves as ethical hackers they also employ a double extortion strategy in case they will deal with the stubborn victims.
The most famous case is the Colonial Pipeline ransomware attack when more than a week the whole East Coast was paralyzed. The consequences of this attack were so serious that politicians started to talk about the threat to national security.
In addition the group stole more than 100 GB of corporate data from the company.
Clop Ransomware Group
Another no less prominent in the field group responsible for the attacks on Universities of Miami and Colorado, security firm Qualys, residential mortgage servicer Flagstar Bank and the jet manufacturer Bombardier.
But unlike other ransomware gangs mentioned above, this one deploy the triple extortion mechanism. In addition to encrypting data and stealing it they also make threats to customers of the affected companies notifying them over the breach and then urging the companies’ customers to make the company pay the ransom in order to avoid the leak of their personal data.
What else to add?
Certainly it’s not a good sign that the cooperation channel between US and Russia is closed. It means that even the little efforts of the Russian government to stem the ransomware cybercriminal activity on its own territory will more than certainly be reduced to null.
Subsequently it may give “a green light” to those who were previously suppressed by the Russian government meaning that the more arduous ransomware attacks will plunge on the US enterprises and organizations.




