The Security Blog From Gridinsoft
Top Maine Lobster Scam on Facebook
Another fraudulent scheme related to the sale of seafood has appeared on Facebook. Fraudsters promise lobster at an excellent price,…
Boeing Hack Confirmed, LockBit Group Resposible
Boeing, a major aircraft manufacturer and aerospace & defence contractor in the US, has confirmed the ransomware attack. A week…
Malicious WhatsApp Mods Spread Through Telegram
Some WhatsApp mods, which are unofficial versions of the app, have been found to contain hidden spyware. This spyware is…
New F5 BIG-IP Vulnerabilities Exploited In The Wild
Two new vulnerabilities in F5 BIG-IP reportedly allow for remote code execution and SQL injection. The company explains it as…
WeChat and Kaspersky Ban in Canada – What You Should Know?
The Canadian government has instituted a ban on the use of WeChat and Kaspersky applications on government-issued mobile devices, effective…
Shuckworm hackers attack Ukrainian organizations with new variant of Pteredo backdoor
Specialists from the cybersecurity company Symantec reported attacks by the…
PRODAFT Published PYSA Ransomware Report
Recently specialists from PRODAFT (Proactive Defense Against Future Threats) published…
Nation-State Threat Actors are an Actual Menace, According to CISA
On April 13, the US government (specifically, the Department of…
Experts Analyzed the Activities of the PYSA Cyber-Extortion Group
Specialists from the Swiss cybersecurity company PRODAFT have published the…
RuRansom Malware Destroys Data in Russian Systems
VMware specialists spoke about the activity of the RuRansom wiper,…
Anonymous hackers published the mail database of the Ministry of Culture of Russia
The media discovered that Anonymous hackers had made public a…
The US won’t cooperate with Russia on ransomware anymore
The US suspends its cooperation with Russia on ransomware criminals…
RaidForums shutdown as the result of Operation Tourniquet
The chain of international law enforcement agencies – Europol, FBI,…
Law enforcement officers closed the hacker resource RaidForums
During the international operation TOURNIQUET, which was coordinated by Europol,…
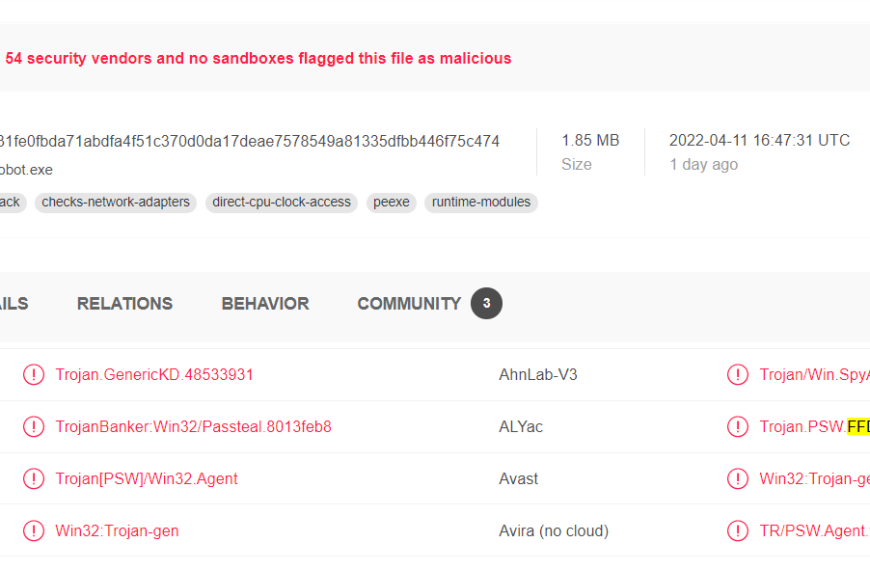
FFDroider Stealer: The New Hazard To Social Networks
FFDroider Stealer is the second malware of this type that…
Meta Infostealer Malware Spread via Spam
Meta, a newly crafted information-stealing malware, is distributed via a…
Leaked Conti ransomware source codes were used to attack Russian authorities
In March 2022, the source codes of the Conti malware…