Password stealer is a type of data stealing malware, that aims at a specific category of information. They are often spread through phishing, malvertising, and sometimes in cracked software. Let’s have a more detailed look on how they work, and how to protect yourself against password stealers.
What Is a Password Stealer?
As its name suggests, password stealer is a type of malware that aims to steal sensitive data. Mainly, this is about credentials to email accounts, social networks, and online banking. But these days, quite a few password stealers incorporate more diverse functionality. They now target crypto wallets, cookies, browser cache and saved passwords, Discord session tokens, and more.
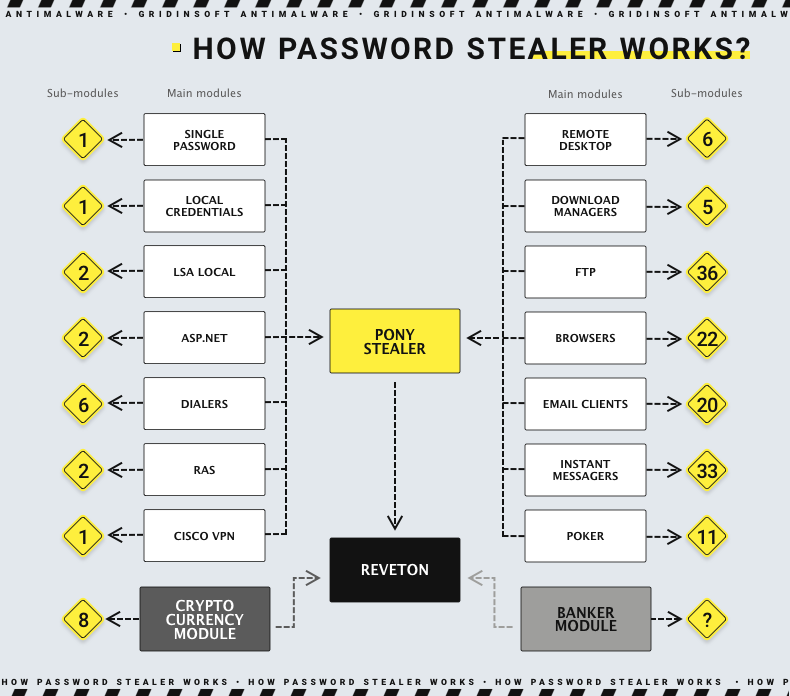
The primary distribution method of password stealers is phishing emails with malicious attachments. Sometimes, however, password stealers can also be distributed via malicious ads in search results. In a selection of cases, spear phishing was used to attack a specific person with the malware.
Technical Analysis
All stealers are generally very similar, so the properties that the current instance has to apply to the others, perhaps with minimal differences. This will be a rather simplified analysis aimed at understanding how password stealer works. I will get through the most common and important actions that this malware does. For the test sample, I’ve chosen Vidar Stealer – a classic password stealer written in C++. The attack commonly begins when the victim runs an infected file.
Defense Evasion
Like most malware, it has a few tricks that make it particularly difficult to detect on the system. When the malware comes under the guise of the installer of a legitimate program, it can contain a row of null bytes at the beginning, which pushes its size over 700 MB. This size allows it to avoid instant detection by antivirus solutions and online checkers like VirusTotal. Another trick aimed at evading detection is code obfuscation. The malware also checks system parameters to ensure it is not running in a virtualized environment. It checks values such as:
HKLM/System/Setup
HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid
These keys contain information about the system and hardware, which allows you to create a digital fingerprint of the infected system in addition to identification.
Data Collection
Once the malware is convinced that it is not running in a sandbox and has established a foothold in the system, it moves on to its primary function – information gathering. password stealer collects the following information from browsers:
C:\Users\admin\AppData\Local\Temp\History\History.IE5\index.dat
C:\Users\admin\AppData\Local\Temp\Temporary Internet Files\Content.IE5\index.dat
C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\index.dat
C:\Windows\system32\CRYPTBASE.dll
C:\Documents and Settings\
C:\Users\user\AppData\Local\Google\Chrome\User Data\
These folders contain information such as autofill, saved passwords, cookies, cache, and browser extensions. Next, stealer tries to collect crypto wallet data by checking the locations you can see below. This list includes only a few wallets, as the exact list is too long to mention.
