Ukrainian cyberwarfare sees further action as the UAC-0099 threat actor escalates its cyber espionage campaign against Ukrainian firms. Leveraging a severe vulnerability in the popular WinRAR software, the group orchestrates sophisticated attacks to deploy the Lonepage malware, a VBS malware capable of remote command execution and data theft.
UAC-0099 Exploits WinRar Vulnerability
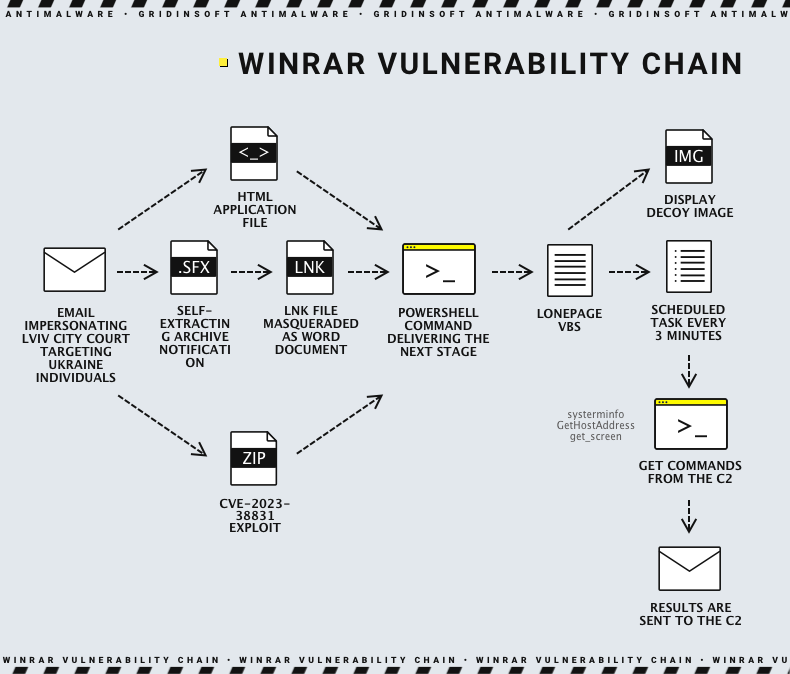
In most recent attacks, UAC-0099’s focus on exploiting the WinRAR vulnerability (CVE-2023-38831, CVSS score: 7.8) signifies a sophisticated approach to cyberattacks. This high-severity flaw in WinRAR, a widely used file compression tool, opens a backdoor for attackers to inject malicious code into unsuspecting systems. Also, the exploit involves the use of rigged self-extracting (SFX) archives and specially crafted ZIP files, designed to bypass traditional security measures and deliver the Lonepage malware directly into the heart of target systems.
Attack Vectors Using WinRAR:
- Self-Extracting Archives Deception: Attackers distribute SFX files, which house malicious LNK shortcuts camouflaged as innocuous DOCX documents. These files, using familiar icons like Microsoft WordPad, entice victims into unwittingly executing malicious PowerShell scripts that install Lonepage.
- Manipulated ZIP Files: UAC-0099 also employs ZIP archives specifically crafted to exploit the WinRAR flaw. These files are engineered to trigger the vulnerability, that further allows frauds to execute arbitrary code.
What is UAC-0099?
The UAC-0099 group, first identified by Ukraine’s Computer Emergency Response Team (CERT-UA) in June 2023, primarily targets Ukrainian employees working for international companies. Their tactics, while not technologically groundbreaking, prove effective in compromising critical information from a wide range of state organizations and media entities. Deep Instinct’s recent analysis reveals a disturbing trend: the group’s consistent focus on espionage, endangering not just the organizations, but also the individuals involved.
What is Lonepage Malware?
Lonepage Malware is a sophisticated Visual Basic Script (VBS) based malware used by the threat actor UAC-0099 in cyber espionage campaigns. It’s designed to stealthily infiltrate target systems and establish communication with a command-and-control (C2) server. Once installed, Lonepage can receive and execute further malicious instructions from this server. Also, its capabilities include deploying additional payloads like keyloggers, data stealers, and screenshot tools. The versatility and ability to adapt to different environments make this malware a significant threat, capable of silently extracting sensitive information and performing long-term surveillance on compromised systems.
Recommendations and Mitigations
As threat actors continue to refine their tactics, it is imperative for organizations, especially those with Ukrainian ties, to stay ahead of these threats through diligent security practices, ongoing education, and robust technological defenses. The battle against cybercrime is ongoing, and awareness is the first step toward safeguarding our digital future.
Here are some tips:
- Ensure all software, especially widely-used applications like WinRAR, are up-to-date with the latest security patches.
- Conduct regular training sessions for employees to recognize phishing attempts and suspicious email attachments.
- Deploy advanced security solutions, including firewalls, antivirus programs, and intrusion detection systems.
- Perform routine security audits and continuously monitor network traffic for signs of unusual activity.