Researchers have discovered a new RedAlert (aka N13V) ransomware that encrypts Windows and Linux VMWare ESXi servers and targets corporate networks.
MalwareHunterTeam, an information security expert, was the first to notice the new malware, posting screenshots from the group’s dark web site on Twitter.
Let me remind you that we also wrote that Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable.
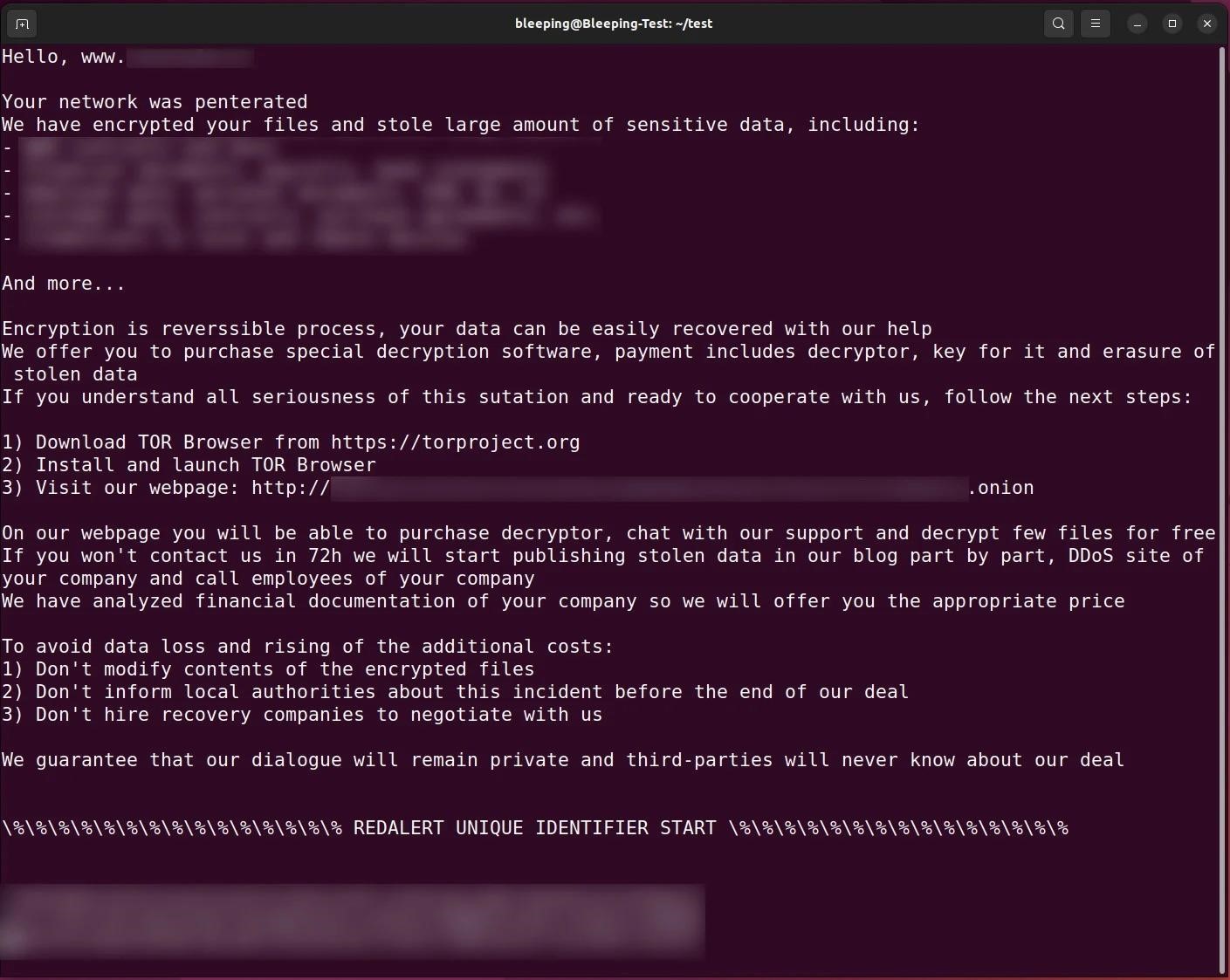
The new ransomware was named RedAlert because of the string the hackers used in the ransom note.
