Gridinsoft Security Lab
What is 127.0.0.1?
127.0.0.1. You’ve probably seen this number on memes, t-shirts, and tech documents. But what exactly is it, and why is it so popular? Let’s dive in and find out. 127.0.0.1 is a special Internet Protocol (IP) address known as “localhost“. As the name suggests, it’s used locally to create an IP connection with your own […]
Pornographic Virus Alert From Microsoft
Microsoft shows you the banner which states that your PC is infected with a “Pornographic virus”? It seems that someone wants to involve you in a popular online tech support scam, called “Pornographic virus alert from Microsoft”. But how can they do it with a single banner? That article will show you the whole mechanism […]
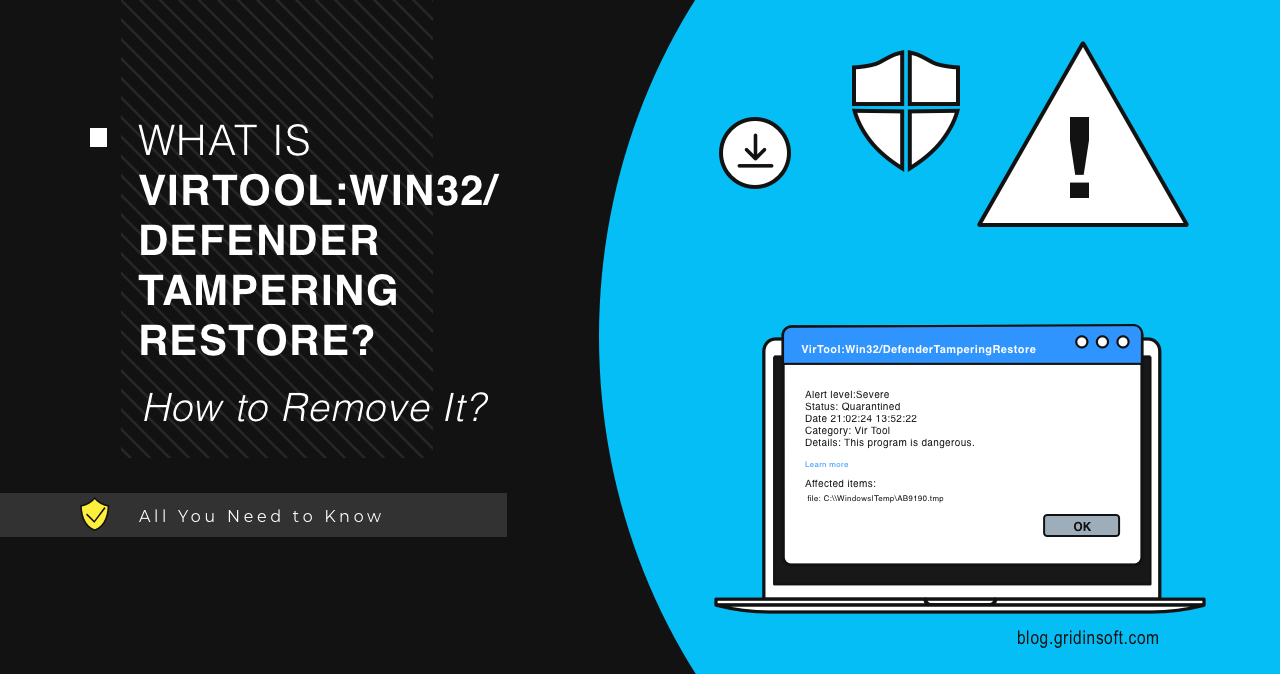
VirTool:Win32/DefenderTamperingRestore
