“Hello perv” is the name for an email scam that got its name from the eponymous title. It aims at scaring the user and asking them to pay the ransom in cryptocurrency, in exchange for not publishing explicit content. These emails are sent in thousands, targeting people all around the world, sometimes even misfiring by sending these letters to tech support addresses.
Such scam emails typically straddle users’ unawareness about how malware and the overall cybercrime world normally work. They take the claims about collected personal information for granted and obey any of the further guidelines. However, there are quite a few signs of these messages being complete and utter scams, and I am going to reveal all of them in this post.
Hello Perv Email Scam Overview
Hello Perv is an email scam that circulates for several months already, gaining significant popularity at the end of June 2024. Fraudsters send them to different emails in hundreds, if not thousands, hoping for gullible people to believe the text and follow the instructions. The email contains threats of publishing explicit graphical content that the hacker has allegedly collected using spyware.
The demand of the email, as you can see above, is about sending a sum of money (typically ~€500) in Bitcoin to a cryptocurrency wallet. One outstanding detail here is that the hacker provides the ability to get extra time to pay the ransom. Overall, the email body is built around social engineering tricks, while having a lot of manipulative facts and logical mistakes. Let me explain each one of them, so you will have a better understanding of how con actors manipulate people and how to detect such scam emails in the future.
Revealing Introduction & Malware Description
Hello Perv fraudulent email did not really try to prolong the narrative. From the very beginning, the fraudster talks about infecting the device through a site with adult content. Further, they claim to start recording from the web camera and capturing the process of the victim touching themselves. To make matters worse, the hacker claims manipulated the resulting video to make it look like the user was watching a prohibited category of adult videos.
A thing that scares a lot of people is that they see this email being sent from their own address. This may look like hackery, but is, in fact, a rather easy trick of sender email spoofing. It only requires using a specific email client, that allows tinkering with email metadata. But nonetheless – this makes enough people believe the scam is genuine.
One major fault here is the story about hacking the computer through an infected browser page. Well, this is totally possible – browsers may be vulnerable to code injections and other flaws. But applying such a technique in attacks on individual users is simply unreasonable. Exploiting vulnerabilities is more suitable in attacks on corporations, where potential profits are much higher.
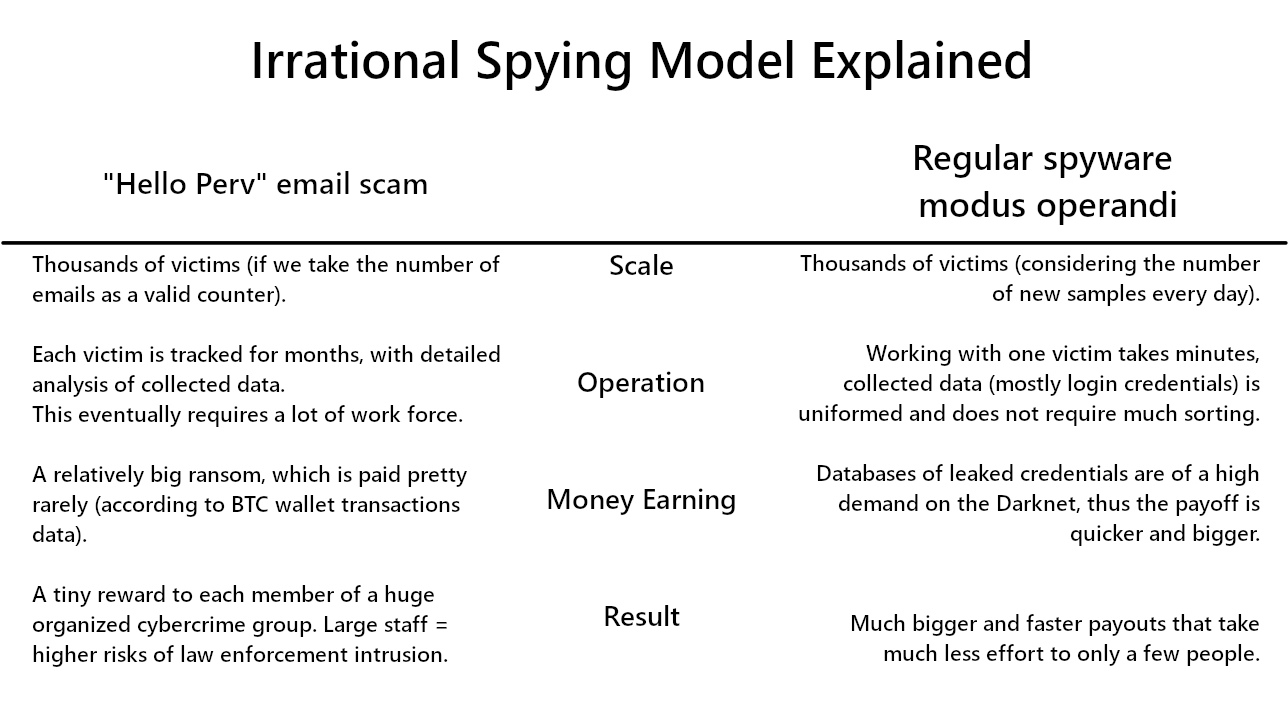
There is also an old-new tactic of hacking the site and putting the “update your browser” banner on top of all the content. Clicking the update button will lead to malware downloading, and the user will likely execute it thinking it is a genuine update. Thing is – all the malware families deployed in such a manner are well-known and do not operate in the way the hacker describes. Doing what spyware operators normally do – collecting credentials and selling them on the Darknet – is more profitable and takes less effort.
