Zabbix, a network monitoring tool widely used in corporate IT infrastructure around the world, appears to be susceptible to SQL injection attacks. The flaw encoded as CVE-2024-22120 affects all the versions from 6.0 and can potentially lead to remote code execution. The researcher who detected the flaw already published the proof-of-concept exploit, meaning that the flaw exploitation may happen sooner than later.
Zabbix SQLi Vulnerability Uncovered
On May 17, 2024, a severe vulnerability in the Zabbix utility was discovered. Back in late February of the same year, Maxim Tyukov, the threat researcher, published a detailed description of a flaw on the support page thread on the developers’ site. Zabbix themselves assigned the CVSS rating of 9.1, while the official ratings from NVD NIST are to come. The report is finalized by the potential damage from the successful vulnerability exploitation.
As it appears from the report, it is really easy to exploit the flaw. All the adversaries need at the start is the low-privileged account and the access to a single host – just to be able to run an exploit script on it. Then, after a short tinkering with the values related to the said account’s login session, the attacker is capable of executing the exploit. It will take some time to start working, as it has a short delay between each action, to avoid triggering the alarm. But after around 10 minutes, the attacker will have access to the entirety of the database.
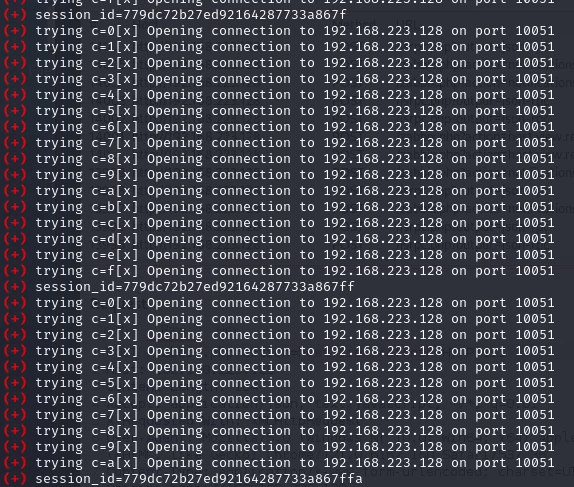
Due to the nature of Zabbix software kit, the kind of data an SQLi may leak in the process is not of a tremendous value. However, information about servers count, their hardware load and status is a perfect starting point for reconnaissance. Bearing this data, the attacker can make its path towards specific servers or even machines. Also, as the researcher admitted, the successful exploitation can eventually lead to remote code execution. It may possibly require some additional actions, but still – RCEs are considered the most dangerous vulnerabilities for quite a good reason.
Affected Versions
The original research names a whole array of Zabbix versions as being susceptible to the exploitation. CVE-2024-22120 can plague versions since 6.0.0, and even some of the beta versions of the newest 7.0. You can see the table below:
| Vulnerable versions | Fixed In |
|---|---|
| 6.0.0 – 6.0.27 | 6.0.28rc1 |
| 6.4.0 – 6.4.12 | 6.4.13rc1 |
| 7.0.0alpha1-7.0.0beta1 | 7.0.0beta2 |
Development of all these fixes are most likely the reason why the info about the flaw took 3 months to publish. Zabbix devs released not just the information, but also patches to all the flawed versions. The obvious step from the client base of the software – which is fairly big – is to install those updates. Publishing of the PoC exploit along with the report should be just another stimulus to do this.




