Security researchers have discovered a phishing campaign that is based on the misuse of SVG virus images. Although there have been similar attacks before, they have now become active again. So, how do they work, and why are they so effective? Let’s dive into the details.
Phishing Attacks via SVG Virus
The security experts from Sophos had encountered a new wave of phishing attacks that exploits a previously underutilized approach, with the use of SVG (Scalable Vector Graphics) file format. These attacks, which began emerging in late 2024, have ramped up since mid-January 2025, bypassing traditional anti-spam and anti-phishing measures.
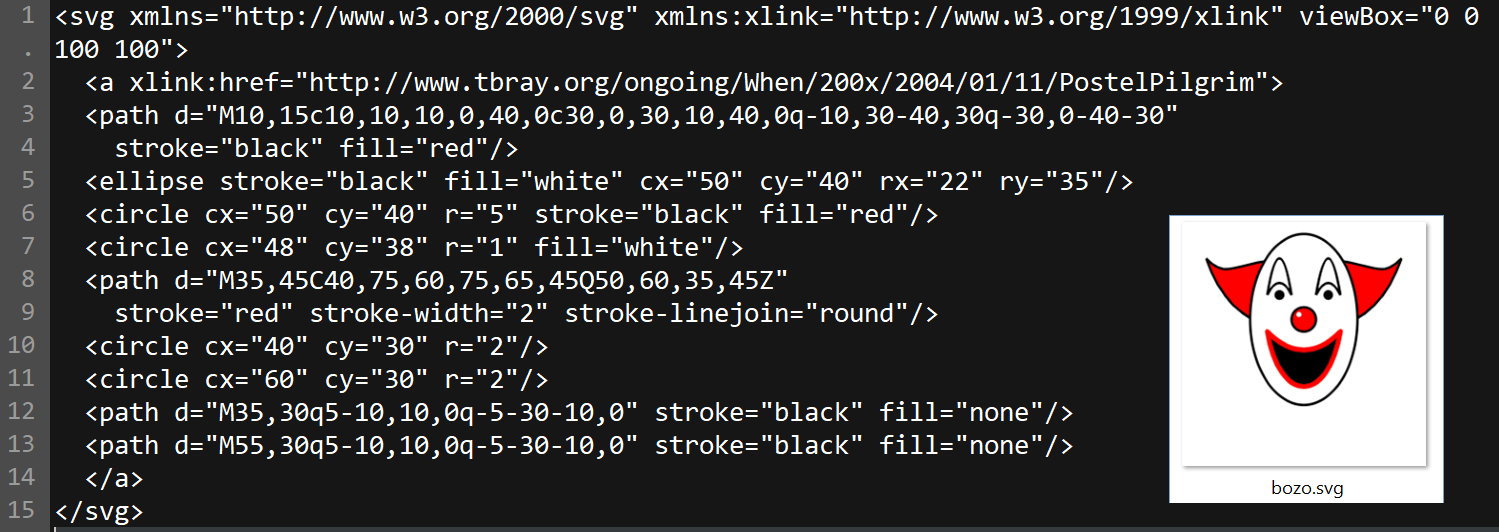
In brief, SVG files are used to create vector-based graphics, such as logos, diagrams, and other images, that can scale without losing quality. Unlike image formats like JPEG or PNG, SVG files are text-based and use XML (eXtensible Markup Language) to describe how to draw shapes in a browser. SVG files also natively support interactive elements like links, scripts, and other web content.
One can often encounter such images in routine work mailing, especially when dealing with graphics in any form (video editing, design, CAD works etc). That is what makes these files an excellent disguise for phishing, and allows for creating believable disguises for malignant emails.
How do SVG Virus Attacks Work?
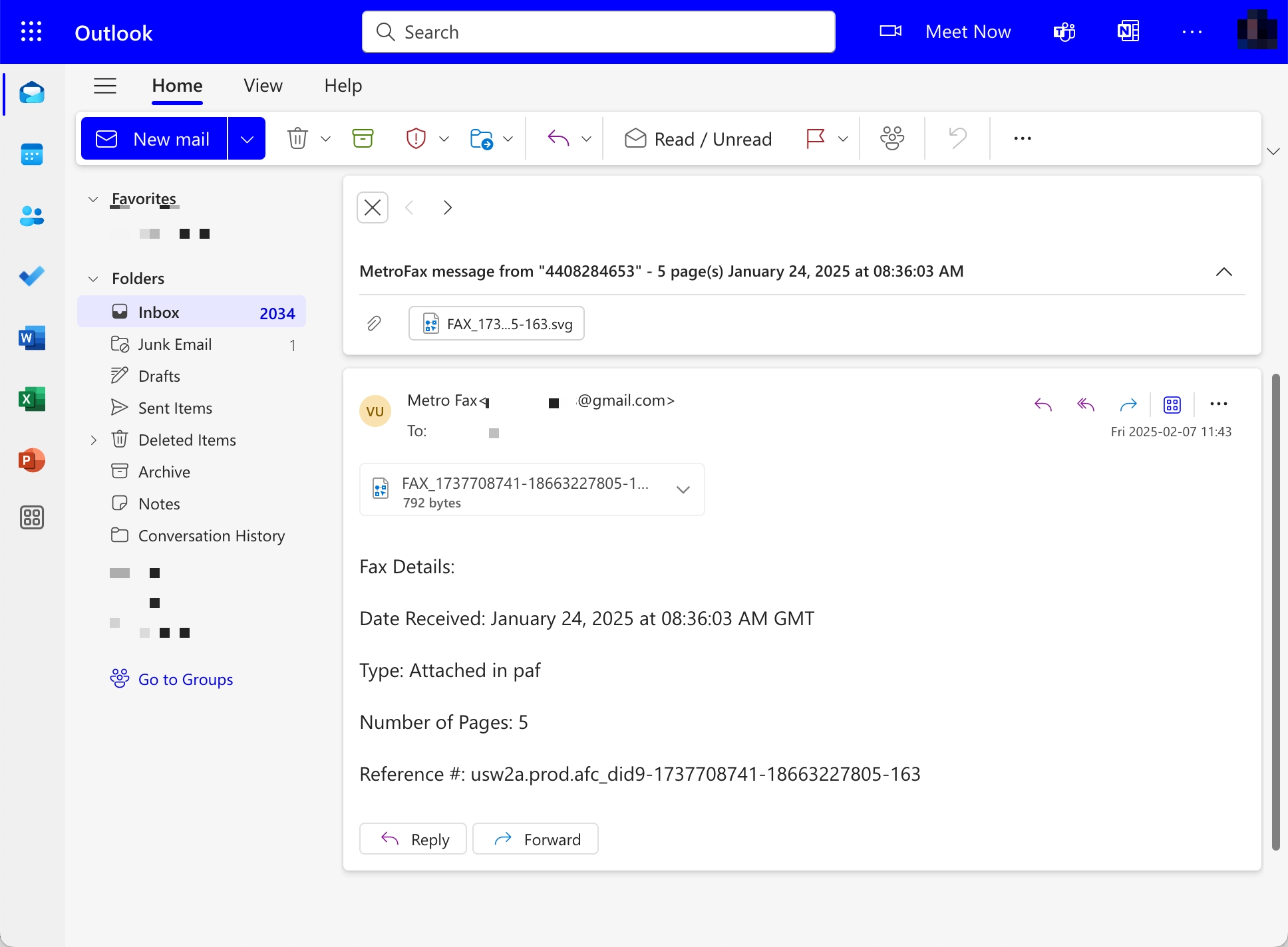
The phishing attacks typically start with an email containing an SVG file attachment. Since SVG files are usually opened by default in a web browser, many users unknowingly open them in their browser. The file then displays a basic graphic, such as a simple rectangle, but also includes an anchor tag (a link) that redirects the victim to a phishing page.
Once the victim clicks the link, they are taken to a social engineering page designed to steal their credentials. These pages are often disguised as one containing legal documents, voicemail notifications, or contract agreements. Such sites are crafted to look like legitimate login screens for well-known services DocuSign, Microsoft, SharePoint, Google Voice and Dropbox.
