Trojan:Win32/Offloader.EA!MTB is malware designed to establish unauthorized access to a target system or deliver a payload of additional malware. This detection is sometimes associated with uTorrent installers, and in such cases, it is more likely a false positive. Let me describe each of these cases and explain how to remove the actual threat.
Trojan:Win32/Offloader.EA!MTB Overview
Trojan:Win32/Offloader.EA!MTB is a heuristic detection in Microsoft Defender, commonly associated with spyware or backdoor-type malware. Such malware is used to steal data or provide remote access to the target system.
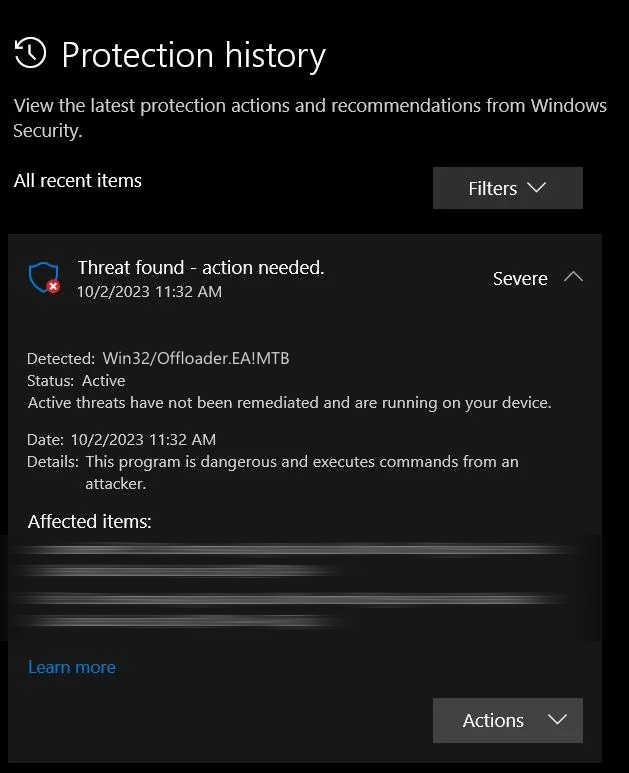
As this is a heuristic detection, it’s based on program behavior rather than specific signatures, which also leaves some room for false detections. It can be triggered by specific program actions, which can sometimes explain why it is linked to the µTorrent installer, which we will discuss near the end of this post.
In terms of distribution, Trojan:Win32/Offloader.EA!MTB is often spread via pirated software, including cracked games or programs. In the case of µTorrent, however, it may appear directly within the installer itself. However, more often than not, after some time, the µTorrent detection may appear under a different name, such as PUABundler:Win32/uTorrent_BundleInstaller or OfferCore.
Trojan:Win32/Offloader.EA!MTB Detection Analysis
First, let’s break down what this detection means. The detection name follows a structured scheme, which helps identify the malware’s characteristics and how it was detected. Trojan:Win32 is a generic classification indicating that this is a trojan designed for 32-bit systems.
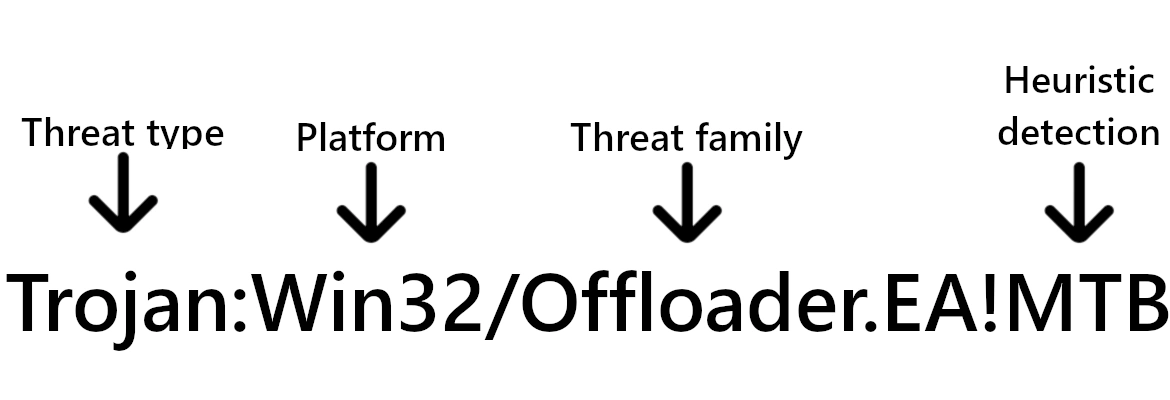
Offloader indicates that the threat can act as a backdoor or loader, allowing it to download and execute additional malicious components on an infected system. Microsoft assigns such generic names for less widespread malware or threats that cannot be attributed to another family. However, this designation can sometimes apply to legitimate programs with similar behavior, which can easily happen in real-world scenarios.
