Altisik Service is a malicious coin miner that usually installs and runs on the target system without the explicit consent of the PC owner. It disguises itself as a Windows service, which makes it difficult to stop or remove. Let’s have a closer look at how this malware operates and how to delete it from the system.
Altisik Service Overview
Altisik Service is a malicious coin miner masquerading as a legitimate Windows process. It is used for hidden illegal cryptocurrency mining, thereby creating a significant load on the processor (up to 80% or 100%). However, this miner differs in one key aspect – it registers itself in the system as a service. As a result, hackers ensure their malware’s increased sustainability. Attempts to manually stop or delete the service can lead to critical system failures, potentially causing a “blue screen of death”.
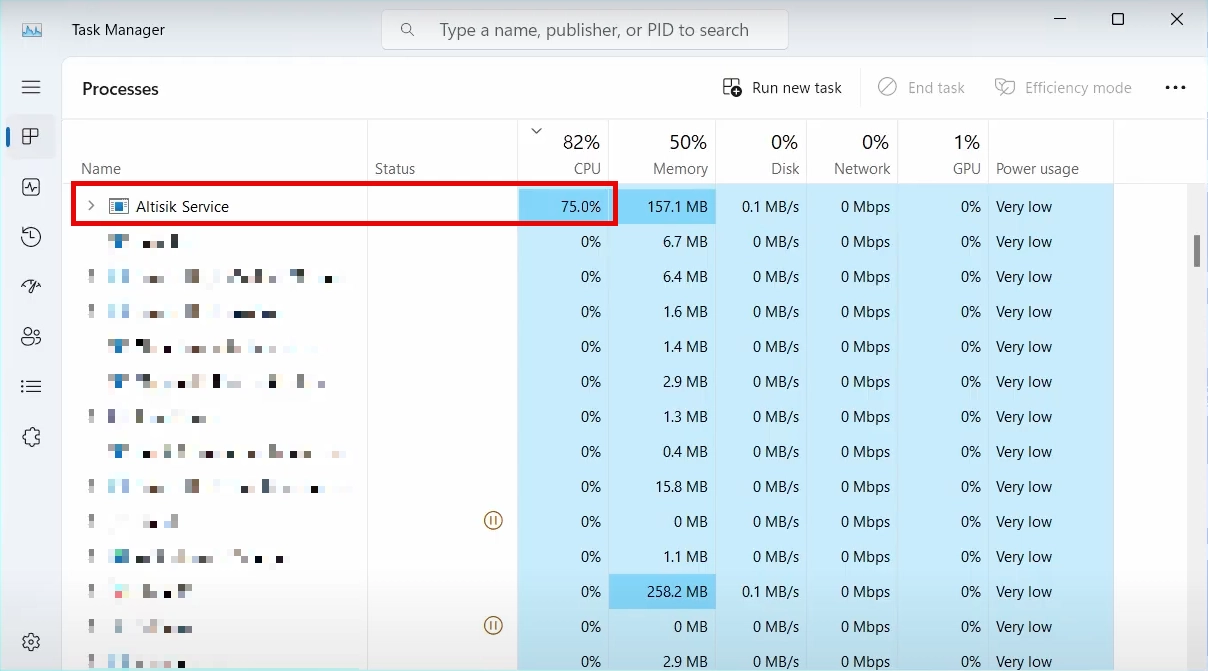
Attackers choose the form of a service for their malware not only for the sake of sustainability. Unlike executable files, services are suspected of malicious activity much less often, simply because users trust them more. Also, Windows services can get higher privileges much more easily, and with less suspicion from security software.
As for the distribution method, users on Reddit report receiving Altisik as an unwanted “bonus” with other software. Miners generally enter systems disguised as bundled software within installers of cracked programs. Another method is through additional malware already present on the computer: vast loader malware botnets can offer huge gains for the operators of malicious coin miners.
Altisik Analysis
Upon execution, Altisik checks for virtual environments and security mechanisms by accessing specific system files and registry keys related to .NET configurations and GPU settings. It pays special attention to Windows Defender settings, especially those concerning real-time protection, by examining related directories and registry entries to potentially disable or bypass these security features. To evade detection, the malware employs stalling tactics with long periods of inactivity, aiming to hinder dynamic analysis and circumvent antivirus sandboxes that might report the file as safe due to lack of immediate activity. These strategies enable Altisik to stealthily operate on infected systems, mining cryptocurrency without user awareness.