The attackers themselves call their malware N13V, writes Bleeping Computer.
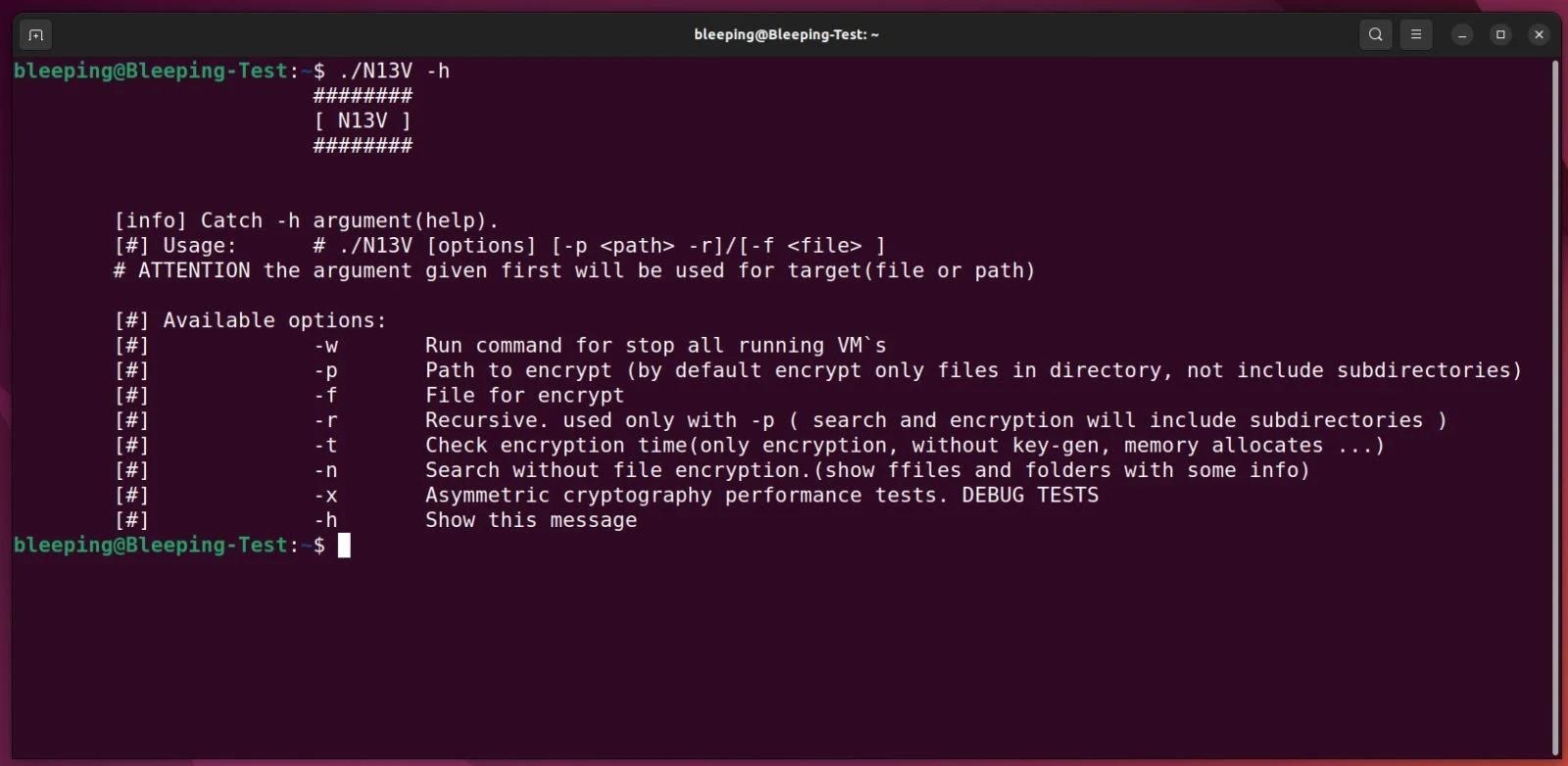
The Linux version of the ransomware is reportedly targeted at VMware ESXi servers and allows attackers to shut down any active virtual machines before encrypting files.
