Progress Flowmon, a popular network monitoring software solution, appears to be vulnerable to arbitrary command injection. Successful exploitation of the flaw can grant adversaries with full access to the network infrastructure, leading to catastrophic consequences. The developer already released the fix and insists on its urgent installation.
Flowmon Command Injection Flaw Threatens Network Security
The recent report from Progress company reveals a severe flaw in Flowmon, their network monitoring utility widely used in corporations. It interconnects all the network-facing assets, allowing for simultaneous monitoring and control over the environment. And, as it turns out, it is possible to surpass the authentication of this solution’s API, and execute whatever command is possible on the affected instance.
Critical vulnerability, coded as CVE-2024-2389, received the highest possible CVSS score of 10. Wide functionality it can grant to the attackers corresponds to this, as the hackers can disrupt the network, change its configuration or obtain sensitive information. Additionally, due to the high trustworthiness of Flowmon and the use of embedded commands it is particularly hard to detect the intrusion.
The issue itself stems from an issue in the mechanism of API commands authentication. A specially crafted command to the network-facing API will be executed no matter what privileges the issue has, if any at all. Deeper analysis shows that the flaw falls under the CWE-78 designation.
Overall, hacking into network infrastructure remains a key attack vector for a lot of cyberattacks. More sophisticated ones try to inject the malicious code under supply chain attack – you may have heard about the recent scandal around the backdoor in XZ Utils. At the same time, the sheer volume of vulnerabilities circulating around make it entirely possible to succeed even without that much effort.
Affected Versions and Mitigations
Progress, the developer of the solution, says that Flowmon versions before 11.1.14 and 12.3.5 are vulnerable. The said versions are the newest updates that contain the fix of this flaw. Earlier versions – 10.x and before – are not susceptible to the exploitation either.
The obvious fix here is to update the program to the latest, non-vulnerable version. Devs do not say about any mitigation – and I cannot suppose one here, except for closing the solution’s API from external access. This, however, may be problematic and will likely disrupt certain functionality.
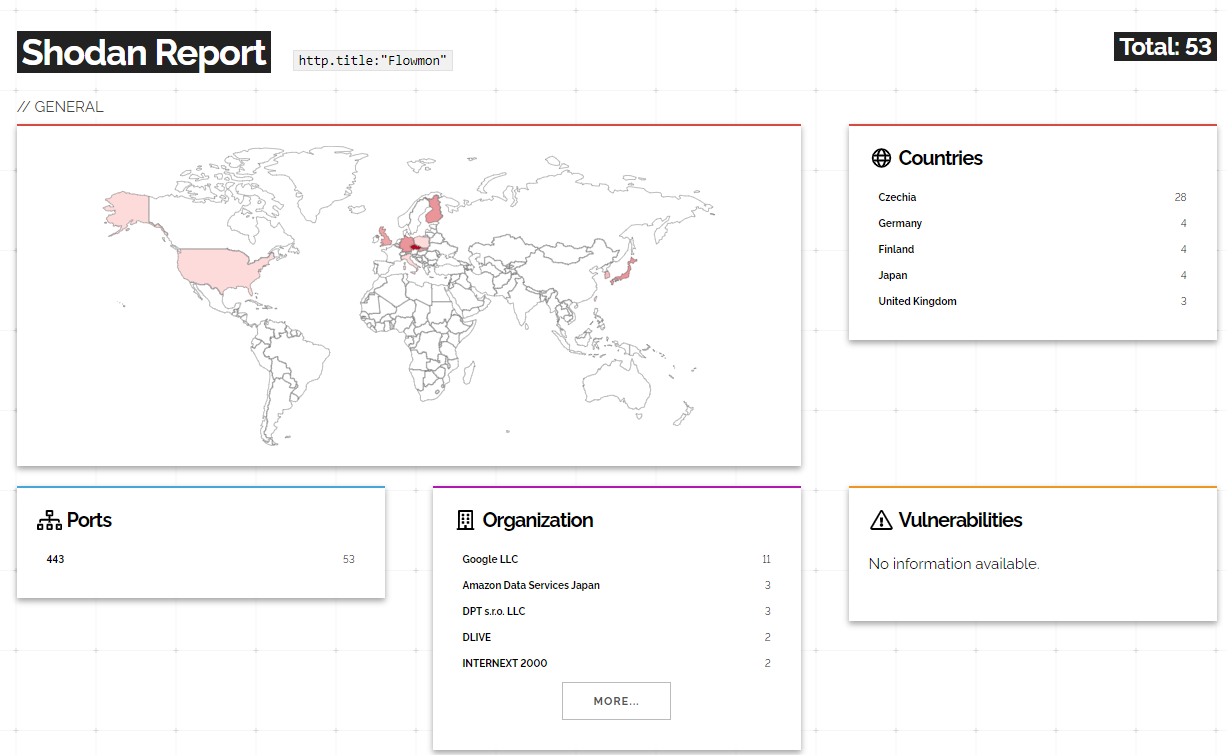
Good news here is that the vulnerability is not exploited in the wild. Progress does not haste to publish the detailed information about how and why this all works, and no PoC exploits exist so far. Network reconnaissance tools like Shodan say about only 53 vulnerable instances around the world. Though this is barely an accurate measurement, since such network monitoring tools are rarely available from the Web.
Nonetheless, ignoring the flaw because of this is not a good idea. The majority of vulnerability exploitation happens after the public disclosure of the flaw. Sooner or later, attackers will find the way to put it to use – and be sure, you will not like the consequences. The less time you give them to attack, the less likely the attack to happen.