Let’s have a closer look at the behavior of the Altisik miner. At the beginning, it is rather typical for a coin miner: upon launching itself, Altisik initially checks for a virtual environment and security mechanisms. Specifically, it checks the following locations:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\machine.config
HKEY_CURRENT_USER\Software\Microsoft\Direct3D\Drivers
HKEY_CURRENT_USER\Software\Microsoft\DirectX\UserGpuPreferences
Further, it pays special attention to Windows Defender settings, specifically ones that touch real-time protection. The malware checks the following system sections.
C:\Program Files\Windows Defender
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\PassiveMode
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection\DisableRealtimeMonitoring
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
The sample employs stalling tactics, including long periods of inactivity, to hinder dynamic analysis. This also helps with circumventing some of the antivirus sandboxes: seeing no activity, one will report that the file is safe.
Persistence and Privilege Escalation
Altisik miner achieves persistence and elevates its privileges by installing itself as a system service. It executes specific shell commands to run helper processes like AltisikHelper.exe and AltisikHelper.dll, which are designed to prevent users from manually terminating the mining activity. Furthermore, the Altisik creates a DirectInput object to read keystrokes, indicating it captures user input. While it is unlikely that Altisik functions as a keylogger, this input capturing could be used for other purposes, such as monitoring user activity to avoid detection or interference.
Let’s look closer: The miner maintains persistence in the system as a service, which grants it elevated privileges. It executes the following shell commands:
"C:\Windows\system32\rundll32.exe" "C:\Users\
C:\Windows\system32\SecurityHealthService.exe
C:\Windows\system32\WerFault.exe -u -p 4328 -s 548
C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding
The AltisikHelper.exe and AltisikHelper.dll processes needed to prevent the user from manually stopping the mining process. Further analysis revealed that the miner creates a DirectInput object, which allows it to read keystrokes. It is unlikely that the Altisik miner can act as a keylogger, but there are quite a few other applications for input capturing.
Network Communication
Altisik uses network communication to send and receive data necessary for its mining operations. The miner communicates with the api.altruistics.org server, likely used for monitoring, control, or data transmission. This may include the miner’s status, statistics, or other mining-related parameters. The response is in text/html format, indicating that the server is returning a web page or text-based data. It also uses Cloudflare DNS 104.18.7.80 and 104.18.6.80, potentially complicating traffic analysis.
How To Remove Altisik?
To get rid of Altisik service, I recommend using GridinSoft Anti-Malware – an effective and easy-to-use antivirus, that will quickly repel any threats present in the system. Though first, I would recommend entering Safe Mode with Networking: go to the Start menu → click Reboot while holding down the Shift button on the keyboard.
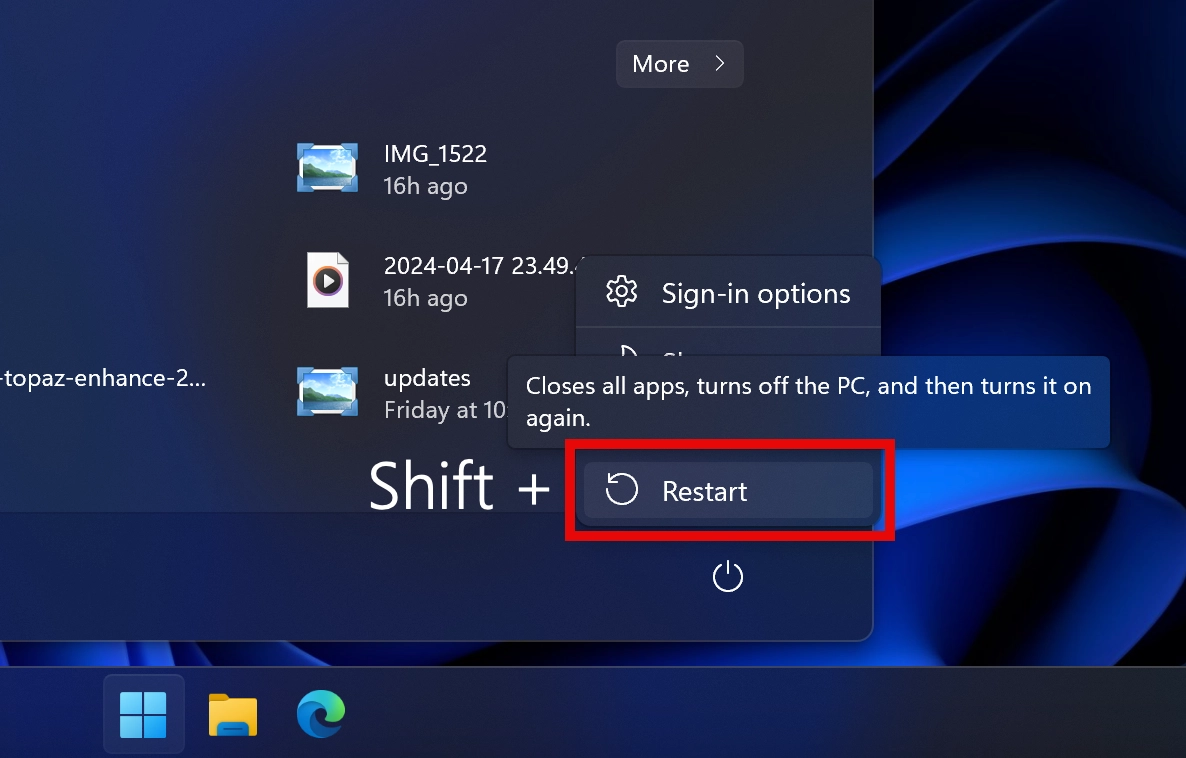
When your PC reboots, in the menu that appears after restarting, select “Troubleshoot” → “Advanced options” → “Startup Settings” → “Restart”.