VirTool:Win32/DefenderTamperingRestore is the name of the Microsoft Defender detection of a malicious element present in the system. Usually, it marks a thing that can weaken the system’s security and make the device vulnerable to malware injection. Let’s find out how dangerous this is, and how to deal with it. Threats like VirTool are often the […]
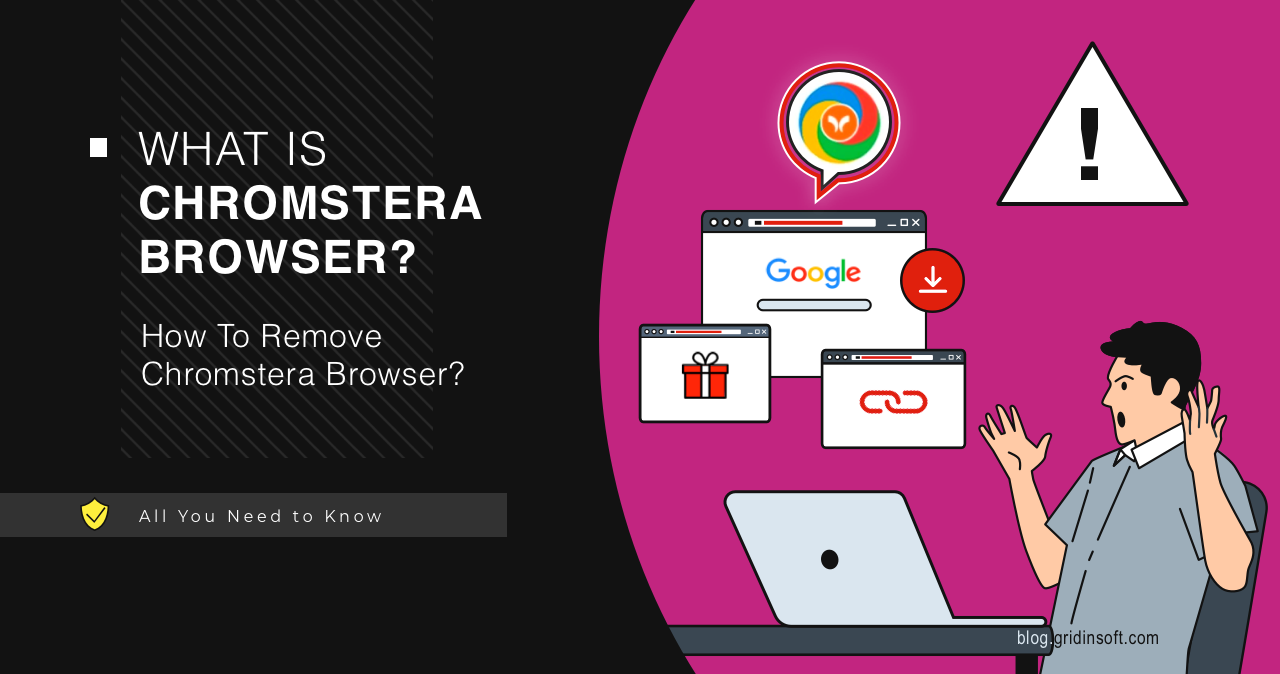
Chromstera Browser
Chromstera Browser a rogue browser that mimics Google Chrome, and spams ads, redirects search queries and collects data about the user’s online activity. Like the majority of such software, it is distributed as “recommended program” in bundles and through malicious adverts. Chromstera Browser Overview Chromstera Browser is potentially unwanted software positioned as an alternative web […]
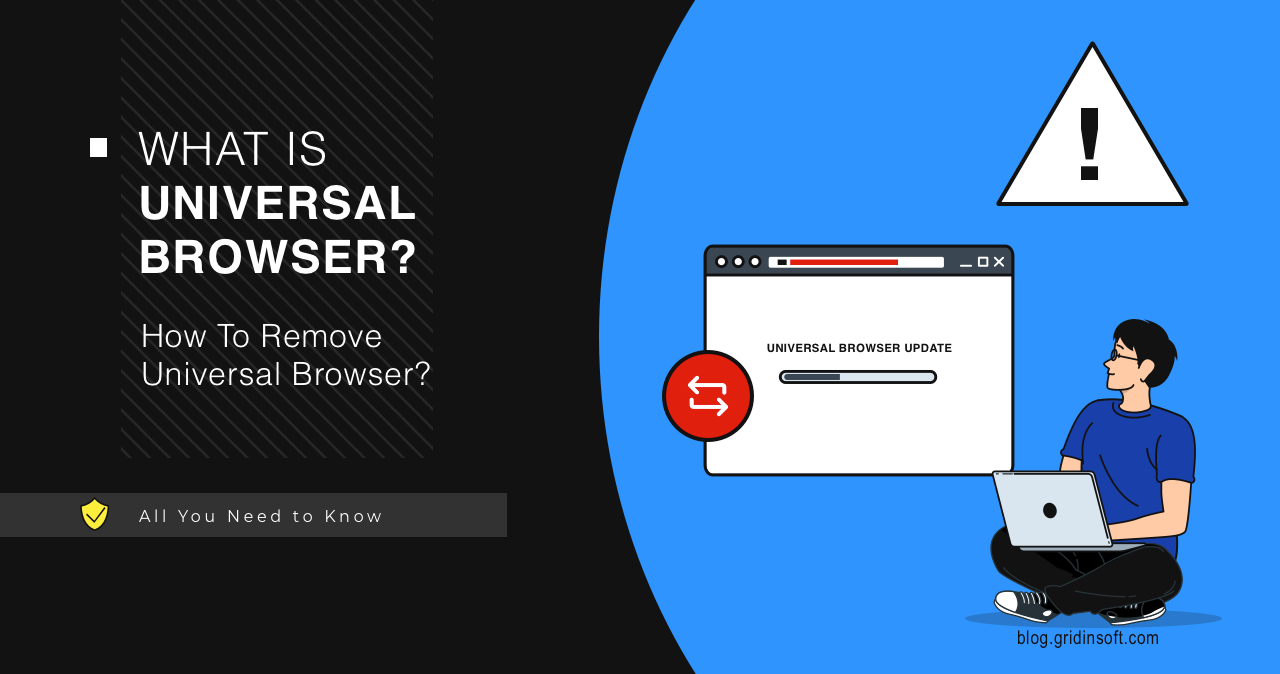
Universal Browser