The researchers say that during file encryption, the ransomware uses the NTRUEncrypt algorithm, which supports different “option sets” that provide different levels of security. It is noted that in addition to RedAlert, this algorithm uses only the FiveHands encryptor.
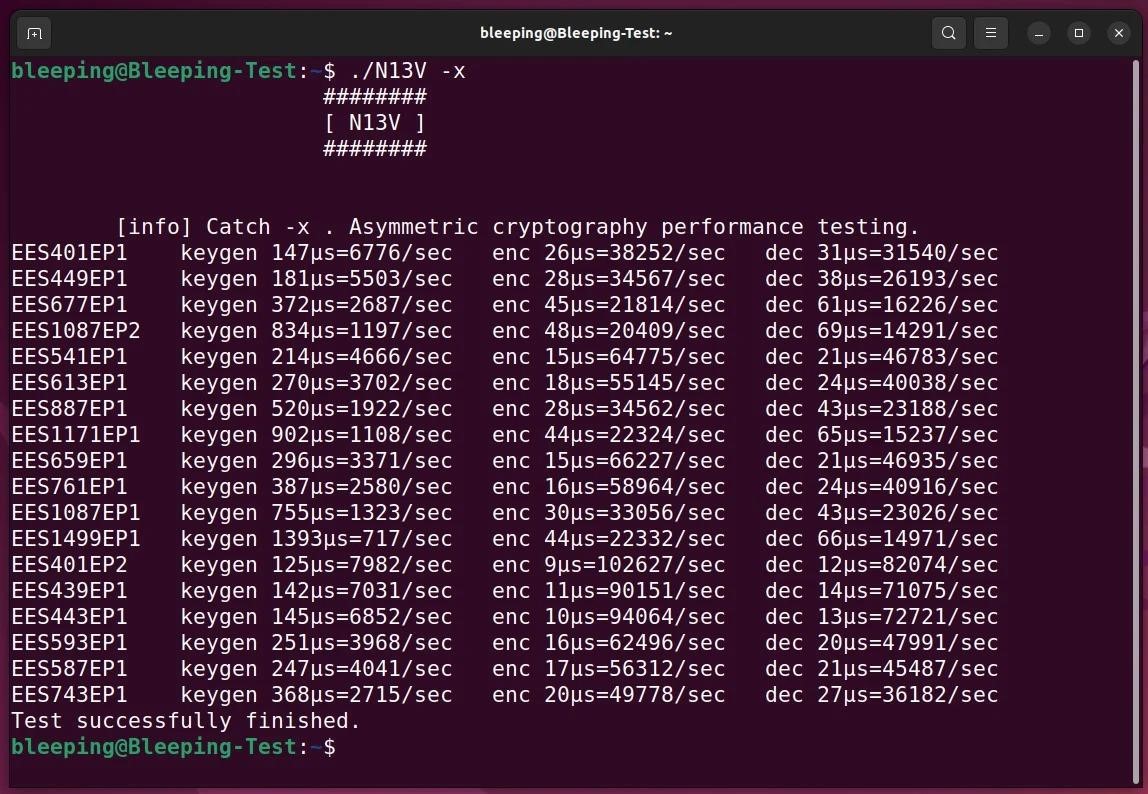
Another interesting feature of RedAlert is the “-x” command line option, which is responsible for “testing the performance of asymmetric encryption” using various sets of options. It is not yet clear whether there is a way to force a certain parameter during encryption, or whether the ransomware chooses the most effective one on its own.
During file encryption, the malware only targets files associated with VMware ESXi virtual machines, including log files, swap files, virtual disks, and so on: .log, .vmdk, .vmem, .vswp, and .vmsn. The malware adds the .crypt[number] extension to these files.
The payment site that victims are sent to via a ransom note is broadly similar to other ransomware sites in that it displays a ransom note and allows negotiating with the attackers. At the same time, the hackers emphasize that they only accept Monero cryptocurrency for payment.
