If you’re seeing Trojan:Win32/Cerber detected by your antivirus, don’t panic. Your computer might be running slow. You might notice suspicious processes or unusual network activity. Some variants can encrypt files and demand payment.
This guide will help you remove this malware completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with methods you can try right now.
| Detection Name | Trojan:Win32/Cerber |
| Threat Type | Multi-variant malware family (Ransomware, Trojans, Backdoors) |
| First Seen | 2016 (Original Cerber family) |
| Affected Systems | Windows 7, 8, 10, 11 (32-bit and 64-bit) |
| Primary Function | File encryption, data theft, system compromise, backdoor installation |
| File Extensions | .cerber, .ba99, .98a0, .a37b, .a563, .beef (ransomware variants) |
| Distribution Methods | Phishing emails, exploit kits, malicious attachments, pirated software, drive-by downloads |
| Common Symptoms | Slow system performance, encrypted files, unusual network traffic, unknown processes |
| Persistence Methods | Registry modifications, scheduled tasks, startup entries, service installation |
| Typical File Locations | %TEMP%, %APPDATA%, %PROGRAMDATA%, System32 folder |
| Risk Level | High – Can permanently encrypt files, steal data, install backdoors |
What is Trojan:Win32/Cerber?
Trojan:Win32/Cerber is Microsoft Defender’s detection name for ransomware threats. The original Cerber ransomware appeared in 2016. It quickly became one of the most dangerous ransomware families targeting both individuals and corporations.
Today, Microsoft uses this detection name for similar ransomware samples. These threats encrypt your files and demand payment. They often target businesses but can harm anyone.
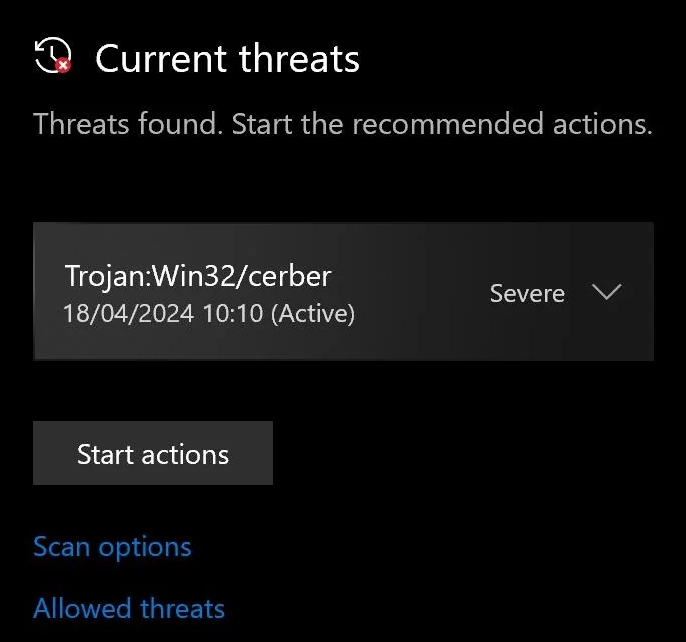
The original Cerber ransomware stopped operating in 2018. But criminals continue creating similar threats. These new variants share code similarities with the original. They use the same basic tactics to encrypt files and extort money.
How Cerber Spreads
This malware spreads through several methods:
- Phishing emails – Fake messages with infected attachments
- Pirated software – Cracked games and illegal programs often contain malware
- Malicious websites – Fake ads and compromised sites can trigger downloads
- Exploit kits – Automated tools that target browser vulnerabilities
Cerber’s Unique Features
This ransomware has some unusual characteristics. After encrypting your files, it creates multiple ransom notes in each folder. You’ll find files named “#DECRYPT MY FILES#.txt”, “#DECRYPT MY FILES#.html”, and “#DECRYPT MY FILES#.vbs”.
The .vbs file is particularly noteworthy. When executed, it uses text-to-speech to announce:
“Attention. Attention. Attention. Your documents, photos, databases and other important files have been encrypted!”
This voice notification makes the attack more intimidating. It’s designed to pressure victims into paying quickly.
Manual Removal Steps
Manual removal is challenging but possible if you act quickly. These steps work best if you catch the infection early. Important: Backup any unencrypted files before starting.
Step 1: Preparation and Safety
Start by disconnecting from the internet. This prevents the malware from communicating with its command servers. It also stops further damage to your files.
- Disconnect your network cable or disable Wi-Fi
- Boot into Safe Mode by pressing Windows + R, typing “msconfig”, and selecting Safe Boot
- Restart your computer
- Create a backup of important unencrypted files to an external drive
Step 2: Identify Malicious Processes
Cerber ransomware runs specific processes on your system. You need to identify and terminate these before removing files.