Universal Browser is a name of a browser that users spectate in a strange update window that pops up in the system, occasionally reporting an update error. This window is in fact related to the Chromstera browser – a rogue web browser app. The appearance of this window happens along with systems going crazy – […]
Wave Browser
Wave Browser is an unwanted browser application that tries to look as a yet another Chromium-based project. Although it performs its function, according to users’ reviews, there are more problems than benefits. Now, we will take a closer look at it and determine whether you should use it. What is a Wave Browser? Wave Browser […]
PUA:Win32/Conduit
PUA:Win32/Conduit is a potentially unwanted application that performs suspicious activity with the browser. It changes the homepage and search engine and installs extensions. It is distributed through hacked software or under the “recommended software” guise. PUA:Win32/Conduit Overview PUA:Win32/Conduit (also goes by PUAAdvertising:Win32/Conduit) is a potentially unwanted application belonging to Conduit Search. One of Conduit’s characteristic […]
Adaware Web Companion
Web Companion is an unwanted program works as a web protection tool. It appears unexpectedly, after the installation of a different program, and tries to make the user pay for a “premium” version. Questionable effectiveness and bloated results are what makes it not recommended to use. Pseudo-effective applications are not severely dangerous, but they can […]
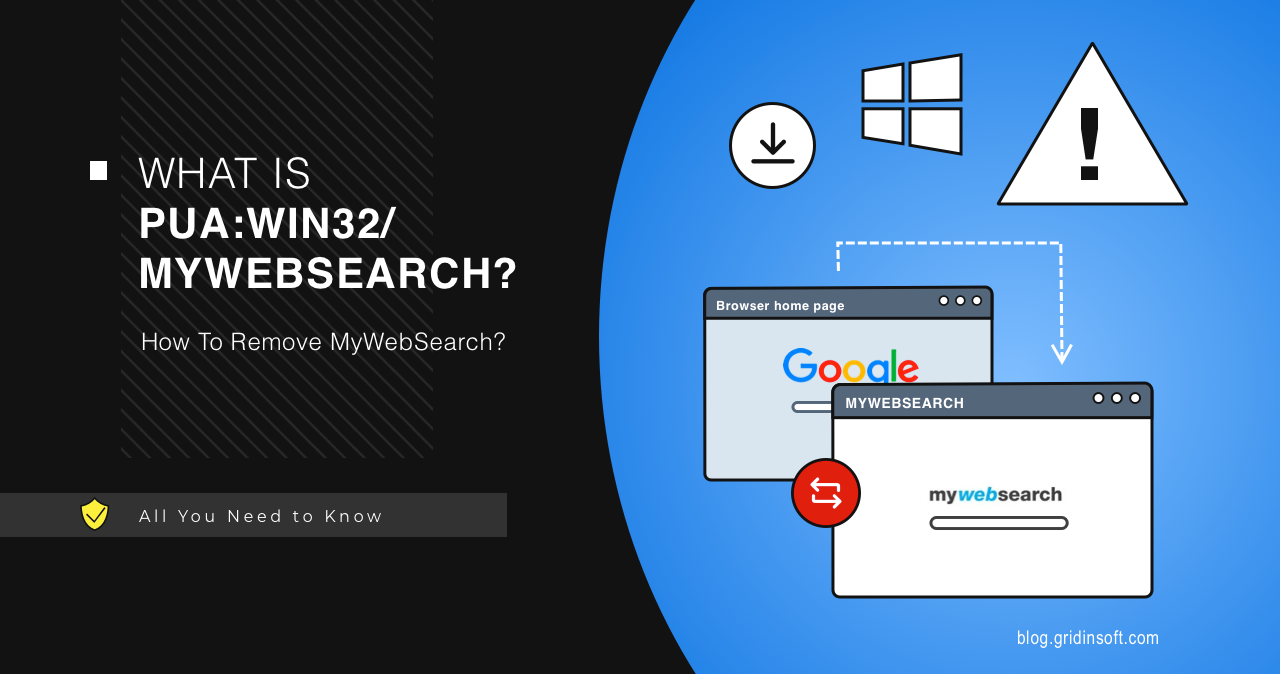
PUA:Win32/MyWebSearch
