Genesis Market Seized by FBI
Genesis Market, a Darknet marketplace for stolen information, was reportedly seized by…
3CX Phone System is Struck With Chain Supply Attack
3CX Phone System, a desktop app for business phone communication, fell victim…
Qakbot Malware Applies New Distribution Methods
Today there is an arms race between cybercriminals and antimalware manufacturers. While…
Spyware Attack: Red Flags You’re Dealing With Spyware
Spyware is probably one of the oldest but most dangerous types of…
Spyware vs. Stalkerware: What’s the difference?
Fraudsters develop various methods to penetrate the property of others, so there…
Signs of Identity Theft: How to Prevent It?
Identity theft is a rather unpleasant crime. Cybercriminals can not only empty…
Pegasus Spyware — The Most Dangerous Malware
Pegasus Spyware is a malicious program that is covered with multiple layers…
Top Working Antispyware Tips 2022
The user risks being compromised by using the Internet. The intruders are…
Google Report Companies Creating Mobile Spyware for Governments
Google Reveals An Italian Company to Sell Android and iOS Spyware to…
10 Signs That Your Computer Is Infected With Spyware
What Is Spyware? It is a malicious program that secretly gets installed…
The 5 Most Famous Spyware Attacks
Spyware can be called the most sophisticated malware these days. It never…
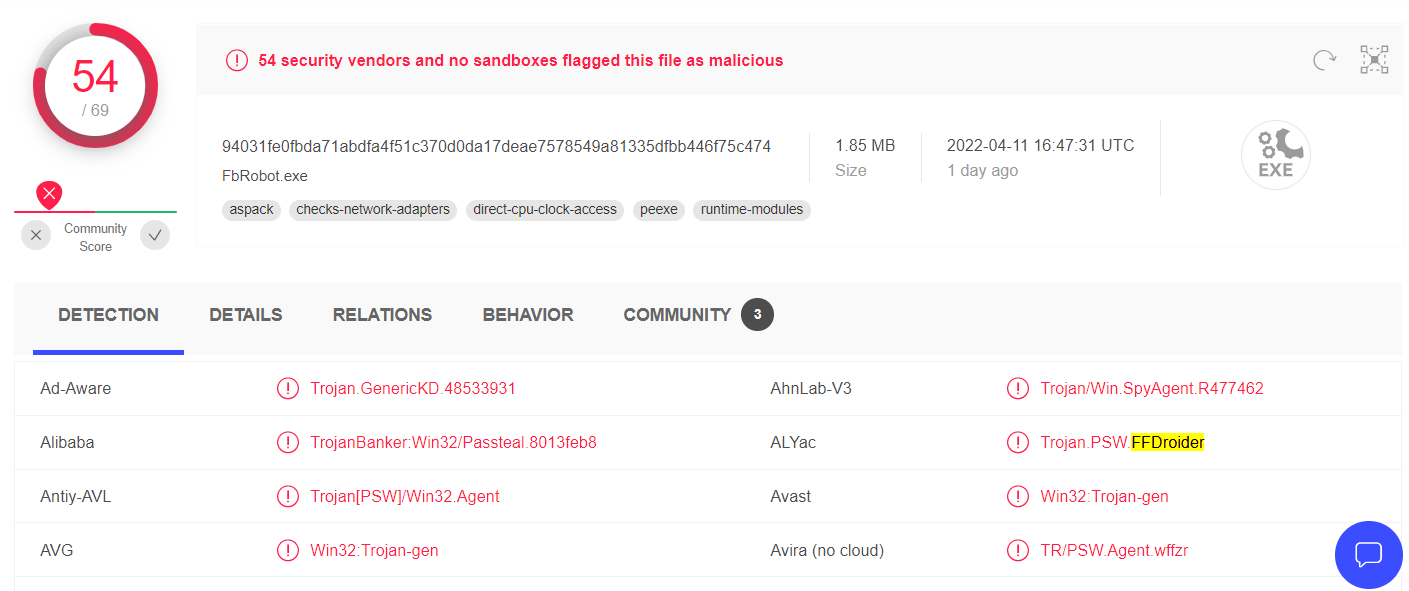
FFDroider Stealer: The New Hazard To Social Networks
FFDroider Stealer is the second malware of this type that popped out…






![Signs of Identity Theft: How to Prevent It? 12 Signs of Identity Theft: How to Prevent Identity Theft [Short Guide 2022 ]](https://gridinsoft.com/blogs/wp-content/uploads/2022/09/istockphoto-1279316333-612x612-1.jpg)