- Press Ctrl + Shift + Esc to open Task Manager
- Click the “Processes” tab
- Look for suspicious processes with random names or high CPU usage
- Common Cerber process names include random combinations like “Ahpdate.exe”
- Right-click suspicious processes and select “End Task”
- Note the file location before terminating
Step 3: Delete Malicious Files
Cerber typically places files in temporary folders. These locations are common hiding spots for trojan malware.
- Open Windows Explorer and navigate to these folders:
- C:\Users\[Username]\AppData\Local\Temp\
- C:\Windows\Temp\
- C:\ProgramData\
- Look for recently created executable files with random names
- Delete any suspicious files you identified in Step 2
- Empty the Recycle Bin completely
Step 4: Clean Startup Programs
Ransomware often adds itself to startup programs. This ensures it runs every time you boot Windows.
- Press Windows + R and type “shell:startup”
- Delete any suspicious shortcuts in the Startup folder
- Press Windows + R and type “regedit”
- Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Look for entries with random names or unfamiliar file paths
- Right-click and delete suspicious entries
Step 5: Registry Cleanup
Cerber modifies Windows registry to maintain persistence. You need to remove these changes manually.
- Open Registry Editor (regedit) as administrator
- Check these registry locations:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ActiveComputerName
- Delete any entries that reference the malicious files you found earlier
- Be extremely careful – wrong changes can break Windows
Step 6: Check Scheduled Tasks
Advanced ransomware uses Windows Task Scheduler to maintain persistence.
- Press Windows + R and type “taskschd.msc”
- Open Task Scheduler
- Click “Task Scheduler Library” in the left panel
- Look for recently created tasks with random names
- Right-click suspicious tasks and select “Delete”
- Check the Actions tab to see what files the task would execute
Step 7: Restore Shadow Copies
Cerber deletes Windows shadow copies to prevent file recovery. You might be able to restore some files if the deletion wasn’t complete.
- Right-click on an encrypted file
- Select “Properties” then “Previous Versions”
- Look for available restore points before the infection
- Select a version and click “Restore”
- This only works if shadow copies still exist
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of ransomware threats. Professional anti-malware software can find hidden components and registry changes that you might miss.
The automated approach is safer for most users. It reduces the risk of accidentally damaging your system. You also get real-time protection against future infections.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
Ransomware often comes through browser exploits. Clean your browsers to prevent reinfection.
Remove Malicious Browser Extensions
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based infection sources, reset your browser completely:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
- Tap Reset settings.
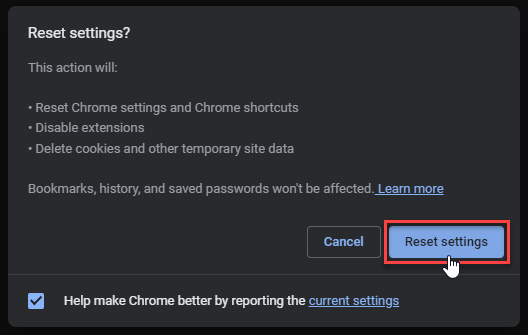
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
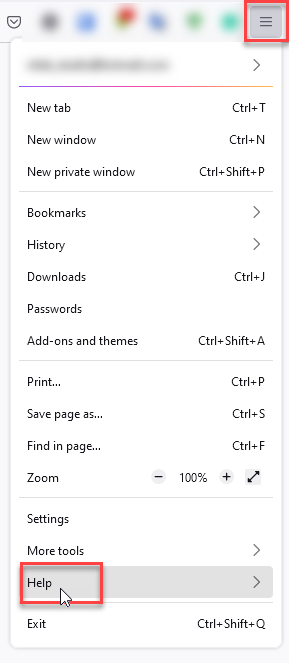
- Choose More Troubleshooting Information.
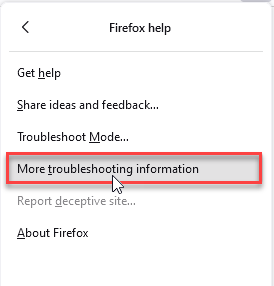
- Choose Refresh Firefox… then Refresh Firefox.