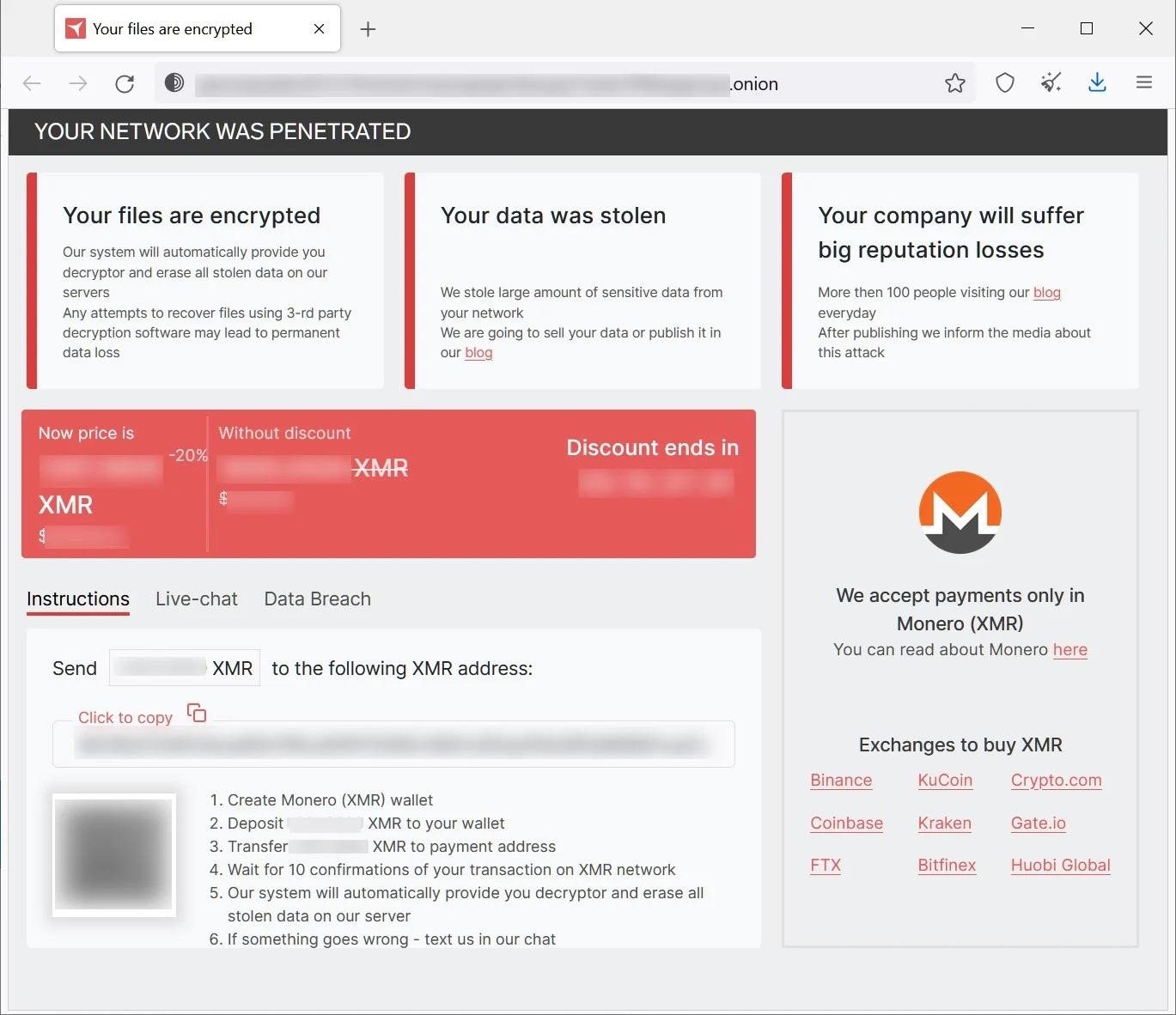
Although experts only discovered a ransomware targeting Linux, there are hidden elements on the group’s website, judging by which decryptors for Windows also exist.
So far, the RedAlert website contains data of only one attacked organization, that is, the malware is just starting its “work”.