TrojanProxy:Win32/Acapaladat.B is a type of malware that hides in free, unauthorized VPN applications, turning infected computers into proxy servers for cybercriminals. This allows attackers to mask their identities while conducting illegal activities online, such as distributing more malware or launching attacks. In this post, I’ll go into more detail about what it is and how to avoid it.
TrojanProxy:Win32/Acapaladat.B Overview
TrojanProxy:Win32/Acapaladat.B is classified as Trojan malware, as the name implies. It installs harmful proxy backdoors, primarily concealed within free and unauthorized VPN applications. These backdoors enable cybercriminals to exploit infected systems as proxies. As a result, it allows them to perform illicit activities anonymously, such as launching attacks or distributing additional malware.
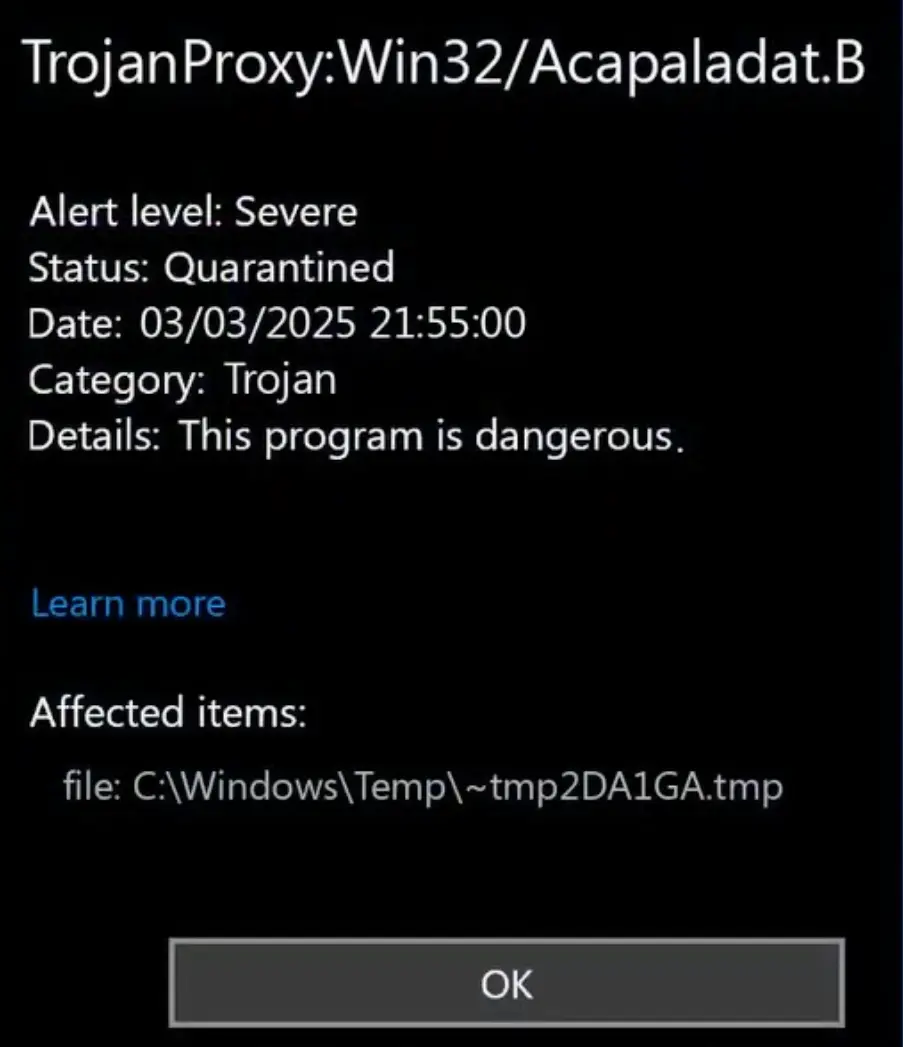
This behavior poses significant risks, as victims may unknowingly contribute to shady operations, compromising system integrity and personal data security. Users report about not suspecting the threat until their antivirus raises the alarm.