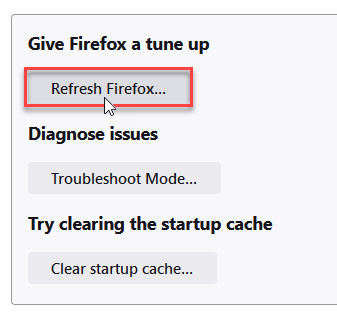
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
Technical Analysis
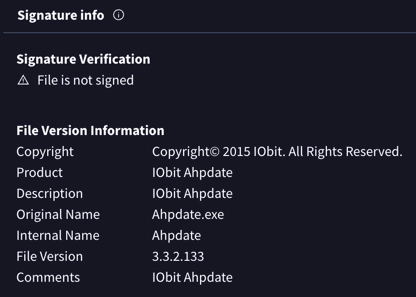
Let’s examine how Trojan:Win32/Cerber behaves using a real-world example. As a sample, let’s take one representative of this malware family. This file masquerades as an IObit utility. It even has all the file data rows filled with correct information.
Upon infiltrating the system, the malware performs specific checks. It ensures it’s not running in a virtual environment. The next step involves checking the location of the current system to avoid infecting specific regions.
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ActiveComputerName
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\WMIC.exe
\REGISTRY\MACHINE\Software\Policies\Microsoft\Windows\System
To place its files, Cerber Trojan uses system temporary folders. It particularly targets AppData\Local\Temp. Upon execution, the malware creates its copy in the said folder. It directs all the persistence hooks towards this file. Then, the original sample deletes itself, covering the tracks. It requests the system reboot.
Execution Process
After conducting its checks, the malware begins its primary task: encrypting data. It utilizes legitimate Windows tools like the command prompt to automate actions and conceal traces.
C:\Users\<USER>\AppData\Local\Temp\Ahpdate.exe
C:\Windows\System32\taskkill.exe
C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost
C:\Windows\system32\svchost.exe -k DcomLaunch -p
C:\Windows\System32\schtasks.exe
The first command executes the executable file located in the temporary folder. Then, there are system commands aimed at terminating active processes. This includes antivirus software. The malware adds itself to the Windows scheduler and initiates certain functions.
Like any ransomware, Cerber invariably deletes shadow copies. This maximizes the difficulty of file restoration. To achieve this, the malware executes the following commands:
IWbemServices::ExecQuery - ROOT\CIMV2 : SELECT * FROM Win32_ShadowCopy
C:\Windows\System32\svchost.exe -k swprv
C:\Windows\system32\vssvc.exe
C:\Windows\system32\wbem\wmic.exe shadowcopy delete
In short, Cerber requests access to all objects from the Win32_ShadowCopy class. This gives information about all existing shadow copies. Then it proceeds to delete them all.
Is Trojan:Win32/Cerber a False Positive?
In most cases, such detections are accurate. But there are rare instances when Trojan:Win32/Cerber may be a false positive. This flag sometimes appears for game files installed via Steam or other official platforms.
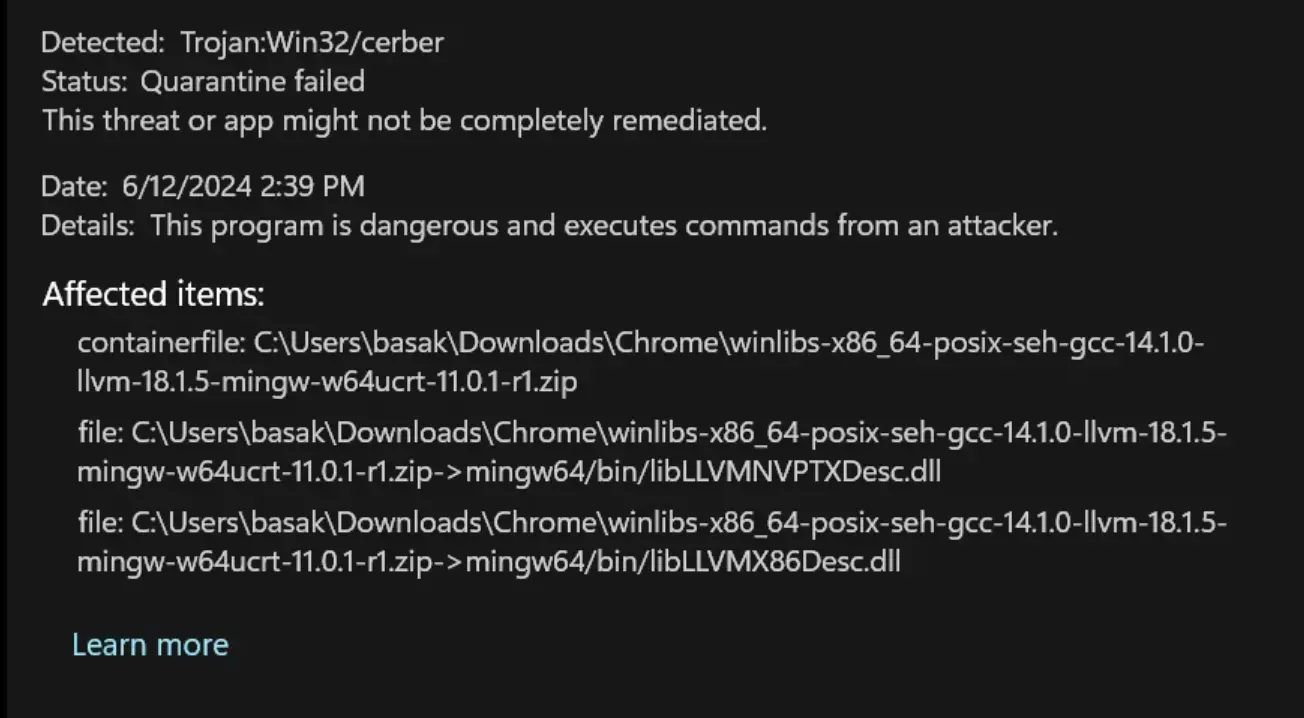
It may happen because the endpoint code of the file coincides with typical virus endpoints. Typically, when this happens with a legitimate file, updating the signature databases resolves the issue. Heuristic detection methods sometimes trigger false alarms.
