File transfer utility Aspera Faspex, developed by IBM, became a riding mare of cybercriminals. A vulnerability discovered in the past year is exploited to deploy various ransomware samples. Key threat actors using that breach are IceFire, Shadowserver and Buhti. The issue allows arbitrary code execution, and touches all app versions before Faspex 4.4.2 PL2.
What is Aspera Faspex?
Aspera Faspex, or shortly Faspex, is a cloud file transfer utility that uses its own transfer protocol. The developer – Aspera – is a subsidiary of one of the oldest companies in the industry – IBM. Fast, Adaptive and Secure Protocol (FASP) allow dealing with sending large files through local and wide area networks, retaining the corresponding security level and transfer speed. Being a web-based app, it provides centralised control over the transfer policies and user accounts.
All these qualities made it popular among companies, however, IBM does not haste to uncover the numbers. It reportedly saw a wide application in media production, where the need to share large files over the network is essential. The developer releases regular patches, which, aside from new functionality, also bring bug fixes and security patches. And the latter is the most interesting point.
Faspex Breach Allows Arbitrary Code Execution
Back in December 2022, IBM spotted the possibility of exploiting the obsolete API call to circumvent the authentication and execute arbitrary code. The breach was listed as CVE-2022-47986 and patched instantly in the upcoming 4.4.2 PL2 release. It received a very high CVSS rating – 9.8. Though it is pretty common to see high ratings for vulnerabilities that allow arbitrary code execution. However, as it usually happens, the update is not getting installed instantly after its release. The vulnerable version of a program is still present on a great number of systems. And that gave crooks the opportunity to commit their dirty deeds.
Since February 13, researchers have detected several ransomware gangs actively exploiting the described vulnerability. The first one was Shadowserver, which attempts were prevented. 3 days later, on Feb 16, Buhti a.k.a BuhtiRansom succeeded in encrypting an array of vulnerable servers using CVE-2022-47986. IceFire group popped out 3 weeks later with attacks on Linux-based infrastructure through the same breach.
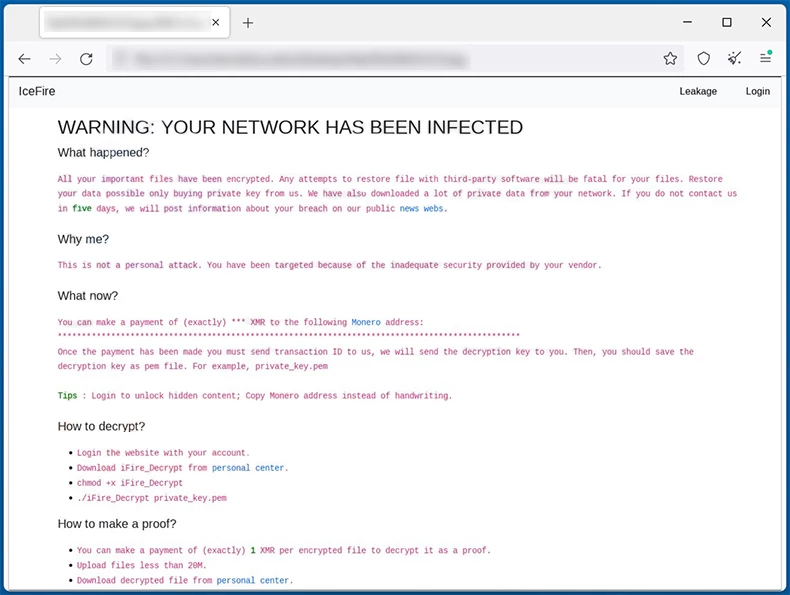
The last mentioned group is worth a separate description. Attacking targets on Linux is an unusual tactic for IceFire, as they previously aimed at Windows systems. Such a switch seems to be a new trend among ransomware gangs, as a number of other ones, such as BlackBasta, ViceSociety and Hive, added functionality to target Linux systems in 2022. That is not the only peculiarity of them – they mainly target companies in Arab countries – UAE, Iran and Pakistan. The group attacked organizations in Turkey as well. Other details, however, are less uncommon: IceFire picks large companies that will probably be able to pay off bigger ransoms.
Patch Now For Not Being Sorry Later
Attacks upon file-transferring tools seem to be another upcoming trend. Recently, the Cl0p ransomware gang was using a breach in GoAnywhere managed file transfer (MFT) tool to attack a huge number of companies. Given that the average ransom of Cl0p is just shy of $250,000, it may be painful to suffer such a loss. Needless to say that other actors may ask more – up to $50 million. Is ignoring minor patches worth it? I think the answer is “no”.
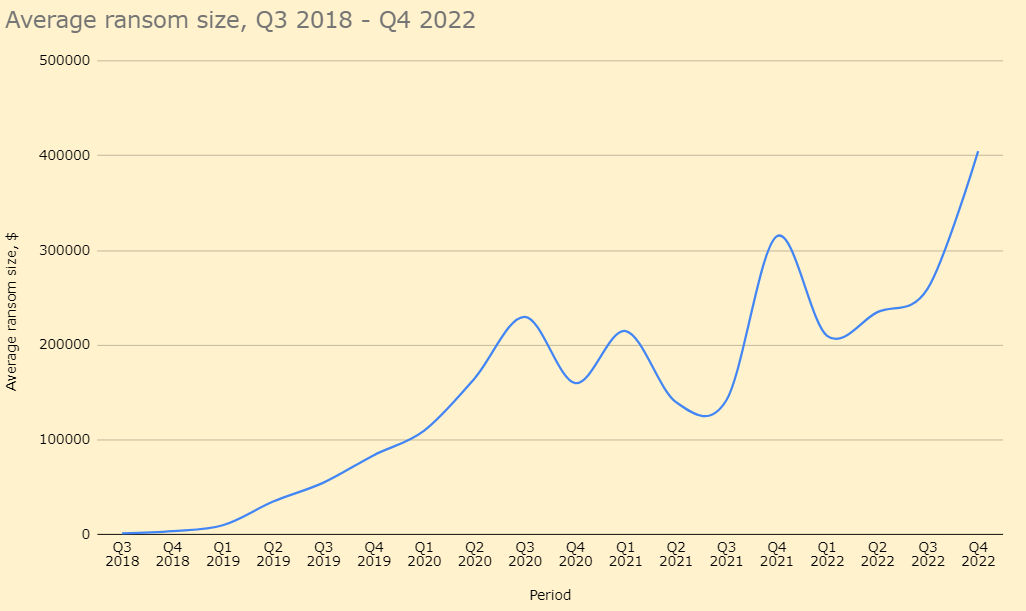
IBM did a great job at detecting and patching the breach, and all clients could receive a fix in 4.4.2 PL2 – just give it a go. The last major update – Faspex 5 – is also secured against that vulnerability. However, as practice shows, companies rarely haste to install patches: even the infamous EternalBlue vulnerability is still getting exploited in numerous attacks, almost 5 years after its detection and patching. Needless to say that less public and worldwide-threatening vulnerabilities may remain active for decades to come.