TrojanProxy:Win32/Acapaladat.B primarily spreads through free and unauthorized VPN applications, which are frequently bundled with pirated video games and software. This distribution method exploits users seeking cost-free or illegal downloads, increasing the likelihood of infection.
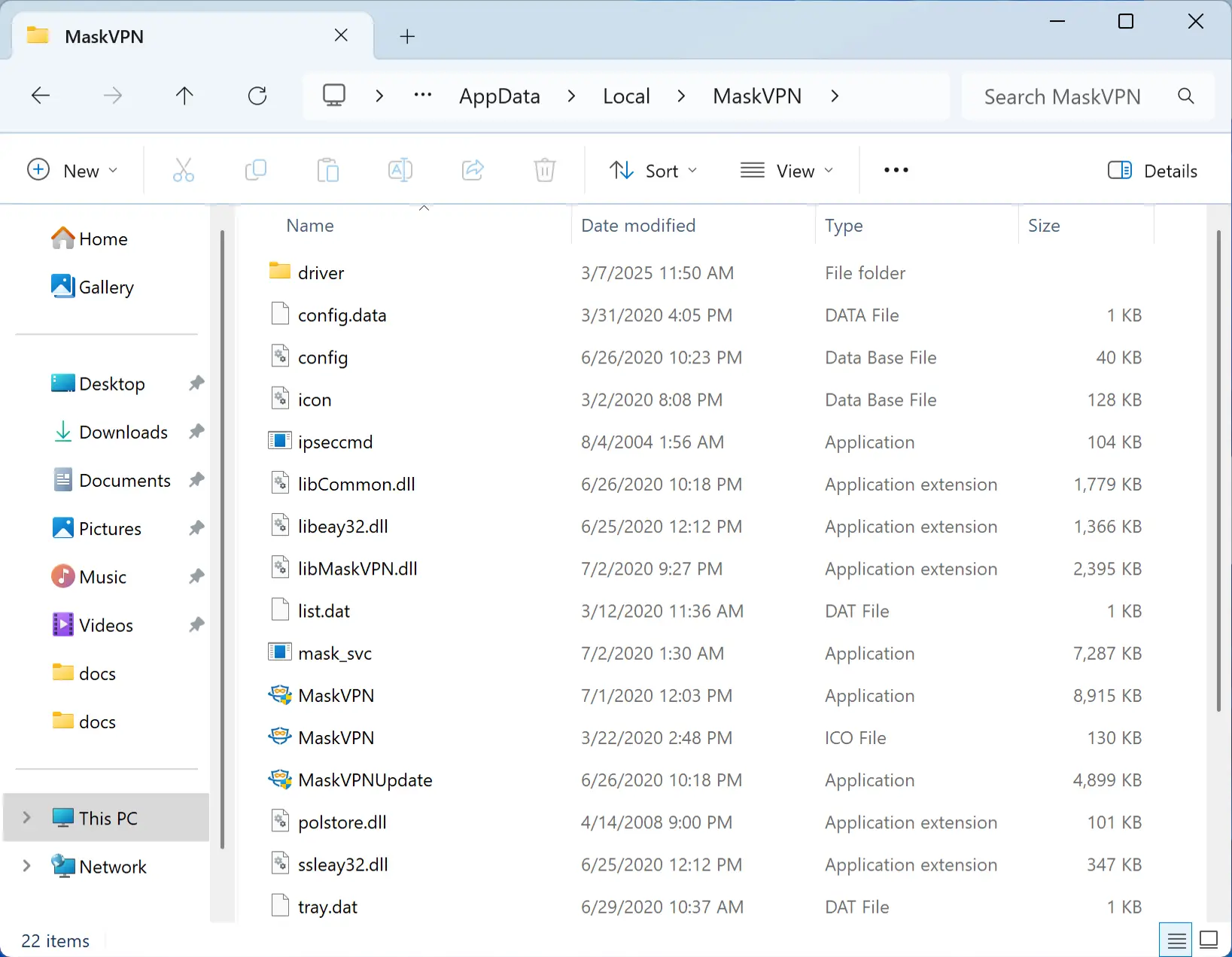
Specific VPN apps associated with this botnet include Mask VPN, Dew VPN, Paladin VPN, ProxyGate, Shield VPN, and Shine VPN, as identified in recent cybersecurity analyses. The malware’s propagation is facilitated by the deceptive nature of these VPNs, which are often marketed as legitimate tools but harbor malicious payloads.
