SmartTube YouTube Client Hacked: Your Ad-Free TV App Just Became a Botnet
Using SmartTube on your Android TV to escape YouTube's aggressive ads? Bad…
ClickFix Gets Creative: Abusing a 1971 Protocol to Deliver Malware
ClickFix is so widespread these days that you can find the most…
The Chronicles of ClickFix: 2025’s Biggest Hit Keeps Evolving
Meet ClickFix, the social engineering attack that's become the cybercriminal's golden ticket…
PROMPTFLUX: AI Malware Using Gemini for Self-Modification
Malware that rewrites itself on the fly, like a shape-shifting villain in…
How to Remove Trojan:Win32/Agent from Windows 11
If you're seeing Trojan:Win32/Agent detected by your antivirus, don't panic. Your computer…
Heuristic Virus Detection: How AI-Powered Security Catches Unknown Threats
Heuristic virus detection is like having a cybersecurity detective who can spot…
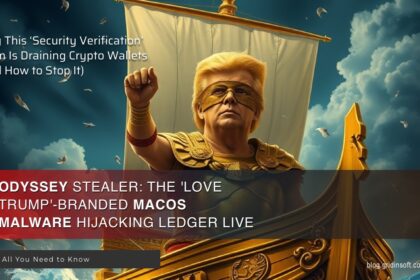
Odyssey Stealer: Russian ‘Love Trump’ Malware Replaces Ledger Live Crypto Wallet App
A new macOS malware campaign is targeting users through social engineering, masquerading…
Noodlophile Stealer: Cybercriminals Hijack AI Hype to Steal Your Data
Just when you thought cybercriminals couldn't get more creative, they've found a…
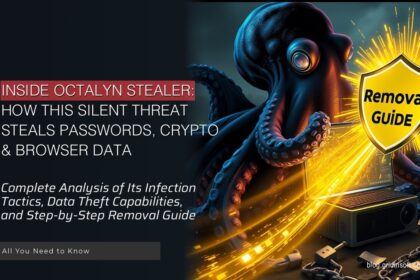
Octalyn Stealer: How This Threat Steals Passwords, Crypto & Browser Data
Octalyn Stealer is an information-stealing malware that's currently being promoted on GitHub…
MaksStealer (MaxCoffe): The Minecraft Mod That’s Actually Stealing Your Passwords
For Minecraft Gamers: MaxCoffe masquerading as a Minecraft performance enhancer! MaksStealer is…
Almoristics Application: What It Is & How to Remove Virus Miner
Almoristics Application is a devious crypto miner that's causing headaches for countless…
Virus:Win32/Expiro: The Chameleon Backdoor That’s Still Causing Havoc in 2025
Have you ever noticed your computer suddenly running like it's wading through…