A backdoor in liblzma library, a part of XZ data compression tool was discovered by Andres Freund. The maintainer of the distribution noticed a half-second delay in the updated version, which eventually led him to the flaw. The latter appears to be the brainchild of one of the new XZ maintainers, who pulled off an outstandingly sophisticated supply chain attack.
Backdoor in XZ Compromised Numerous Linux Systems
The story around the backdoor in XZ data compression tool is nothing short of marvelous, from both ends, and may probably be screened in future. A guy under the nickname Jia Tan was making his way to the status of project administrator since 2021. Typically for any tech savvy open-source project user, he started offering his fixes for bugs and new functions. Allegedly by creating a huge number of bug reports, the guy forced the manager to seek for an aide, with Jia being the best candidate at that moment.
This long road was needed to hide a tiny, deeply concealed backdoor (CVE-2024-3094) that is not even available from the public GitHub repository. The catch actually hides within the version that goes to the dependent project, mainly major Linux distributions. Files responsible for the backdoor initiation appear as test ones. This explains why it took so long: to avoid detection, Jia Tan was forced into adding each piece gradually, making it look like a development routine. A proper special operation, one may say.
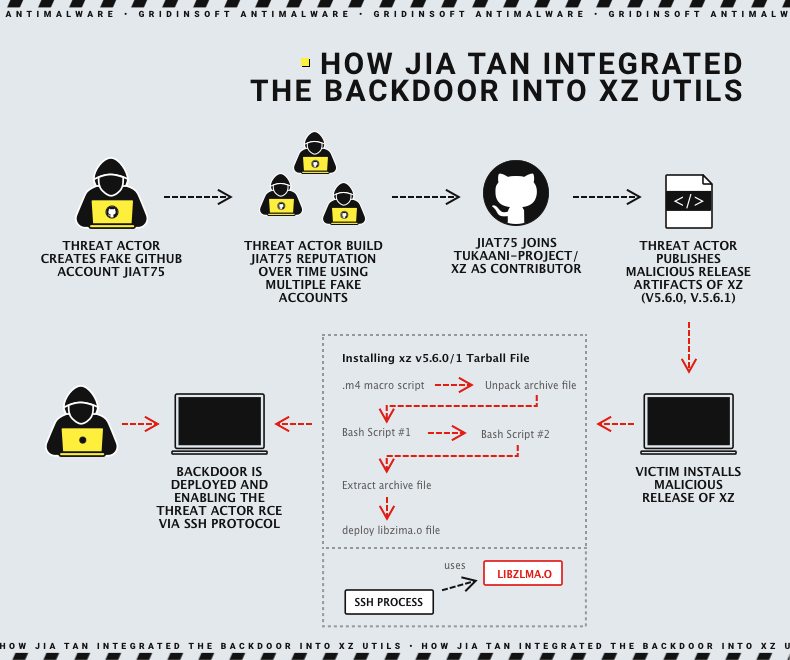
The resulting flaw allowed for the unauthenticated SSH access to any machine. The only condition here is the infected XZ package and SSH usage. This, in turn, endangers thousands of servers that system administrators quite commonly connect through this protocol. Linux is a backbone of cloud servers, and having such a backdoor access effectively means leaking all the data they store.
More of the special operation things surfaced during the ongoing investigation. Shortly after Jia pushed the malicious fixes, numerous XZ update requests popped up in feedback hubs of different Linux distributions. Investigators suppose that either Jia Tan or his associates posted these comments. Some of the distros adhered to them and pulled the infected version, effectively installing the malware into their product.
How Was It Discovered?
The way the backdoor was discovered, on the other hand, sounds more like a miracle. Andres Freund, the developer, noticed that the SSH authentication takes 500ms longer than usual. Also, the operation started taking more CPU power than it used to, which intrigued Anders to search for a new bug. Searches quickly led him to the updated XZ version, and consequently to the backdoor built into it.
Andres Freund released his notification regarding the malicious changes on March 29, 2024. It is still unclear how long these changes were live, but Linux distributions were using them in release versions since early March. Among them are the following distros and versions:
| Kali | All the versions after March 26 |
| Arch | All the versions after 2024.03.01/VM images 20240301.218094 and later |
| Alpine | 5.6 versions before the 5.6.1-r2 update |
| Debian | Only unstable versions, starting from 5.5.1-alpha-01 to 5.6.1 |
| OpenSUSE | All Tumbleweed and Micro OS versions released between March 7 and March 28, 2024 |
| Red Hat | Fedora Linux Rawhide/Fedora Linux 40 |
Mitigations and Fixes
Upon discovering the backdoor code, the project maintainers instantly took down the GitHub repository. Though, further research showed that there was no need for this. As I’ve mentioned, malicious code was hidden in test files, mainly used in dependent projects like distributions. This, however, did not make the task any easier.
Together with the developers and maintainers of affected distros, Andres Freund elaborated both the list of affected versions and possible mitigations. Users should downgrade to the versions that do not contain malicious code, or upgrade to ones where it is already gone. At the same time, the investigation keeps going, as this supply chain attack can have more severe effects.




