Intezer analysts call the new Linux malware Lightning Framework a real “Swiss knife” because of its modular architecture, as well as the ability to install rootkits and backdoors.
Let me remind you that we also talked about New RedAlert Ransomware that Targets Windows and Linux VMware ESXi Servers, and also that Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable.
It appears that the malware has not yet been used in real attacks, but the researchers managed to study some of its components, and they say that the rest “still needs to be found and analyzed.”
It is known that the Lightning Framework has a fairly simple structure: the main loader component (kbioset), which downloads and installs other malware modules and plugins on compromised devices, including the main module (kkdmflush).
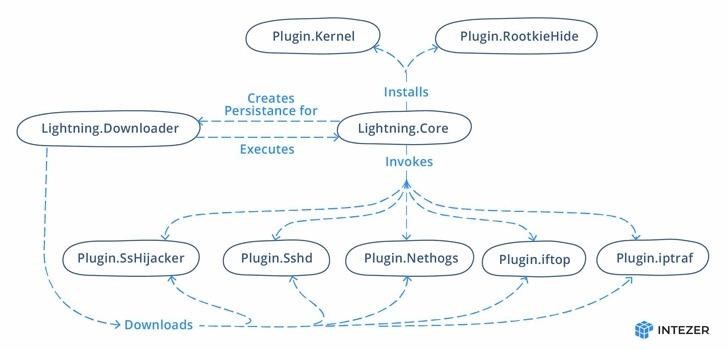
The main task of the main module is to establish communication with the manager and receive the commands necessary to execute various plugins, as well as to hide the presence on the compromised machine. For example, the malware uses typesquatting to disguise itself and disguises itself as the Seahorse password and key manager.
Other cloaking methods include changing the timestamps of malicious artifacts using timestomping, and hiding the PID and any associated network ports using one of several rootkits that the Lightning Framework is able to deploy. The malware can gain a foothold in the system by creating a script called elastisearch in /etc/rc.d/init.d/, which will be executed at each system boot and run the bootloader module again to re-infect the device.
In addition, the Lightning Framework adds its own SSH-based backdoor to the infected system: it launches an SSH server using one of the downloaded plugins (Linux.Plugin.Lightning.Sshd). As a result, this will allow attackers to connect to infected machines via SSH using their own SSH keys.



