FXLocker is a ransomware-type malware. It is supposedly targeting large organizations or is in open testing. In this post, I will explain what this threat is and what to do if you fall victim to it.
FXLocker Ransomware Overview
FXLocker is a newly identified ransomware variant that follows the typical modus operandi of file-encrypting malware. It targets user files, encrypting them with a strong cryptographic algorithm, and appends the “.fxlocker” extension to the affected files. Victims are then presented with a ransom demand, instructing them to pay a hefty sum in Bitcoin to recover their data. The ransom note appears both in a pop-up window and a text file named “README.txt.”
Interestingly, FXLocker’s ransom demand is set at 0.75892 BTC – equivalent to around $95,000 at the time of analysis. This figure is unusually high for ransomware that could potentially affect individual users. This suggests that the malware might either be misconfigured (which is unlikely) or intended to attack corporations. Moreover, the ransom note lacks a valid Bitcoin wallet address, which raises questions about whether the ransomware is still in a testing phase or if the attackers are handling payment collection manually.
Detailed Analysis
FXLocker operates through a straightforward but highly effective infection chain. Once executed, it scans the victim’s system for files to encrypt, applying the “.fxlocker” extension to each one. The encryption algorithm used is robust, making decryption without the attackers’ key practically impossible. Like many modern ransomware strains, FXLocker ensures that victims cannot access their data without intervention from the perpetrators.
The ransom note explicitly warns against renaming or modifying encrypted files, as this could prevent decryption. Additionally, it cautions victims against closing the pop-up or rebooting their system. This suggests that the malware might incorporate persistence mechanisms or secondary payloads designed to corrupt data upon system restart.
In terms of detection, major antivirus vendors have flagged FXLocker under various names, such as “Trojan:Win32/Wacatac.B!ml” (Microsoft). The inclusion of “Python” in some detections indicates that the ransomware is likely written in Python. This aligns with a growing trend where cybercriminals leverage easy-to-deploy scripting languages to develop ransomware.
Ransom Note Overview
The ransom note delivered by FXLocker is both typical and concerning. It explicitly states that all files have been encrypted and demands 0.75892 BTC for decryption. The note provides two contact emails ([email protected] and [email protected]) for victims to reach out to the attackers. Additionally, it includes a “Reference ID” that victims are instructed to mention in their correspondence.