The “EA” fragment serves as a sub-identifier commonly used by security products to classify specific variants and versions within a malware family. In Microsoft Defender’s classification, “EA” helps denote a specific strain or variant behavior, distinguishing it from other varieties.
The “!MTB” suffix indicates that detection was achieved through Microsoft’s machine learning (ML) and telemetry-based analysis (TB). “MTB signifies that the malware detection relies on behavior-based machine learning rather than traditional signature-based methods. Heuristic or AI-based detection significantly increases the likelihood of identifying previously unknown threats. However, this approach can also lead to a higher rate of false positives (which I will discuss next).
Is Trojan:Win32/Offloader.EA!MTB False Positive?
Trojan:Win32/Offloader.EA!MTB may be a false positive detection. In particular, the detection can sometimes be associated by Defender with the uTorrent installer. While this program is classified as potentially unwanted software with its own unique detection name, Microsoft Defender may occasionally label new versions differently.
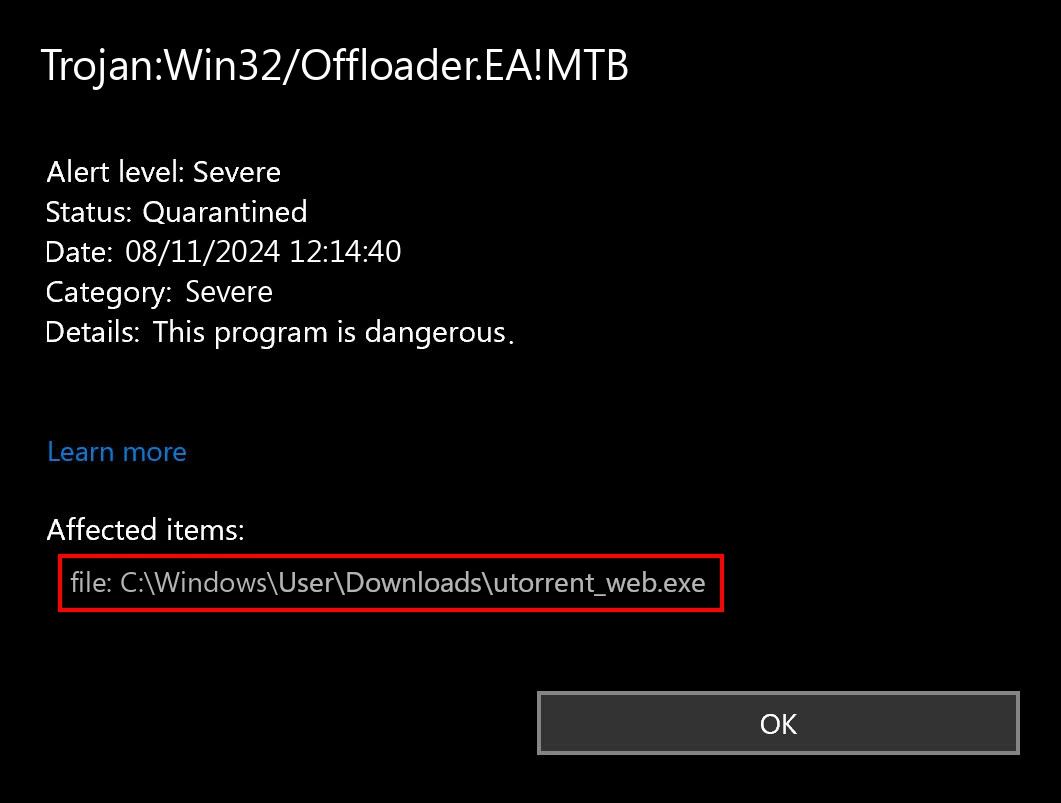
This is due to uTorrent’s installation and monetization practices. First of all, the online installer is used during the installation. The user downloads a small .exe file, which connects to the server upon launch and installs the program as a “payload” in the system.
But questionable P2P downloading software aside, there is a chance of other legit programs falling under this detection. Heuristic system requires confirmation from other detection mechanism to reach adequate precision. Without it, the Defender can flag normal programs, clean of any suspicious behavior or malware, as Trojan:Win32/Offloader.EA!MTB. Though, it may sometimes be tricky to understand the exact origin of the problem.
What Should I Do?
If you are sure that the alert is false, you can just ignore it. Most likely, Defender will stop detecting the file as a threat after the next database update, and the issue should resolve itself. However, I will still recommend performing a second-opinion scan with a reliable anti-malware tool like GridinSoft Anti-Malware. With its Full scan mode, you will ensure that no threats remain in the system.
As for uTorrent, I strongly recommend refraining from using it. Although it is not currently malicious, past incidents involving embedded miners in the official uTorrent client, along with its current monetization strategy, have given it a reputation as unwanted software.
Instead, consider using free open-source solutions – there are plenty of them around. The absence of ads and additional downloads significantly reduces the risk vector and avoids unnecessary hardware load.