PUA:Win32/MyWebSearch is a Microsoft Defender detection that refers to an unwanted browser modifier. This application adds add-ons and toolbars that in fact take control of the web browser, redirecting search queries and causing advertisements to appear. It usually spreads as add-on software in bundles and is often installed without the user’s explicit consent. PUA:Win32/MyWebSearch Overview […]
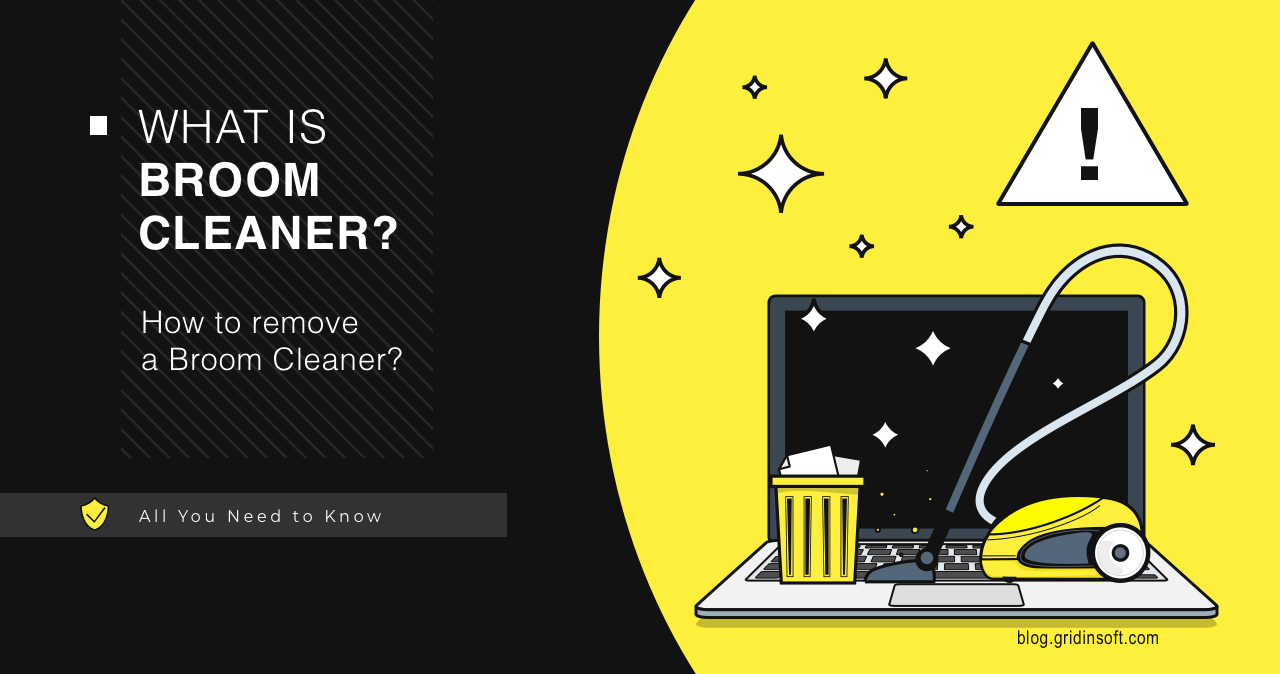
Broom Cleaner App (Virus Removal)
Broom Cleaner is an unwanted program that at first glance seems to be a safe tool for cleaning and optimizing your computer. However, in reality, once installed, it performs unwanted changes to system settings, shows ads, or even installs additional unwanted programs. This can cause significant disruption to your computer and leak confidential information. Let’s […]
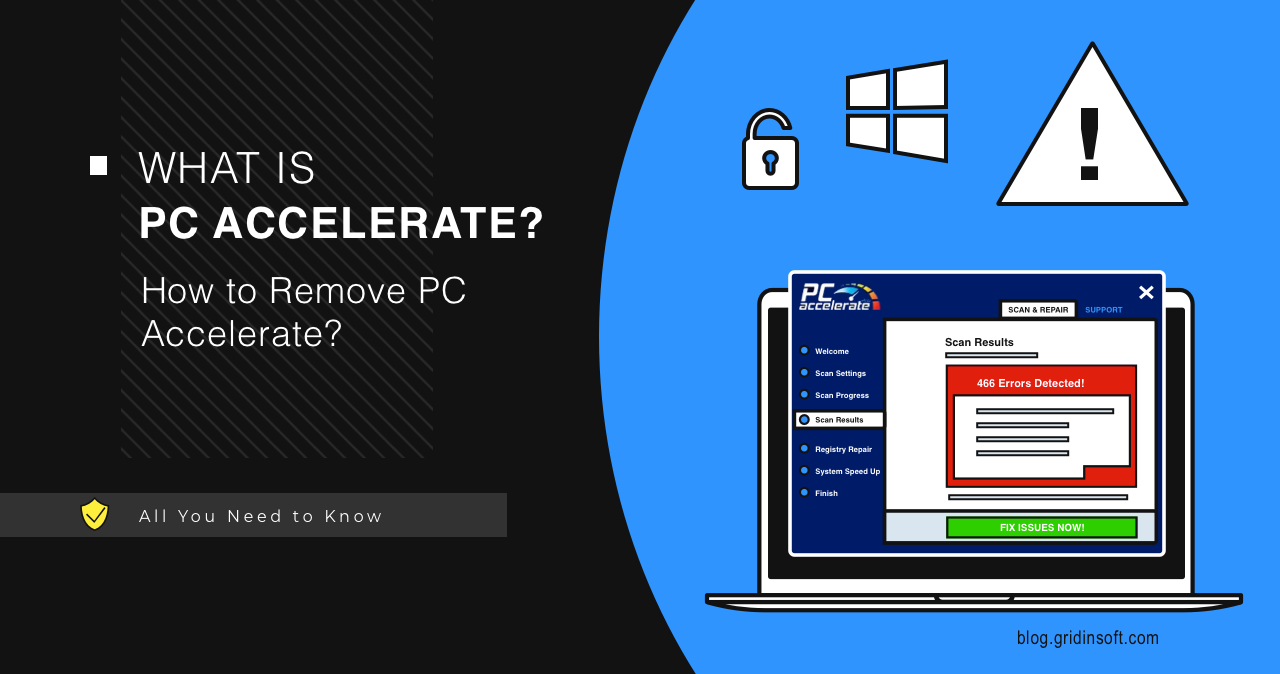
PC Accelerate
