The Security Blog From Gridinsoft
Capita Hacked, Black Basta Gang Publishes Data
Capita, a London-based international business process outsourcing company, was hacked recently. Users noticed strange events in the company earlier this…
Medusa Groups Claims That It “Merged” the Source Code of Bing and Cortana into the Network
Medusa extortionist group claims to have published internal materials stolen from Microsoft, including the source codes of Bing, Bing Maps…
Chinese Hackers Use Google Command & Control Capabilities in Attacks
Google experts have warned that the Chinese “government” hack group APT41 is abusing the red team’s GC2 (Google Command and…
Legion Hacker Tool Used to Steal Data from Poorly Protected Websites
Experts have discovered a Python-based Legion hacking tool that is sold via Telegram and is used as a way to…
LockBit Releases World’s First macOS Ransomware
LockBit, an infamous ransomware gang that became a major threat actor over the last two years, released the variant of…
Twitter and Graphika neutralized Dracula propaganda botnet
Experts from the Graphika research group talked about how they…
Hackers use in attacks malicious plugin for 3Ds Max
Bitdefender experts have discovered a hacker group that is attacking…
SpiKey technique allows opening the lock by recording a sound of a turning key
Scientists from the National University of Singapore have published a…
Ukrainian cyber police in cooperation with Binance detained operators of 20 cryptocurrency exchangers
Since January 2020, the Ukrainian cyber police began cooperating with…
Microsoft developers will stop supporting classic Edge and IE 11
Microsoft said it would stop supporting classic Edge and IE…
Vulnerabilities in Amazon Alexa opened access to user data for outsiders
In June this year, researchers from Check Point discovered a…
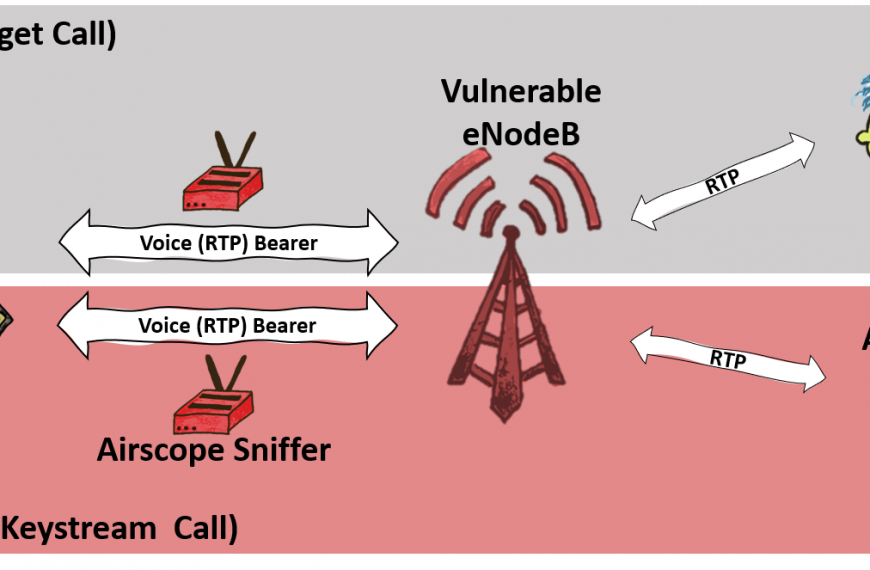
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…
Mozilla Downsizing Affects Security Professionals
Earlier this week, Mozilla fired 250 employees, and another 60…
Citrix expects attacks on fresh issues in XenMobile
Citrix engineers released a number of Citrix Endpoint Management patches…
HIBP (Have I Been Pwned?) leak aggregator opens the source code
Founder of Have I Been Pwned? (HIBP) Troy Hunt announced…
Kr00k problem threatens devices with Qualcomm and MediaTek Wi-Fi chips
In early 2020, ESET experts spoke about the Kr00k vulnerability…
Intel investigates data leak: 20 GB of source codes and documents
Swiss programmer Till Kottmann has been studying various dumps in…