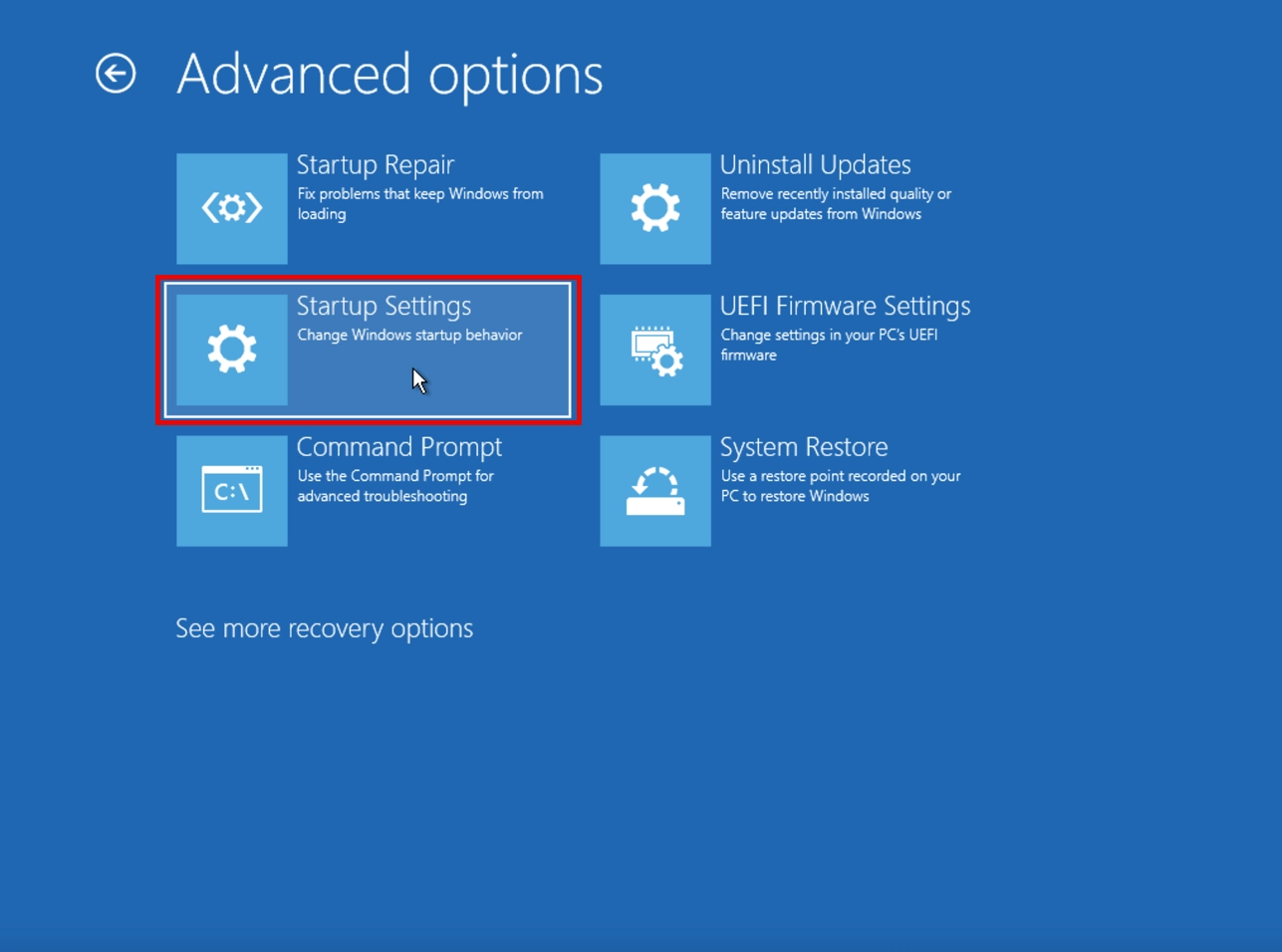
Next, select the Safe Mode with Networking and press the corresponding key (usually F5, though it may vary depending on your Windows version).
