In March 2021, researchers at the University of Louisiana at Lafayette presented a paper on a new hCaptcha bypass method that replaced reCAPTCHA in Cloudflare and Google last year. Experts have developed an attack that uses browser automation tools, image recognition, image classifiers, and machine learning algorithms to download hCaptcha tasks, recognize image content, classify images, and then solve problems.
Moreover, unlike other attacks on various CAPTCHA systems, this method does not require much computing power: the researchers’ equipment consisted of a simple Docker container running Ubuntu, with a tri-core processor and 2 GB of memory.
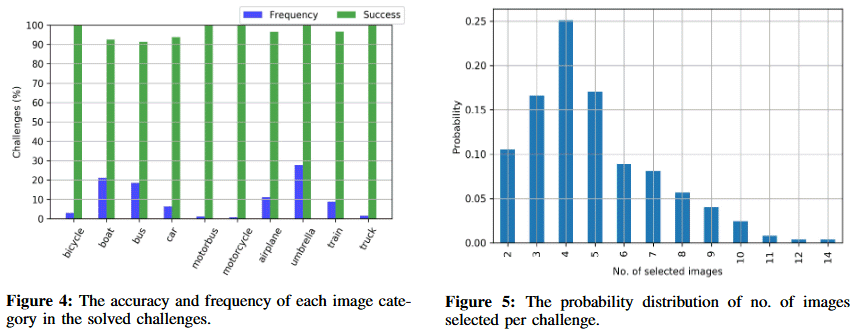
Researchers write that their attack works with an accuracy of 95.93%, and on average it takes only 18.76 seconds to crack hCaptcha. Moreover, the attack could have worked even faster if the researchers replaced their own image classifier with services such as Google Cloud Vision, Amazon Rekognition and Microsoft Azure Cognitive Vision.
The authors of the report warned that the method they developed could help attackers bypass hCaptcha on live sites and carry out automated attacks, including posting spam on forums, scraping content, and so on.
The Record turned to Cloudflare for comment as the University of Louisiana’s findings alarmed many site owners. The company said that “hCaptcha is just one of various methods Cloudflare uses to detect and potentially block automated traffic.” Cloudflare claims that they have additional systems to detect automated attacks, and there is no need to worry about a new attack method.
The developers of hCaptcha, in turn, reported that they have already implemented in their CAPTCHA methods proposed by experts to mitigate the consequences of such attacks. However, hCaptcha acknowledged that the free version does not prevent all types of automated attacks, but solely due to some design decisions.
Let me remind you that I wrote that Hackers force users to solve CAPTCHA.