Some versions even go as far as using CAPTCHA gates to prevent automated detection. After bypassing the CAPTCHA, the victim is presented with a login page that closely resembles the official site, but hosted on a malicious domain. In some instances, the attacker may pre-fill the victim’s email address into the login form to increase the likelihood of success.
That is done by a simple trick: upon composing an email, a customized phishing URL is added, with the recipient’s email address specified as one of the parameters. Nonetheless, such a fine detail is what lulls the vigilance completely and makes people believe they’re dealing with a genuine website.
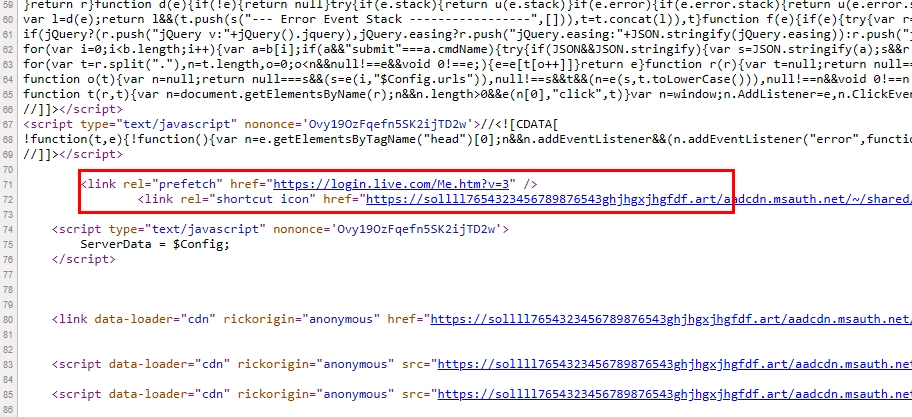
In some attack scenarios, malicious actors have become even more creative. Some SVG virus files embed links to remote images, designed to mimic login pages for services like Google Docs or DocuSign. Others even include hidden blocks of text taken from Wikipedia articles, or use JavaScript to automatically load the phishing page after a short delay, without requiring any interaction from the victim.
The most complex SVG virus attacks start with an SVG file that contains an embedded ZIP archive encoded in base64. Once decoded, the ZIP file can contain a password-protected malicious executable (detected as Troj/AutoIt-DHB) that installs a keystroke logger named Nymeria. This type of attack allows the attacker to capture sensitive data, like passwords, as the victim types.
Avoiding the SVG Virus and Phishing Threat
As we can see, SVG files may only seem innocent, but they pose a serious risk when weaponized by cybercriminals. To defend against these types of phishing attacks, there are a few simple steps users can take:
Change the Default Program for SVG Files. Instead of opening SVG files in a browser, set Windows to open them in a text editor, like Notepad. This ensures that even if you open a malicious SVG file, it won’t execute any harmful code.
Be Cautious of Suspicious Emails. Always verify the sender’s email address, check for unusual subject lines, and look closely at any embedded links. If the link seems off or the domain doesn’t match the expected URL (for example, .ru instead of .com), don’t click it.
Use Security Software. Use security solutions that can detect and block malicious attachments. I recommend considering using GridinSoft Anti-Malware, as it has comprehensive protection and can neutralize the threat before it even performs its action.