Attackers are again abusing the Google Ads platform to distribute malicious advertising and Redline information stealer. This time, the ads advertised a trojanized version of the CPU-Z tool.
CPU-Z Malware in the WindowsReport Page Clone
Recently, a wave of malicious ads on Google Search results page offered users a Trojan-infected version of the popular CPU-Z program. For better disguise, the malware was hosted on a clone site of the real news site WindowsReport. As the presence of the official site for the product is not that obvious for users, such a trick was quite effective.
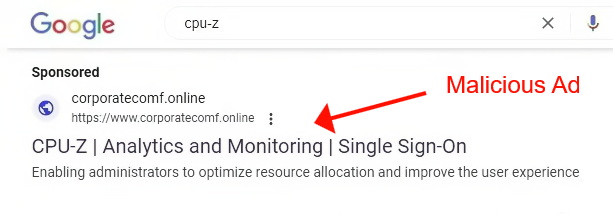
By clicking on such an advertisement, the victim goes through a series of redirects that fooled Google’s security scanners and filtered out crawlers, VPNs, bots, etc., redirecting them to a special decoy site that did not contain anything malicious.
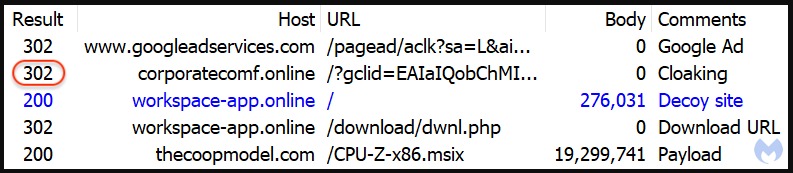
Users ended up on a fake news site hosted on one of the following domains:
- argenferia[.]com;
- realvnc[.]pro;
- corporatecomf[.]online;
- cilrix-corp[.]pro;
- thecoopmodel[.]com;
- winscp-apps[.]online;
- wireshark-app[.]online;
- cilrix-corporate[.]online;
- workspace-app[.]online.
The result of these manipulations is the chain attack, initiated with FakeBat malware. Further, this loader injects well-known RedLine infostealer – an old-timer of the scene.
What is RedLine Infostealer?
Downloading the CPU-Z installer from the attackers’ resource resulted in the download of an MSI file containing a malicious PowerShell script, which the researchers identified as the FakeBat malware loader (aka EugenLoader). This downloader extracted the Redline payload from a remote URL and launched it on the victim’s computer.
Redline is a powerful data theft tool that can steal passwords, session tokens, cookies, and vast amounts of other stuff. We have a dedicated article with the complete tech analysis of this malware – consider checking it out.
Earlier, we wrote about how cybercriminals distribute RedLine infostealer. It uses sites for downloading the fake MSI Afterburner utility. To distribute it, various domains were also used as part of the hacker campaign, which could be mistaken by users for the official MSI website. The imitation of brand resources was done quite well.
According to Google representatives, all malicious ads associated with the hacker campaign to distribute the infected CPU-Z tool have now been removed, and appropriate action has been taken against the accounts associated with them.
This is not the first time that hackers have used Google Ads
This exact malvertising campaign was discovered by analysts, who believe it is part of a previously observed campaign of a similar purpose. Previously, the attackers used fake Notepad++ advertisements to deliver the malware.
In the ads, the attackers promoted URLs that were clearly not associated with Notepad++, and used misleading titles in their ads. Since headers are much larger and visible than URLs, many people likely didn’t notice the catch.
Let me remind you that we talked about how malware operators and other hackers are increasingly using Google Ads to distribute malware to users who are looking for popular software. So, you can encounter malicious ads when searching for Slack, Grammarly, Dashlane, Audacity, and dozens of other programs.




