The Security Blog From Gridinsoft
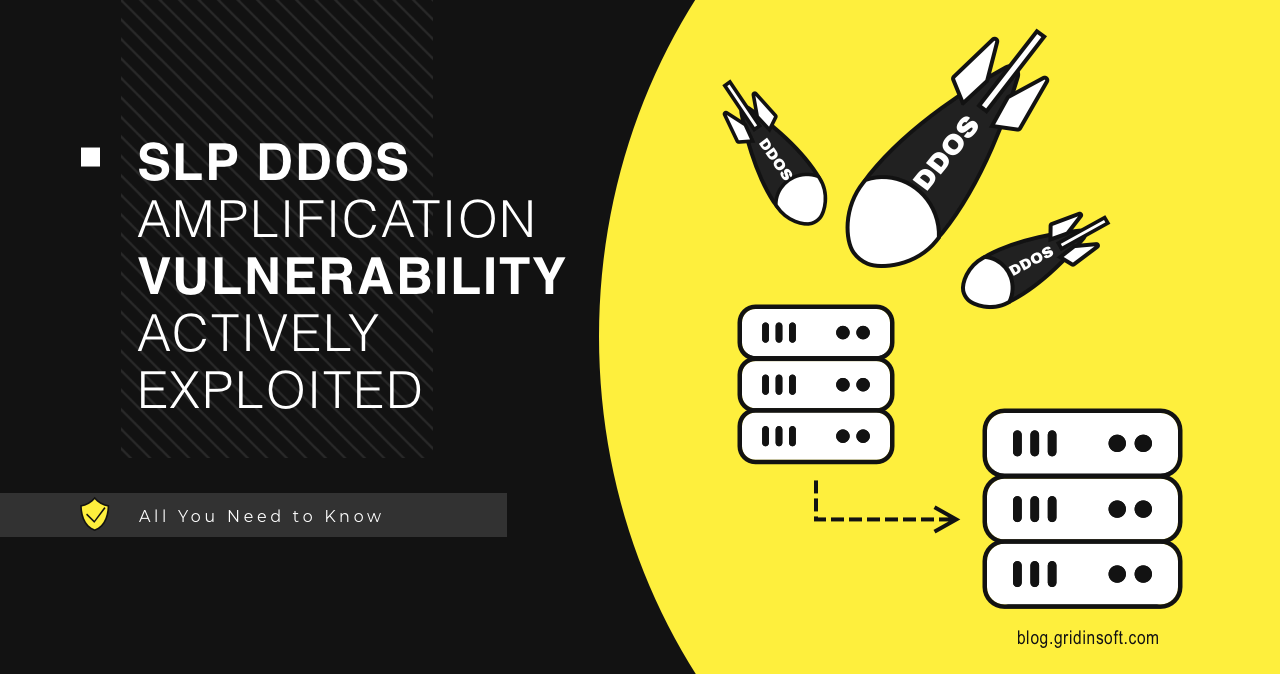
SLP DDoS Amplification Vulnerability Actively Exploited
In a recent development, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has raised alarms over an actively exploited high-severity…
SecuriDropper Bypasses Google Play & Android Defenses
SecuriDropper is a rare example of the Android dropper malware that operates under the dropper-as-a-service (DaaS) model. This malware is…
North Korean Hackers Force US, Japan & South Korea Consultations
Increased activity by North Korean state hackers forced South Korea, the United States and Japan to create a special advisory…
Socks5Systemz Proxy Service Infects 10,000 Systems Worldwide
A proxy botnet, “Socks5Systemz”, uses malware loaders to infiltrate computers across the globe. Attackers have infected about 10,000 devices and…
Top Maine Lobster Scam on Facebook
Another fraudulent scheme related to the sale of seafood has appeared on Facebook. Fraudsters promise lobster at an excellent price,…
Experts analysed the conversations of Conti and Hive ransomware groups
Analysis of more than 40 chats with victims allowed the…
Ukraine Was Hit by DDoS Attacks from Hacked WordPress Sites
Ukrainian Computer Emergency Response Team (CERT-UA) said that Ukraine was…
Stabbed in the back: Chinese Mustang Panda Cyberspies Attack Russian Officials
Secureworks researchers have discovered a phishing campaign by Chinese Mustang…
20 Dangerous Types of Cybersecurity Threats
The cybersecurity threats in this year are more considerable than…
Vulnerabilities in Linux Allow Gaining Superuser Rights
A Microsoft specialist has discovered vulnerabilities in Linux systems, the…
State Department Offers $1 million for Info on Russian Hackers
The US State Department has announced a reward amounting up…
Emotet Malware Operators Found a Bug in Their Bootloader
Emotet malware operators have fixed a bug due to which,…
T-Mobile Admits that Lapsus$ Hack Group Stole Its Source Codes
Information security specialist Brian Krebs found out that even before…
Amazon Patch for Log4Shell allowed privilege escalation
Palo Alto Networks warns that a patch released by Amazon…
Hackers Use Fresh Vulnerability in Windows Print Spooler in Real Attacks
The US Infrastructure and Cybersecurity Agency (CISA) warned that a…
TOP 9 Malware Attacks: Compilation 2022
The World Wide Web is not a hostile realm by…
Shuckworm hackers attack Ukrainian organizations with new variant of Pteredo backdoor
Specialists from the cybersecurity company Symantec reported attacks by the…