Technical Details
The technical analysis of TrojanProxy:Win32/Acapaladat.B reveals it as a sophisticated threat, with no specific aliases noted in recent reports. Its operation within a system involves several stages: infiltration, installation, configuration manipulation, proxy functionality, and self-preservation mechanisms. Below, I’ve made a step-by-step breakdown of how it functions once it gains access to a target machine.
The malware infiltrates systems through unauthorized VPN applications such as Mask VPN and Dew VPN or is bundled with pirated software. These act as droppers, deploying the Trojan upon execution while bypassing user-level security due to the perceived legitimacy of the host application. It drops executable files into system directories like AppData, Temp, or ProgramFiles under deceptive names such as svchost.exe or update.dll, blending in with legitimate processes.
To establish persistence, TrojanProxy:Win32/Acapaladat.B modifies system configurations to ensure automatic execution on startup. It creates or alters Windows Registry keys under HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run or HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run, pointing to its executable. Alternatively, it registers itself as a scheduled task using Windows Task Scheduler to execute at startup or predefined intervals. In some cases, it installs as a fake Windows service under a misleading name like “Windows Update Service”.
The malware manipulates system settings to weaken security and ensure its continued operation. It modifies Group Policy settings to disable security features such as Windows Defender real-time protection and User Account Control (UAC) by editing registry values or executing commands like reg add or gpedit.msc.
It adds firewall exceptions, allowing outbound connections through specific ports like TCP 80 and 443, ensuring uninterrupted communication with attacker-controlled servers. Additionally, it reconfigures network settings to reroute traffic through the infected machine, effectively turning it into a proxy node by modifying the TCP/IP stack or injecting code into processes like svchost.exe.
A core functionality of TrojanProxy:Win32/Acapaladat.B is its ability to act as a proxy server, relaying cybercriminal traffic through infected machines. It listens for incoming connections from external sources and forwards them, obscuring the attackers’ IP addresses. This is achieved by running a lightweight proxy server module embedded within the Trojan.
Malware maintains communication with a remote command-and-control (C2) server using encrypted protocols such as HTTPS, making detection more difficult. The C2 server provides instructions, directing the malware to proxy specific traffic, download additional payloads, or execute further commands. The infected system becomes part of a botnet, facilitating DDoS attacks, accessing dark web resources, or distributing spam while concealing the attacker’s true location.
Acapaladat virus not only functions as a proxy but also acts as spyware, a downloader, and a backdoor. It can collect sensitive data like login credentials and browsing history by hooking into browser processes or scanning local files, then sending this information to a command-and-control server. Its downloader capability allows it to install additional malware, such as ransomware and banking Trojans. The persistent backdoor enables remote command execution, file manipulation, and potential network spread through shared drives.
To avoid detection, TrojanProxy:Win32/Acapaladat.B uses stealth techniques, such as injecting code into legitimate processes like explorer.exe and svchost.exe, and employing fileless execution methods. It may also utilize polymorphic techniques to change its code structure and can disable security software by terminating processes (e.g., taskkill /F /IM msmpeng.exe for Windows Defender).
How To Remove TrojanProxy:Win32/Acapaladat.B?
The removal of TrojanProxy:Win32/Acapaladat.B is effectively addressed using advanced solution. I recommend GridinSoft Anti-Malware, a cybersecurity tool designed to detect and eliminate various malware. For best effect, you should reboot your system into network-enabled safe mode. This will avoid potential problems when trying to remove the malware, as only necessary system processes are run in this mode.