Recent research uncovered a selection of websites that deploy Lumma Stealer under the guise of a browser update. They pose as tutorial pages that offer seemingly correct guides, but then open a malicious JS iframe handled with ClearFake framework. Some of these sites are active for several weeks now.
Fake Tutorial Sites Spread Lumma Stealer with ClearFake Framework
A new spreading campaign of Lumma Stealer apparently started on fake tutorial sites. Avast reports about one specific example of such a page, that uses a JS framework known as ClearFake to trick the user into running a payload. The base website, pchelperspro[.]com appears as just a page that instructs on solving an issue with Windows update, with the rest of the attack happening after spending a bit more time. Though, an attentive user will notice that the all buttons on the page are inactive, and they in fact are from a different site.
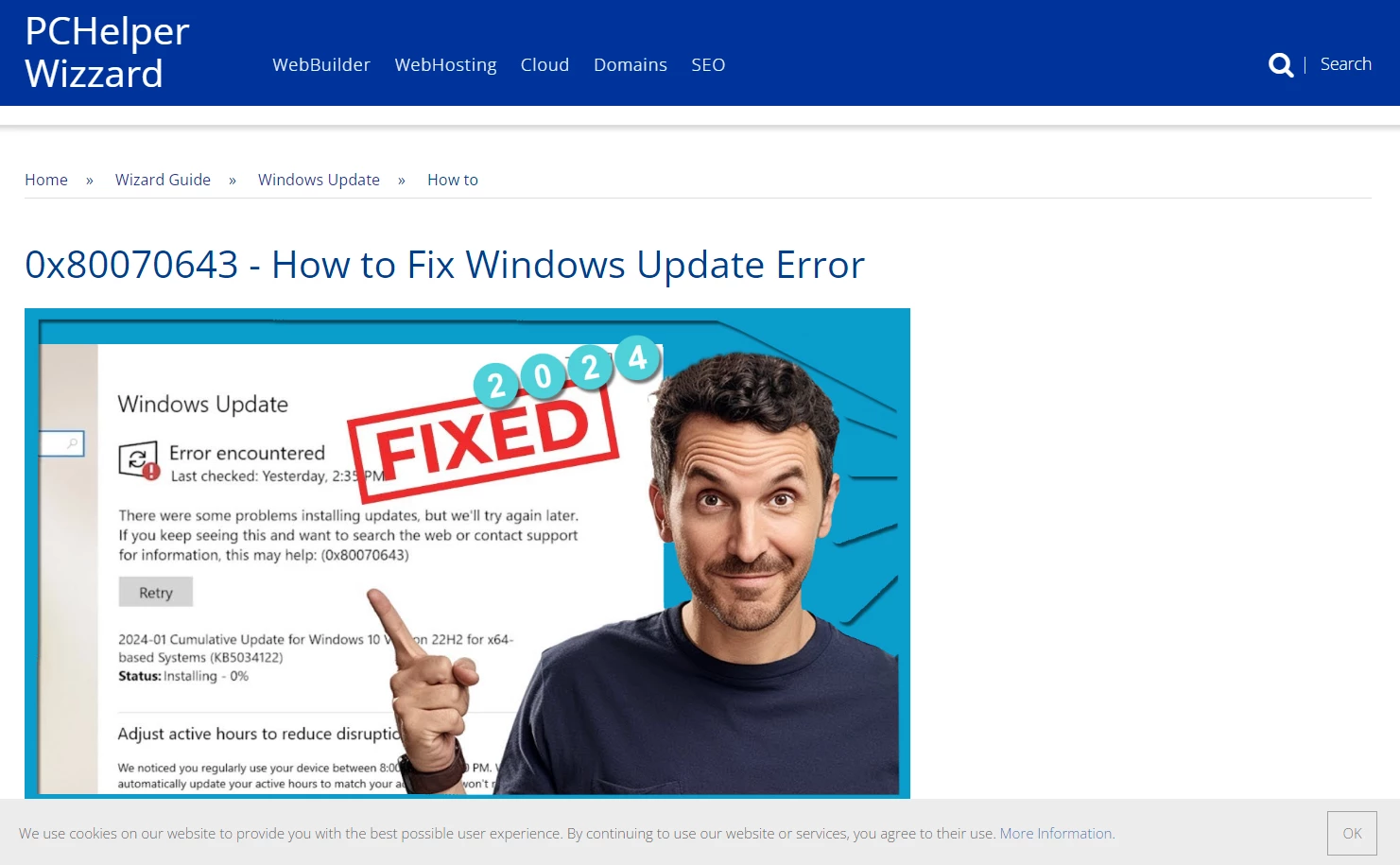
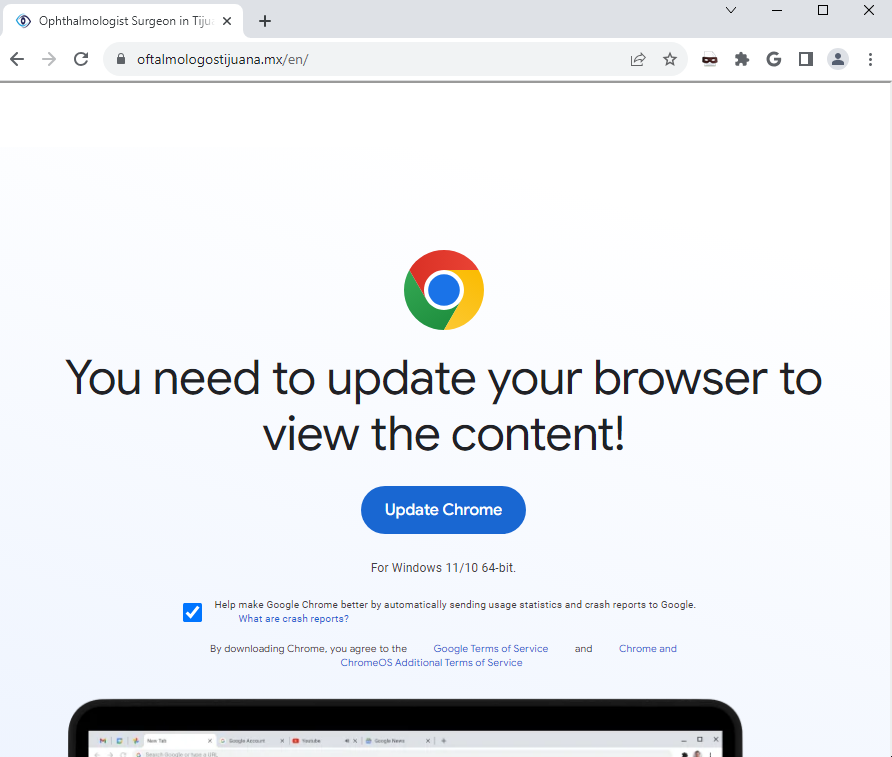
After a short timeout, the aforementioned framework kicks in, opening the fake browser update window. The way it functions, as well as the design of the fake update page, makes it particularly hard to think of it as something malicious. If, of course, you are not aware that web browsers never show such windows to begin with. Following the guidance from the fake update window makes the user download and run the malicious PowerShell script.
The PS script, in turn, connects to the command server, loads the final payload (Lumma Stealer) and executes it. Interestingly enough, the script also performs a chain of actions targeted on system fingerprinting. In particular, it performs the following queries:
C:\Windows\SysWOW64\netsh.exe
C:\Windows\system32\SecurityHealthService.exe