Ransom Demands
After the rapid introduction, the “hacker” puts out the demand: pay a ransom to a cryptocurrency wallet and no explicit videos will make it to the public. Typically for this specific email campaign, ransom amounts are around €500, though it may change in future. As I’ve already mentioned, there is a possibility to extend the ransom payment deadline for another 48 hours. One particularly interesting clue here is the Bitcoin wallet: its statistics uncover how “successful” this scam is.
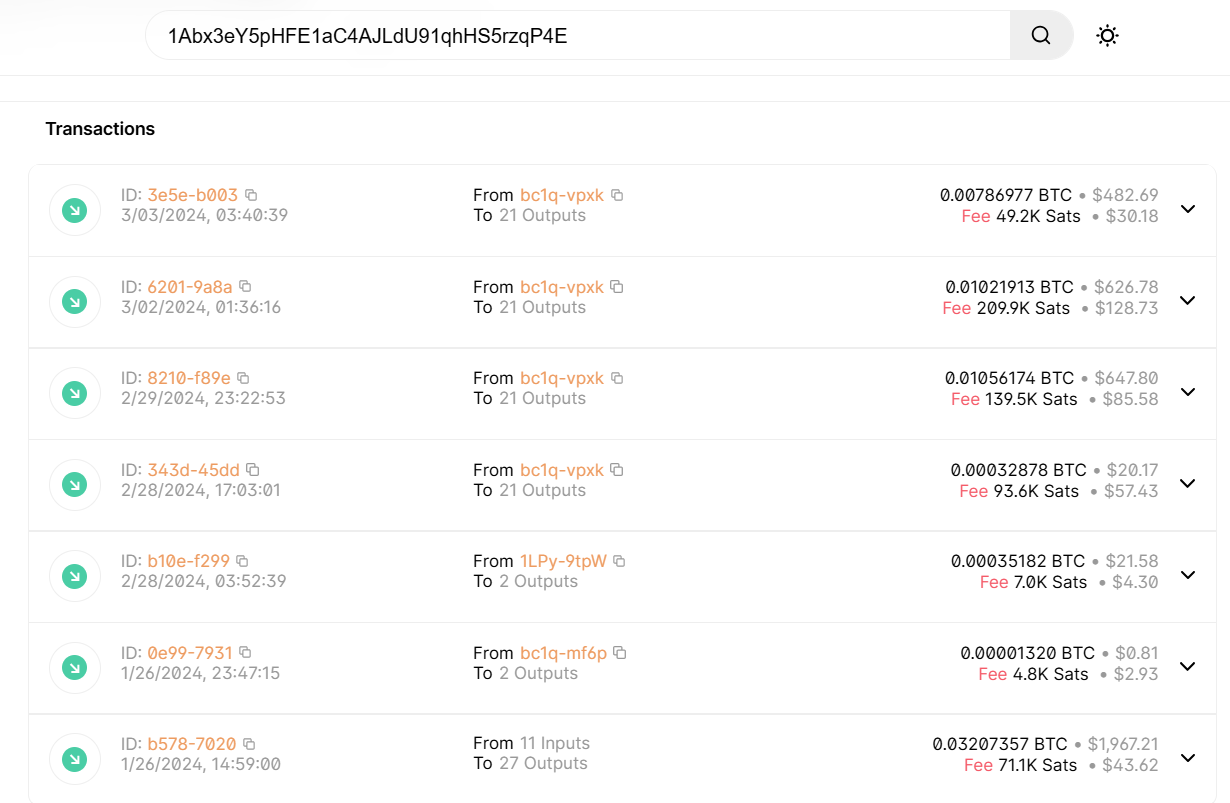
It is possible to see the Bitcoin wallet balance & history using free blockchain explorer tools. A few clicks – and voila, we now can see when and how much was paid to the wallet in the past. Throughout the extensive list of wallets, the majority have just a few transactions, with a total sum of $4-6k. Interestingly, the sum of some of the incoming transactions is twice of what is the current bid of the scammer. This implies that the fraudster either uses the wallet for several scam campaigns, or forces victims into paying more, possibly after extending the deadline.
Threats of Publishing Explicit and Compromising Videos
Strangely, the actual threats go after the ransom demand – not a usual tactic for this kind of scammers. Though, it was rather obvious where all this is going: “hacker” threatens to publish the compromising video to all the victim’s social media pages, so all friends and colleagues will see this abomination. And the forbidden character of the video suggests that this may be the reason for law enforcement to turn their attention.
Obviously, same as pretty much any other email scam, this one ensures the user about watching their computer and user’s actions. Shall the user try to trick the scammer, they will translate their threats into actions. Though, I wonder how the scammer will track a police call from your phone? Or from a friend’s phone? Once again, the email is full of rather obvious logical mistakes, and that’s just another one. Most of them are clearly visible even to people without much knowledge in cybersecurity, it’s merely about cold-minded analysis.
Any chances the computer is infected?
Despite the Hello Perv email being a blatant scam like a Professional Hacker Scam or Pegasus Scam, there is still a possibility that malware once was present in your system. Some variations of such email scams may additionally scare people by showing them their (old) passwords. This pretty much forces users into believing the fairy tales about advanced spyware and all-encompassing tracking. To be sure your system is clean of any spyware, consider scanning it with GridinSoft Anti-Malware: it is capable of finding and eliminating even the most recent spyware samples.