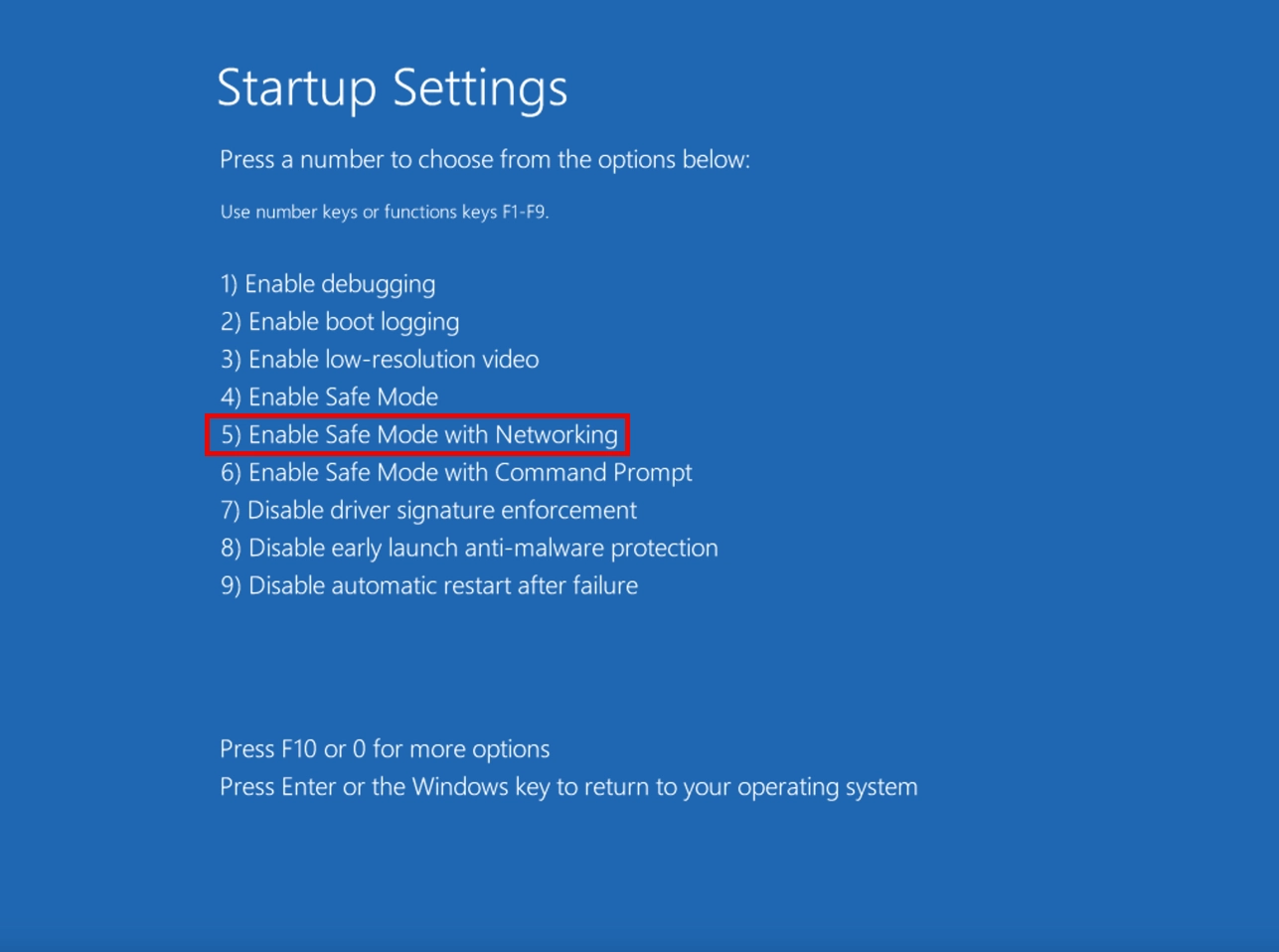
Hint: If you have any problems with switching to Safe Mode, please read our guide: How to Remove a Virus From a Computer in Safe Mode.
After switching to the Safe Mode with Networking, follow the steps below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.