Addresses of command servers are encoded into the script text, and initially appear as some sketchy online shops. However, every single one was created just 20 days ago – barely a coincidence.
Innerverdanytiresw.shop
Lamentablegapingkwaq.shop
Stickyyummyskiwffe.shop
Greentastellesqwm.shop
ClearFake and Lumma Stealer Short Overview
ClearFake is a name for a JavaScript framework, that allows creating JS iframes with any needed content, circumnavigating web browser’s protective mechanisms. Originally spotted in August 2023, it was massively used in attack campaigns similar to what I’ve described above. Same as in the current campaign, it was used to display an “update your browser” page, with some additional customization depending on the browser that the victim is using. The only difference now is the use of day-timer websites instead of compromised pages, like in the original campaign.
Lumma Stealer, on the other hand, is a much more recognizable malicious program. Appeared just a year ago, in early 2023, it gained significant popularity and fame on the Darknet. Built around the principle of the least footprint, it is capable of avoiding detection from antiviruses that orient at typical activities of spyware. Combined with flexible spreading ways (YouTube promos of cracked software, spam in Discord), this pushed Lumma to its current popularity. From the perspective of functionality, it is a modular infostealer that collects passwords, session tokens, cryptowallet data, and so on.
Protect Your Network Browsing & PC Activities
Using GridinSoft Anti-Malware, you will be able to avoid shady sites and malicious frameworks before they can harm you. Its network security module will analyze the activities with multiple detection systems. Continuous database updates allow the program to have peak efficiency even against the most recent network threats. Try it out now!