The Security Blog From Gridinsoft
Rorschach Ransomware Analysis
Recent research from the CheckPoint Research team revealed a new ransomware sample that can potentially beat all samples currently present…
Rorschach’s New Ransomware Is Named the Fastest to Date
Check Point analysts have discovered a new ransomware, Rorschach ransomware that has already been used to attack an unnamed American…
SFX Archives Can Sneakily Launch PowerShell
CrowdStrike warns that hackers are adding malicious functionality to self-extracting SFX archives containing harmless honeypot files that can launch PowerShell.…
Genesis Market Seized by FBI
Genesis Market, a Darknet marketplace for stolen information, was reportedly seized by the FBI on Tuesday, April 4, 2023. The…
Blogger Forced ChatGPT to Generate Keys for Windows 95
YouTube user Enderman demonstrated that he was able to force ChatGPT to generate activation keys for Windows 95. Let me…
Vulnerabilities in Amazon Alexa opened access to user data for outsiders
In June this year, researchers from Check Point discovered a…
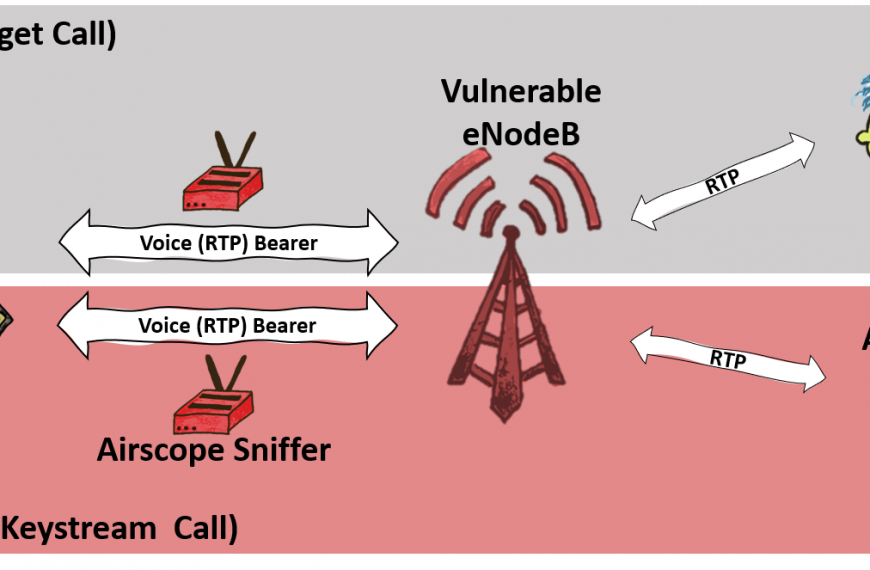
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…
Mozilla Downsizing Affects Security Professionals
Earlier this week, Mozilla fired 250 employees, and another 60…
Citrix expects attacks on fresh issues in XenMobile
Citrix engineers released a number of Citrix Endpoint Management patches…
HIBP (Have I Been Pwned?) leak aggregator opens the source code
Founder of Have I Been Pwned? (HIBP) Troy Hunt announced…
Kr00k problem threatens devices with Qualcomm and MediaTek Wi-Fi chips
In early 2020, ESET experts spoke about the Kr00k vulnerability…
Intel investigates data leak: 20 GB of source codes and documents
Swiss programmer Till Kottmann has been studying various dumps in…
US authorities offered $10000000 for information on planned cyberattacks for the elections
Less than 100 days are left before the start of…
295 Chrome extensions injected ads in search results
AdGuard analysts have identified 295 malicious extensions in the Chrome…
Google: 11 0-day vulnerabilities identified in the first half of 2020
Google Project Zero experts estimate that 11 0-day vulnerabilities, actively…
Media Reports that Garmin Paid Ransom to WastedLocker Malware Operators
In July 2020, Garmin, the manufacturer of wearable electronics and…
Attacks on EMV cards, which were only a theory for 12 years, noticed in reality
Experts from the Gemini Advisory company published a report, according…