The malicious campaign exploits the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen to spread Phemedrone Stealer. It utilizes intricate evasion techniques to bypass traditional security measures and target sensitive user information.
Phemedrone Stealer Campaign Exploits CVE-2023-36025
Trend Micro researchers uncovered a malware campaign exploiting the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen. This campaign involves the Phemedrone Stealer, which can extract a wide range of sensitive data. Its infection chain begins with cloud-hosted malicious URL files, often disguised using URL shorteners. Upon execution, these files exploit CVE-2023-36025 to initiate the malware download.
The campaign itself is concentrated on social media. Hackers spread URL files, that look as an innocent link shortcut. Clicking it initiates a call to the GitHub repo, that returns the shellcode needed to download and run the payload. While it is not new to see the frauds targeting such places, the use of URL files is what defines the efficiency of the trick. They essentially act as a lockpick to user trust, spam filters and system protection all at once.
CVE-2023-36025: A Gateway for Cybercriminals
In a nutshell, CVE-2023-36025 is a critical vulnerability that affects Microsoft Windows Defender SmartScreen. It allows attackers to bypass security warnings and checks by manipulating Internet Shortcut (.url) files. Despite Microsoft’s patch released on November 14, 2023, cybercriminals have actively exploited the vulnerability, leading to its inclusion in the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) list.
In the Phemedrone campaign, frauds use advanced evasion tactics by utilizing a control panel item (.cpl) file to bypass Windows Defender SmartScreen. By default, it should send you a warning once you the URL shortcut. But the usage of specifically crafted file variant circumvents the protection and executes malicious downloads in the background. Further on the line, a couple of other known Windows weaknesses are exploited, particularly the Windows Control Panel binary.
Detailed Analysis
Attackers spread Phemedrone Stealer malware using cloud hosting and URL shorteners. They exploit CVE-2023-36025 by tricking users into opening .url files. They evade Windows Defender SmartScreen using a .cpl file and the MITRE ATT&CK technique T1218.002. The malware executes a DLL loader that calls Windows PowerShell to download a loader from GitHub. The second-stage loader, Donut, can execute various types of files in memory and targets multiple applications and services to steal sensitive information.
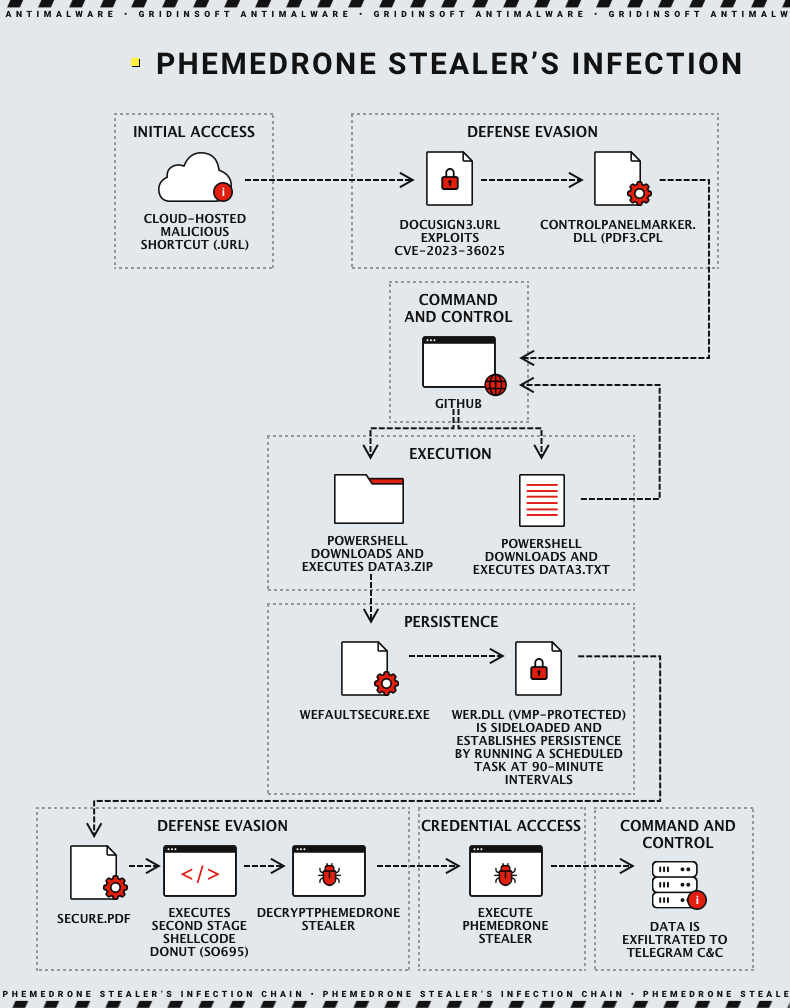
The malware collects system information and compresses it into a ZIP file using MemoryStream and ZipStorage classes. It then validates the Telegram API token and sends the attacker the compressed data via the SendMessage and SendZip methods. The SendZip method uses an HTTP POST request to compress the data into a document and send it to the Telegram API.
Mitigation and Recommendations
In light of this threat, when attackers find vulnerabilities faster than developers fix them, we have a few recommendations in that regard:
- Regularly update your OS, apps, and security solution. This action is crucial as developers continuously address security vulnerabilities through patches. Although the process may seem tedious, it is a necessary and proactive measure to ensure that your operating system, applications, and security solutions are equipped with the latest defenses against evolving cyber threats.
- Be cautious with Internet Shortcut (.url) files. Exercise caution, especially when dealing with Internet Shortcut files, particularly those received from unverified sources. These files can serve as gateways for malware, making it essential to pay attention to the legitimacy of URLs before opening them to mitigate the risk of infection.
- Implement advanced security solutions. This measure detects and neutralizes malware if it infiltrates your device. Robust security software with real-time monitoring and threat detection capabilities adds an extra layer of protection, helping identify and promptly respond to potential threats.
- Stay informed about the risks of phishing and social engineering. These tactics often serve as the initial vectors for malware campaigns. Educate yourself and your team on recognizing phishing attempts, avoiding suspicious links, and verifying the authenticity of communications to minimize the likelihood of falling victim to such cyber threats.