PC Accelerate is a questionable software that is presented as a useful utility designed to optimize your computer’s performance. In reality though, this software can do more harm than good. Installing such applications often leads to unintended consequences, from system slowdowns to serious security threats. What is PC Accelerate? PC Accelerate is a potentially unwanted […]
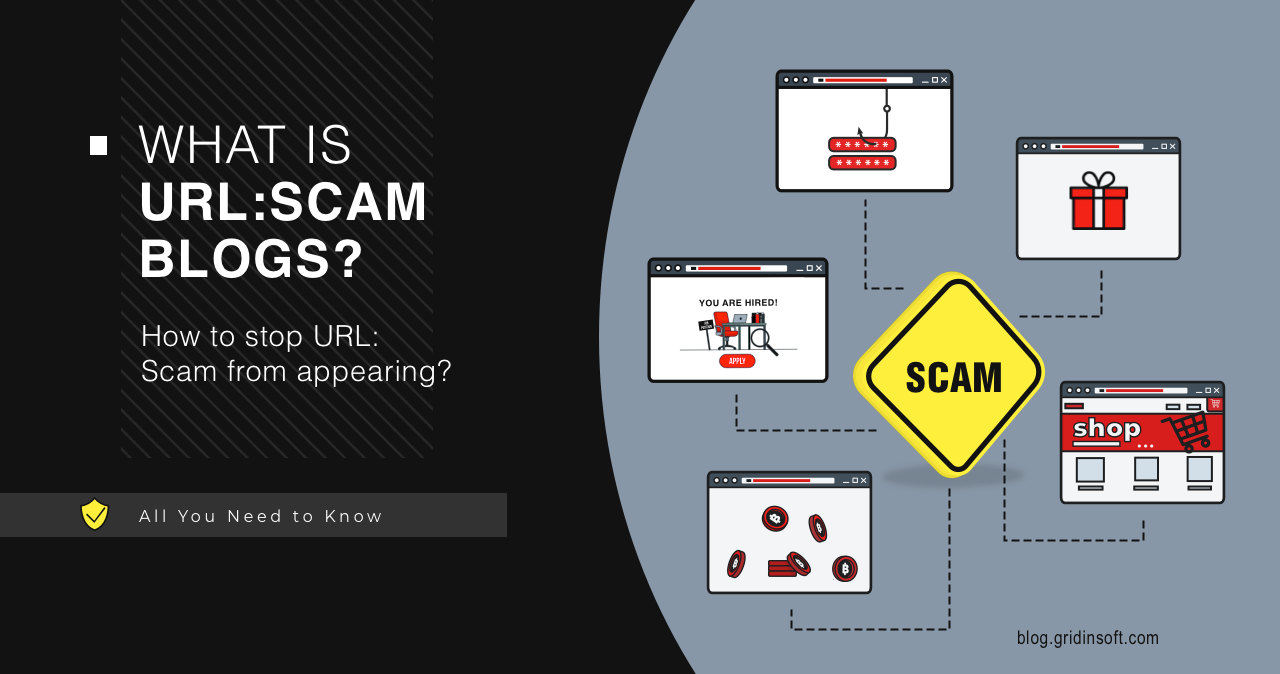
URL:Scam (Avast): Understanding This Detection and Securing Your System
The URL:Scam detection by Avast and AVG is a protective warning that triggers when these security solutions identify a website as potentially fraudulent or malicious. When this alert appears during browsing, it means the antivirus has flagged a web address as a probable scam operation. This protection mechanism helps safeguard users, but understanding when and […]