Researchers discovered a new infostealer malware dubbed Vilsa Stealer, with source code published on GitHub. Its easy-to-use interface potentially lowers the entry threshold to make it usable even for people with no PC knowledge. This malware carries other interesting features, and in this post, I will show them all.
Vilsa Stealer Overview
Researchers from cybersecurity firm Cyfirma have identified Vilsa Stealer while browsing through GitHub repositories. The new malware sample primarily targets stored data in web browsers. It also collects login data for messaging applications, certain cryptocurrency wallet extensions, including MetaMask, and other logins and passwords saved in the system. While this list is pretty wide, it is nothing unique: infostealers that are already present on the market show pretty much the same capabilities.
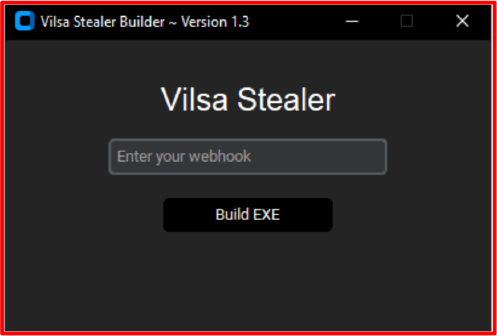
What makes it outstanding though is speed, reliability, and stealth. Vilsa Stealer utilizes multiple stealth techniques, such as obfuscation, which allows it to remain undetected on the system for extended periods of time. It also employs heavy sample encryption, which leads to malware being much harder to detect. Main promotion campaign appears to take place in Telegram – a rather risky approach, considering the latest changes to its data disclosure policies.
Technical Details
A detailed analysis revealed how Vilsa Stealer operates on an infected system. The sample is written in Python and, as I’ve mentioned, heavily relies on encryption to conceal its activity during execution. That is probably the must-have feature for Python malware, as it is quite easy for antiviruses to detect malicious calls on this specific programming language. The payload after all the manipulation is 16.19MB in size and lacks a digital signature, though this part may alter in future.
Once in the system, the malware performs several checks for a virtual environment. It monitors processes using functions like check_windows, check_registry, and check_dll. Thus, Vilsa checks active windows, searches for window titles linked to debugging and analysis tools, and searches the Windows registry for any subsections that might be associated with the virtual environment. If it detects a virtual environment, the malware reports this to its server and terminates itself.
Persistence
Once the malware confirms it is not in a virtualized environment, it aims for privilege escalation and system persistence. It attempts to bypass User Account Control (UAC), and if unsuccessful, prompts the user for administrator privileges. After obtaining UAC permissions, the malware runs a PowerShell command to add the entire C drive to Microsoft Defender’s exclusion list and copies itself to the autorun folder.
Data collection and Exfiltration
The malware then proceeds to its main objective: data collection. It extracts data from browsers, including cookies, autofill data, passwords, browsing history, and cryptocurrency wallets like MetaMask. Vilsa also targets login credentials from apps such as Telegram, Steam, and Discord. It compresses the gathered data into a ZIP archive for exfiltration.
In its final step, the malware encrypts and uploads the ZIP archive to dedicated servers, giving attackers access to the data. Vilsa Stealer communicates with its command-and-control (C2) server at hxxp://bundeskriminalamt[.]agency/pw (83.136.208.208), leading researchers to believe the malware originates from France, not Russia as is commonly believed.
Protective Measures
With all the advanced anti-detection measures of Vilsa Stealers, a proper anti-malware solution with proactive protection is a must for detecting and stopping it. Heuristic mechanisms have proven themselves as reliable solutions, but they sometimes still not enough against the most sophisticated malware samples. This is where AI detection shines the most, as it sometimes notices ridiculously small elements, that hint malware presence.
GridinSoft Anti-Malware is the program that can give you all this protection. And even more – consider trying out our network detection system, that blocks malicious connections at the very beginning. Thanks to the advanced website scanning algorithm, it can spot the shady activity even before any public notifications about the shady activity appears. You can use a 6-day free trial to get taste of the full functionality of the program – don’t miss out!