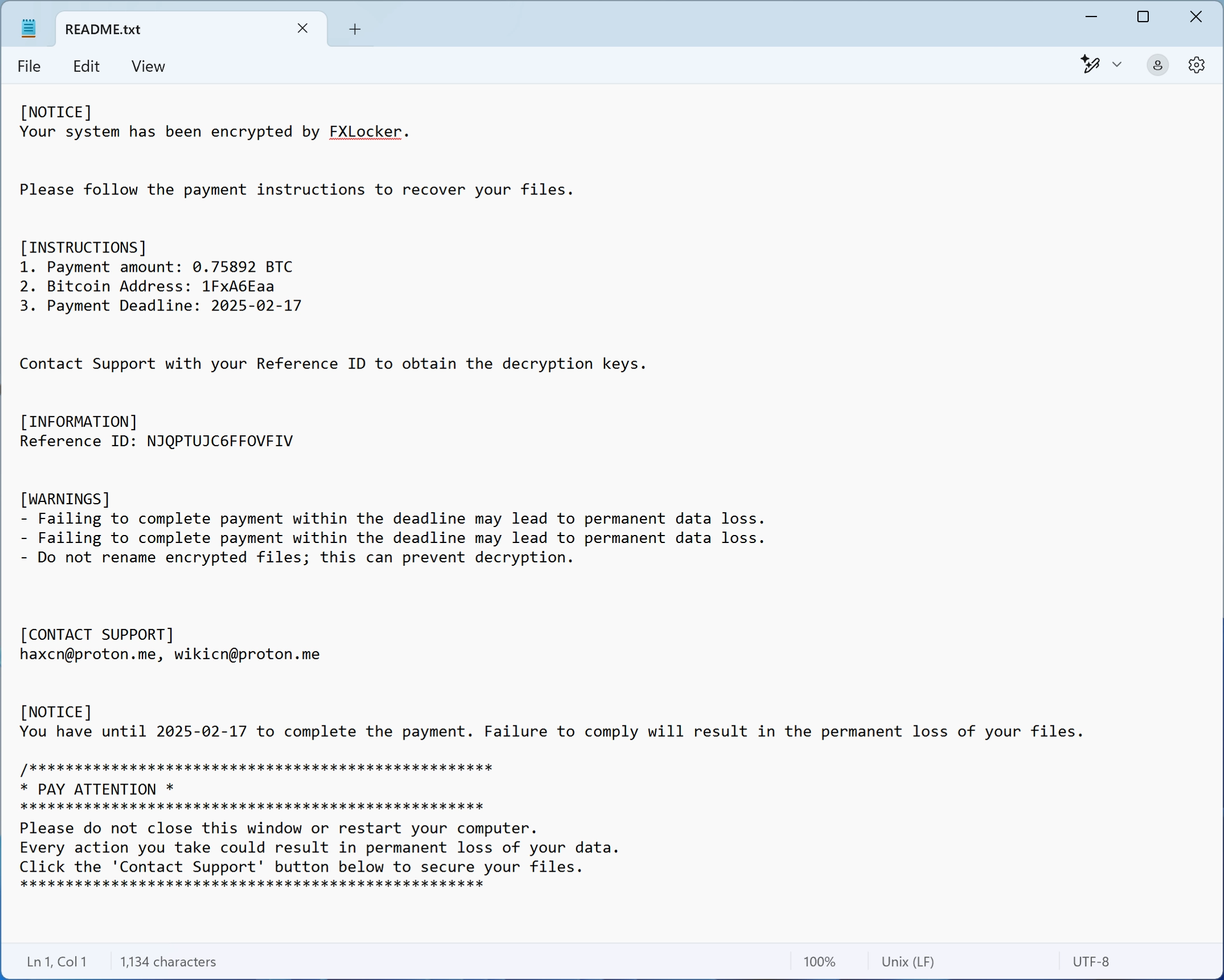
What makes this ransom note uncommon is the absence of a valid Bitcoin wallet address. Typically, ransomware groups include a hardcoded wallet address to streamline payments. However, FXLocker requires victims to contact them first. This suggests that the ransomware operators might be handling payments on a case-by-case basis, possibly negotiating ransom amounts based on the victim’s profile.
The note also doubles down on psychological pressure, warning that failure to comply within the deadline will result in “permanent data loss.” While this is a common tactic used by ransomware operators, the repetition of this threat in the note hints at a less professional approach compared to more established ransomware gangs.
How to Remove FXLocker Virus?
The first step should be removing FXLocker from the system entirely. As long as the ransomware remains active, any newly created or recovered files risk being re-encrypted. The best approach is to disconnect the infected system from the internet and run a full system scan using reputable antivirus software. Booting into Safe Mode with Networking and using GridinSoft Anti-Malware can also help in identifying and removing the malicious payload. Download it by clicking the banner below and run a Full Scan to check the system down to the most remote areas, so the malware will be gone for good.
While manual removal might be possible for some threats, FXLocker employs multiple persistence mechanisms. This makes complete eradication difficult without professional tools. Therefore, using security software is strongly recommended to prevent further damage.
How to Recover FXLocker Files?
Unfortunately, at the time of writing, no publicly available decryption tool exists for FXLocker. The encryption algorithm is strong, meaning brute-force decryption is not a feasible option. Unless a flaw is discovered in the ransomware’s implementation, recovering files without the attackers’ key remains impossible.
Despite this, I strongly discouraged paying the ransom. Firstly, there is no guarantee that the cybercriminals will provide the necessary decryption key even after receiving payment. Additionally, paying the ransom only fuels further attacks, encouraging criminals to continue their operations.
The best way to restore files is through a backup. If an unaffected backup is available, users should format their systems, reinstall their operating system, and restore data from the backup. If no backup exists, data recovery software might offer limited help, but its effectiveness is uncertain. Moving forward, implementing a robust backup strategy-storing copies of critical files on external or cloud-based systems-remains the best defense against ransomware attacks.





