Trojan:Win32/Stealer!MTB is a detection that indicates the presence of an infostealer on your system. Despite being generic, it still shows enough information to make basic conclusions, but this does not tell you there’s a probability of this detection being a false positive. In this post, I will explain how to understand whether something threatens your system and how to remove the malware.
Trojan:Win32/Stealer!MTB Overview
Trojan:Win32/Stealer!MTB is a generic Microsoft Defender detection that, as its name says, belongs to the infostealer malware type. In summary, this type of malware specializes in stealing information from the target system. Since the detection is generic, it can be applied to any infostealer, so I will describe them here in general terms and then go into more detail with a specific example.
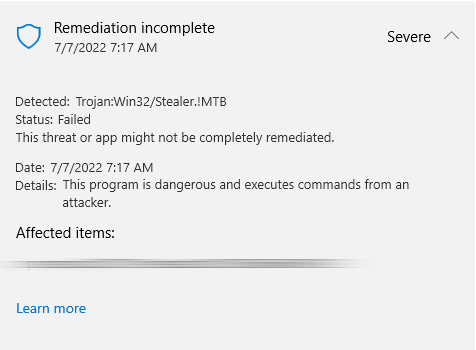
As for the data that this malware can steal, any sensitive info stored on the system is at risk. Infostealer primarily steals login data stored in browsers (encrypted and unencrypted). In addition, it steals user/profile data of local email clients. Trojan Stealer is spreading in a variety of ways. But most often it spreads via compromised pirated software and as malicious email attachments.
Key Characteristics
| Trojan Virus | Disguised as legitimate software to trick users into executing it. |
| Information Stealing | Focuses on extracting personal data such as usernames, passwords, credit card numbers, and other confidential information. |
| Stealth Operations | Operates in the background without the user’s knowledge. |
| Potential Malware Download | May download additional malicious software onto the infected system. |
Understanding the Name
- Trojan: Refers to malware that tricks users into loading and executing it on their systems.
- Win32: Indicates that it targets 32-bit Windows operating systems.
- Stealer: Specifies that the primary function is to steal data.
- !MTB: A specific identifier used by Microsoft to classify and track the threat.
Technical Analysis
Let’s now take a look at how Trojan Stealer behaves in an infected system, using one of the samples. Since this is a generic detection, a short time after detection its name will likely be changed to a more specific threat type. For simplicity, I have divided the entire process into several steps.
Initialization and Privilege Escalation
Like most malware, the first thing the stealer does is check to see if another instance of the malware is running. To do this, it runs an executable file and executes PowerShell commands:
%SAMPLEPATH%\3f7e041e466f779ea61696d2b932da57ce525fefe11972c8a7a489b1a2a9e38e.exe
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
Trojan Stealer then checks for special mutexes and if none are found, it creates them. Mutex is a special piece of code that prevents multiple instances of the program (or malware, in this case) from running on the system. So, if the malware has already been launched, it creates a special mutex. If not, the current instance does the following:
\Sessions\1\BaseNamedObjects\Global\RasPbFile
\Sessions\1\BaseNamedObjects\Global\SyncRootManager
\Sessions\1\BaseNamedObjects\Local\ZonesCacheCounterMutex
\Sessions\1\BaseNamedObjects\Local\ZonesLockedCacheCounterMutex
To ensure that it is running on a live system and not a virtual environment, it performs the following check for system protection status.
HKCU\Software\Microsoft\Internet Explorer\Security
HKCU\Software\Microsoft\Internet Explorer\Security\DisableSecuritySettingsCheck
C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.2102.4-0\X86\MsMpLics.dll
In this way, the malware checks the status of Microsoft Defender and tries to disable it. Next, the malware attempts to gain persistence in the system so that it can run on every system startup. To do this, it uses the legitimate schtasks.exe process and adds itself to autorun:
C:\Windows\System32\Tasks\Updates
C:\Windows\System32\Tasks\Updates\oobbtR
Payload and Data Collection
In the next step, the malware duplicates its files and configs to the AppData folder. This location is not normally visible to a user, hence there’s much less risk of the user raising an alarm or deleting the files. Typically for malicious programs, the file names are obscure and unintelligible.
%USERPROFILE%\AppData\Local\Temp\__PSScriptPolicyTest_dhhkkyeh.5dh.ps1
%USERPROFILE%\AppData\Local\Temp\__PSScriptPolicyTest_ypq04irl.mrv.psm1
%USERPROFILE%\AppData\Local\Temp\tmp8901.tmp
%USERPROFILE%\AppData\Roaming\oobbtR.exe
%USERPROFILE%\AppData\Local\Temp\tmpF5CB.tmp
Next, the threat performs its main task, which is to collect data. In summary, it checks installed browsers, email clients, and other places on the system that may contain login credentials. To elaborate, these are the following locations:
C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Login Data
C:\Users\user\AppData\Local\Microsoft\Credentials\
C:\Users\user\AppData\Local\Microsoft\Edge\User Data\Default\Login Data
C:\Users\user\AppData\Roaming\8pecxstudios\Cyberfox\profiles.ini
C:\Users\user\AppData\Roaming\Comodo\IceDragon\profiles.ini
C:\Users\user\AppData\Roaming\Flock\Browser\profiles.ini
C:\Users\user\AppData\Roaming\K-Meleon\profiles.ini C:\Users\user\AppData\Roaming\Microsoft\Credentials\
C:\Users\user\AppData\Roaming\Mozilla\Firefox\profiles.ini
C:\Users\user\AppData\Roaming\Mozilla\SeaMonkey\profiles.ini
C:\Users\user\AppData\Roaming\NETGATE Technologies\BlackHawk\profiles.ini
C:\Users\user\AppData\Roaming\Postbox\profiles.ini
C:\Users\user\AppData\Roaming\Thunderbird\profiles.ini
C:\Users\user\AppData\Roaming\Waterfox\profiles.ini
The malware compresses all collected data into an archive and saves it in a temporary folder. This way, it will be impossible to detect the data transfer, as the file simply mixes up with the rest of network traffic. But to avoid detection of abnormal package transfer from security software, the malware also uses encrypted connections when it comes to communications with the command server.
Data Exfiltration
The last step in the malware cycle is to send the collected data to the attacker’s command and control (C2) server. But before all that, the malware checks the external IP address of the system through the api.ipify.org service. It’s probably needed to add to a system fingerprint, the set of data that distinguishes one infected system from another. The malware uses Telegram as a command server, specifically calling for a part of Telegram API to send messages via URLs.
https://api.telegram.org/bot5693068931:AAGSQSNIWDJM1FzeZVNHS020I9wVBrQdkRM/sendMessage
On the hacker’s side, this looks like a conversation with a bot that regularly sends back the logs from victim PCs. It is now a rather popular practice to use Telegram as a C2 server, though the exact model of how this works may change after the recent events around the messenger.
How To Remove Trojan:Win32/Stealer!MTB?
To get rid of the Stealer, the best option will be performing an anti-malware scan. Gridinsoft Anti-Malware will be an optimal solution for that task: its multi-component detection system will swiftly delete any malicious elements, regardless of their origin. Below, you can see the detailed guide on how to perform the scanning and remove the threats afterwards.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.