However, for mods, add-ons, and game hacks, the situation is different. The likelihood of getting actual Trojan:Win32/Cerber is much higher. While the first two options are developed by third-party developers, the last one is generally illegal. Embedding malware into hacks, cheats, and game cracks is common practice among criminals.
Prevention
Preventing ransomware infection is easier than removing it. Here are essential steps to protect your system:
Safe Browsing Habits
- Avoid downloading software from unofficial sources
- Be cautious with email attachments from unknown senders
- Don’t click suspicious links or ads
- Keep your browser updated with latest security patches
System Security
- Enable Windows Update automatic installation
- Use reputable antivirus software with real-time protection
- Enable Windows Firewall or use a third-party firewall
- Avoid using administrator accounts for daily activities
Backup Strategy
- Create regular backups of important files
- Store backups on external drives disconnected from the network
- Test backup restoration periodically
- Consider cloud backup services for additional protection
Software Management
Avoid pirated software and illegal downloads. These are common sources of ransomware infections. Stick to official software sources and legitimate purchases.
Frequently Asked Questions
What is Trojan:Win32/Cerber and why is it dangerous?
Trojan:Win32/Cerber is Microsoft’s detection name for ransomware that encrypts your files and demands payment. It’s dangerous because it can permanently lock access to your personal documents, photos, and other important data. The original Cerber ransomware was one of the most active threats from 2016-2018.
How did Trojan:Win32/Cerber get on my computer?
This malware typically spreads through phishing emails with infected attachments, malicious downloads from unofficial websites, or bundled with pirated software. It can also come from compromised websites that exploit browser vulnerabilities.
Can I remove Trojan:Win32/Cerber manually?
Yes, manual removal is possible if you follow the steps in this guide carefully. However, it requires technical knowledge and can be risky. Automatic removal with professional anti-malware software is safer and more reliable for most users.
Is it safe to delete processes flagged as Trojan:Win32/Cerber?
Only terminate processes you’re certain are malicious. Make note of the process name and file location first. If you’re unsure, use automated removal tools instead. Ending legitimate system processes can cause Windows to malfunction.
How can I prevent Trojan:Win32/Cerber infections?
Keep your system updated, use reputable antivirus software, avoid downloading from unofficial sources, and be cautious with email attachments. Regular backups are crucial – they allow you to restore files without paying ransom if infection occurs.
What if manual removal doesn’t work?
If manual removal fails or you’re uncomfortable with the technical steps, use GridinSoft Anti-Malware for automatic detection and removal. Professional tools can find hidden components and clean registry entries that manual methods might miss.
Can I recover encrypted files without paying the ransom?
Sometimes you can restore files from Windows shadow copies or backups created before the infection. However, modern ransomware often deletes these recovery options. This is why prevention and regular backups are so important.
Are fake virus alerts related to Trojan:Win32/Cerber?
Some fake virus alerts may claim to detect Cerber to scare users. Always verify detections through your installed antivirus software rather than trusting pop-up warnings from websites or unknown programs.
- Trojan:Win32/Cerber is a ransomware detection that encrypts files
- It spreads through phishing emails and pirated software
- Manual removal requires technical skills and multiple steps
- Automated removal is safer and more reliable
- Prevention through backups and safe browsing is essential
- Ransom.Win64.Cerber.tr: 8db4a31b05dec3c5adfc4b7ede9f0d8e4e2eb384524ce829e707c9908492d355
- Ransom.Win64.Cerber.tr: 1d01fa681548912172f1c3a54513f1bdbe6fa4ce0678f9faa44424d32021bb33