C:\Users\user\AppData\Local\Blockstream\Green\wallets\
C:\Users\user\AppData\Local\Coinomi\Coinomi\wallets\
Data Exfiltration
The malware’s final operation step is stolen data exfiltration. To do this, password stealer communicates with C2 (Command and Control) to receive further instructions. By the way, there can be various options for communicating with C2. Attackers often still use classic C2 servers; sometimes, they use Telegram or Mastodon as intermediate servers. However, in our case, the malware uses Steam. Before sending the stolen data, stealer sends several requests, including:
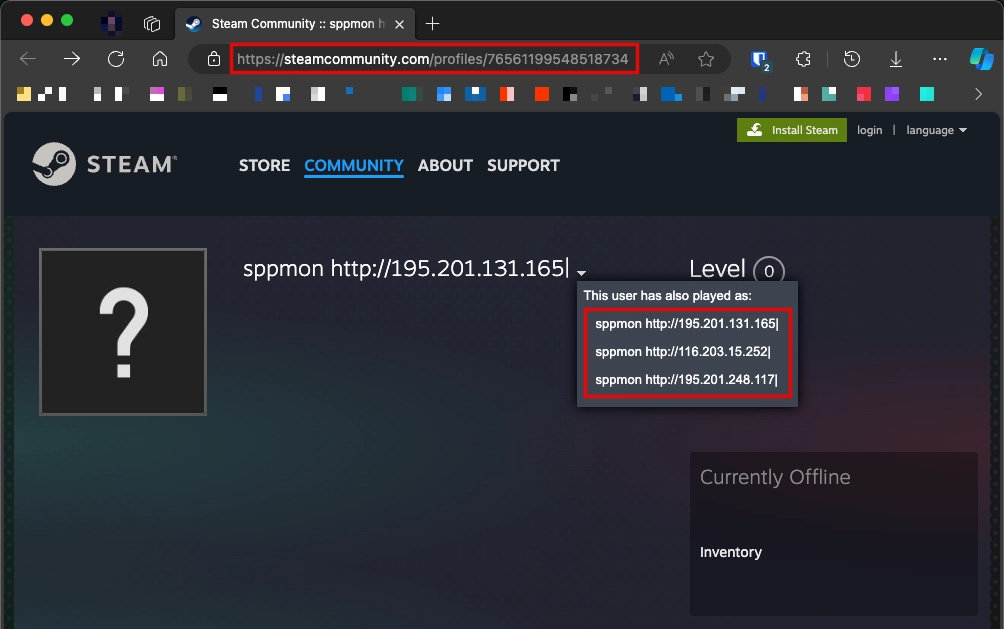
GET https://steamcommunity.com/profiles/76561199548518734 200
This is a link to a Steam profile. However, the strange name profile’s name “sppmon http://195.201.131.165|” is the command for malware. This is actually the address of the final server that the stealer should connect to. The phrase “This user has also played as” suggests that the address in the name changes quite often.
When finished, stealer self-deletes itself and covers its tracks. Though, not all infostealers do this, preferring to stay in the system even after extracting all the data. But when they do, the shell command comes in handy:
"%ComSpec%" /c taskkill /im "%SAMPLENAME%" /f & erase "%SAMPLEPATH%" & exit
Difference Between Password Stealer and Spyware
Password stealers and spyware may look similar, but have some fundamental differences. The first difference lies in the principle of operation: stealer works quietly and quickly, often sticking to “steal and leave” tactics. Spyware, on the other hand, aims at a long and permanent presence in the system. Although some stealers can take screenshots and capture keyboard inputs in addition to collecting sensitive data, this is not the main functionality.
Spyware, on the other hand, can stay on an infected system for months and continuously collect data. This includes screenshots, capturing keystrokes, and camera and microphone recordings. This data is sent periodically or in real-time to the attacker’s server.
Safety Recommendations
Malware and password stealers in particular tend to become more and more sophisticated. Getting harder to detect, picking new spreading ways, collecting more and more data – all this makes them a menace to be aware about. Fortunately, the ways to prevent this from getting into your PC is not particularly hard.
- Be careful with email attachments. This method is still the leading method among successful malware infections. Do not open attachments or click on links if the email has a suspicious sender or is not the email you were intentionally expecting.
- Avoid cracked software. Pirated software is illegal in itself, but it carries serious risks. Attackers embed malicious code in “repacks”, as installing most hacked programs requires disabling security software.
- Use security software. A reliable antimalware solution is essential because it can prevent malware from running and installing in case of user error. In addition, it will generally provide comprehensive protection by significantly reducing infection vectors. In addition, advanced solutions such as GridinSoft Anti-Malware have an Internet Security module that blocks potentially malicious sites.