The Security Blog From Gridinsoft
New Mirai Based Botnet Exploits Four-Faith Vulnerability
Researchers detected another IoT botnet based off of Mirai malware source code, that now leverages a newly-discovered vulnerability in Four-Faith…
25 Chrome Extensions Compromised, Exposing 2M+ Users
A targeted attack on Chrome extensions publishers compromised the add-ons uploaded to Chrome Web Store, leading to a potential compromise…
Apache Traffic Control Critical SQLi Vulnerability Fixed
Apache Traffic Control platform got a critical security patch that addresses a major vulnerability that could let attackers execute arbitrary…
Lockbit 4.0 Released, With New Infrastructure and Features
Lockbit ransomware group steps up with a new version of its malicious software, LockBit 4.0, and with adjustments to their…
LockBit Ransomware Developer Arrested and Extradicted in Israel
US authorities have detained a developer associated with the LockBit group, one of the most active ransomware creators. Investigators allege…
Binance Smart Contracts Blockchain Abused in Malware Spreading
Cybercriminals appear to exploit Binance smart contracts as intermediary C2,…
Kaspersky Antivirus Banned By the Biden Administration
On June 20, 2024, the Biden administration implemented a complete…
Win.MxResIcn.Heur.Gen
Antivirus engine of MaxSecure, a well-known cybersecurity vendor, currently shows…
Lumma Stealer Spreads Via Fake Browser Updates, Uses ClearFake
Recent research uncovered a selection of websites that deploy Lumma…
Microsoft Patches Critical MSMQ Vulnerability
In the latest Patch Tuesday, on June 11, 2024 Microsoft…
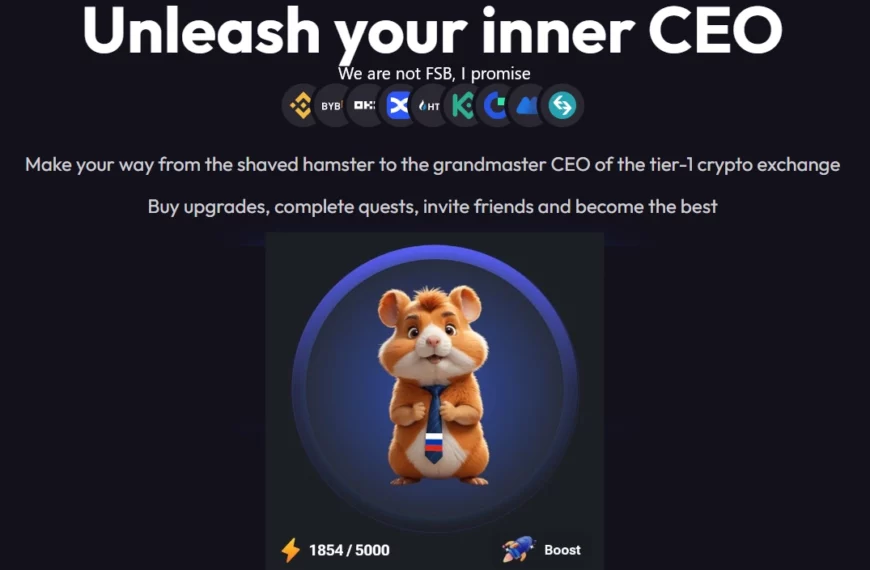
Hamster Kombat Game Rises Concern Over Russian Origins
Hamster Kombat, a recently released tap game in Telegram Messenger,…
New Embargo Ransomware Discovered, Possible ALPHV Reborn
A new strain of ransomware, named Embargo, written in Rust,…
GitHub Enterprise Server Auth Bypass Flaw Discovered
On May 21, 2024 GitHub disclosed a new authentication bypass…
Zabbix SQLi Vulnerability Leads to RCE, Latest Versions Affected
Zabbix, a network monitoring tool widely used in corporate IT…
BreachForums is Seized, Again, FBI Puts a Banner
BreachForums, one of, if not the biggest Darknet forum, is…
Dell Hacked, 49 Million Users Exposed
On Friday, May 10, Dell Technologies released a claim regarding…
LockBit Leader Identity Revealed, NCA Publishes More Data
On May 7, 2024, UK National Crime Agency published the…