PyPI, an index of Python packages, once again became a place for malware spreading. Threat actors registered hundreds of profiles to deploy packages, with the name set as typosquatting to known and popular packages. This forced the administration to halt new user registration until the issue is resolved.
PyPI Malware Spreading Causes Registrations Halt
Python Package Index, commonly known as PyPI, closes the registration of new users due to the wave of malware spreading through the platform. Such trouble is nothing new, as similar infestations happened in the past. Each time in the past the platform was implementing changes targeted on prevention of malware uploading in future, but the protection likely failed this time. The research from CheckPoint uncovers the entire flow of the attack.
Under the latest attack course, cybercriminals uploaded not the final payload, but a malicious script that further loads the malware. Exact repositories with these scripts were generally uploaded on March 27, with user accounts created the day before. Overall, the research unveils 576 malignant repositories.
Another thing that unites all these uploads is the use of typosquatting in their naming. Frauds were purportedly aiming at spoofing the names of popular packages. They particularly used symbol-numeric substitution (request5 instead of requests), popular typos (requestss) and slight changes like -sdk or -v1 endings. While looking as obvious fakes, they may still work out when users are in haste or distracted.
Package indexes for different programming languages are often a target of cybercriminals’ attention. Ones of the size of PyPI, which boasts of over 800,000 users, are literally Mekkas for hackers. By spreading malware in packages, they can infect both users and developers, potentially gaining a starting point for a cyberattack on a corporation, or even for a supply chain attack. Considering the wide use of Python in machine learning, this can also be leveraged for attacks on ML clusters. The latter appears to be a new point of interest for cybercriminals.
Malware in PyPI: How It Works?
Despite the scale of the attack, the way the attack works is nothing special. As I’ve said, malicious repositories contained not the exact malware, but an obfuscated loader script. The latter invoked the connection to the command server – funcaptcha[.]ru – and pulled the payload.
All the repos were spreading the same script, which deployed the same malware, regardless of the region. Those were an infostealer malware and a cryptojacker, both in a form of obfuscated code. None of them, however, belong to any of the known malware families, likely being developed for this specific attack campaign.
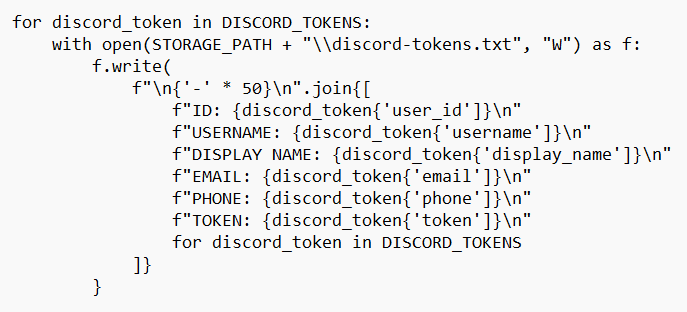
Infostealer targets passwords stored in browser files and session tokens of popular desktop applications. Additionally, it grabs browser cookies – another valuable source of user information. Cryptojacking malware modifies the desktop crypto wallets it detects, so they most likely change the recipient of all transactions to the frauds’ wallet. Following the action, both malware samples communicate the same C2 server as the loader script did.
Disclosure and Remediation
Shortly after uncovering the attack chain, PyPI administrators claimed the suspension of all new user registration. Consequently, they started searching for exact repositories and deleting them, which corresponds to the tactics they used before. Still, this does not solve the problem of exclusively reactive actions towards such threats.
Despite being well-known and trusted, all large package repositories suffer from the very same problem. It is too hard to track all the uploads, and strict premoderation will queue the new packages for weeks. The only variable here is which one will be the next to get the attention of adversaries. This eventually raises the question of self-defense from the developers who rely on these repos in daily tasks.
An obvious advice here is to double-check all the packages, regardless of their source. Malware receives more and more sophisticated disguises, becoming effective even against savvy and aware users. A good anti-malware software will be on hand as well: a proper one will easily detect and prevent the execution of a malicious script before it starts its mischievous job.





