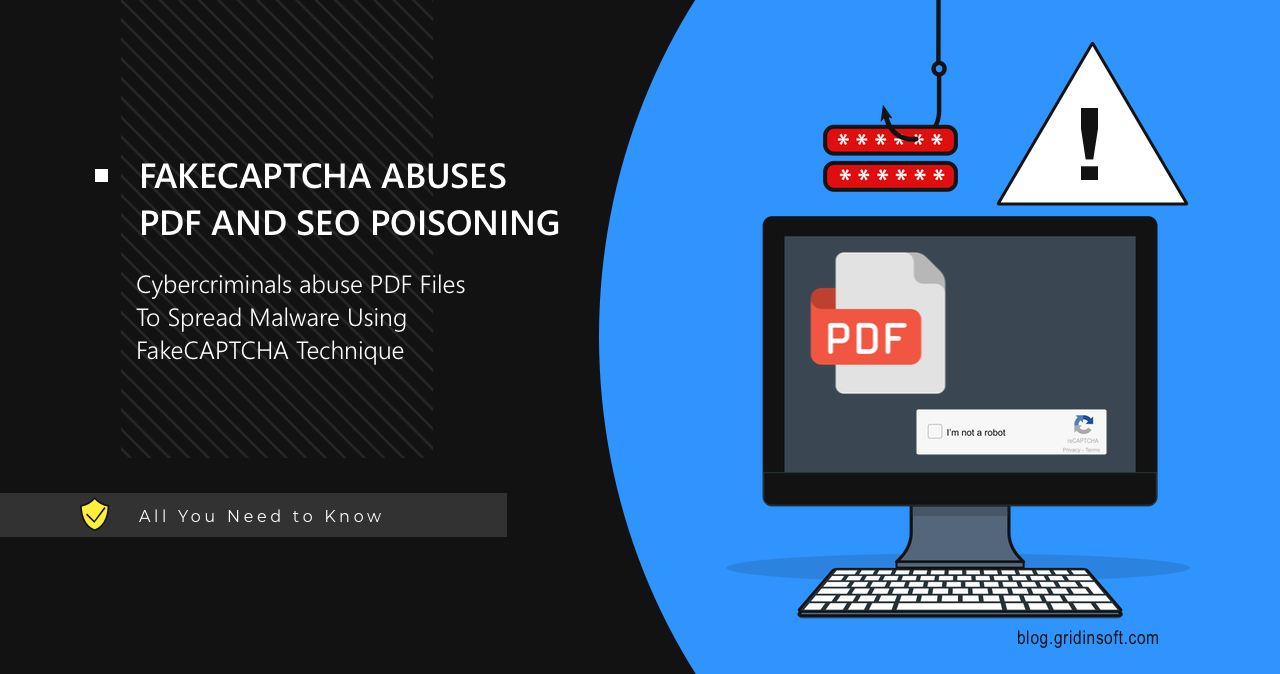
Cybercrime actors misuse search ads to distribute fraudulent PDF files, that lead to fake CAPTCHA sites. This can end up with malware .
Phishing Campaign Abuses Webflow, SEO, and Fake CAPTCHA
A recent phishing campaign has been targeting individuals searching for documents online, aiming to steal their credit card information. This operation has been active since mid-2024 and has affected numerous users across various industries. The most impacted sectors include technology, manufacturing, and banking, particularly in North America, Asia, and Southern Europe.
The attackers abuse search engines to lure victims into accessing malicious PDF files hosted on Webflow’s Content Delivery Network (CDN). These PDFs contain fake CAPTCHA images embedded with phishing links, leading unsuspecting users to provide sensitive information.
Technical Details of the Scam
Essentially, the attack is based on search advertising, specifically the abuse of search results. The attackers exploit Webflow’s CDN to host malicious PDFs. Webflow, a popular website builder, offers CDN storage for customer assets, which in this case is misused to store harmful PDF files.
Next, Google’s algorithms come into play. When individuals search for specific keywords like book titles, documents, or charts, these malicious PDFs appear in the top search engine results. In our case, it’s assets.website-files[.]com. The PDFs are crafted with multiple targeted keywords to increase their visibility.
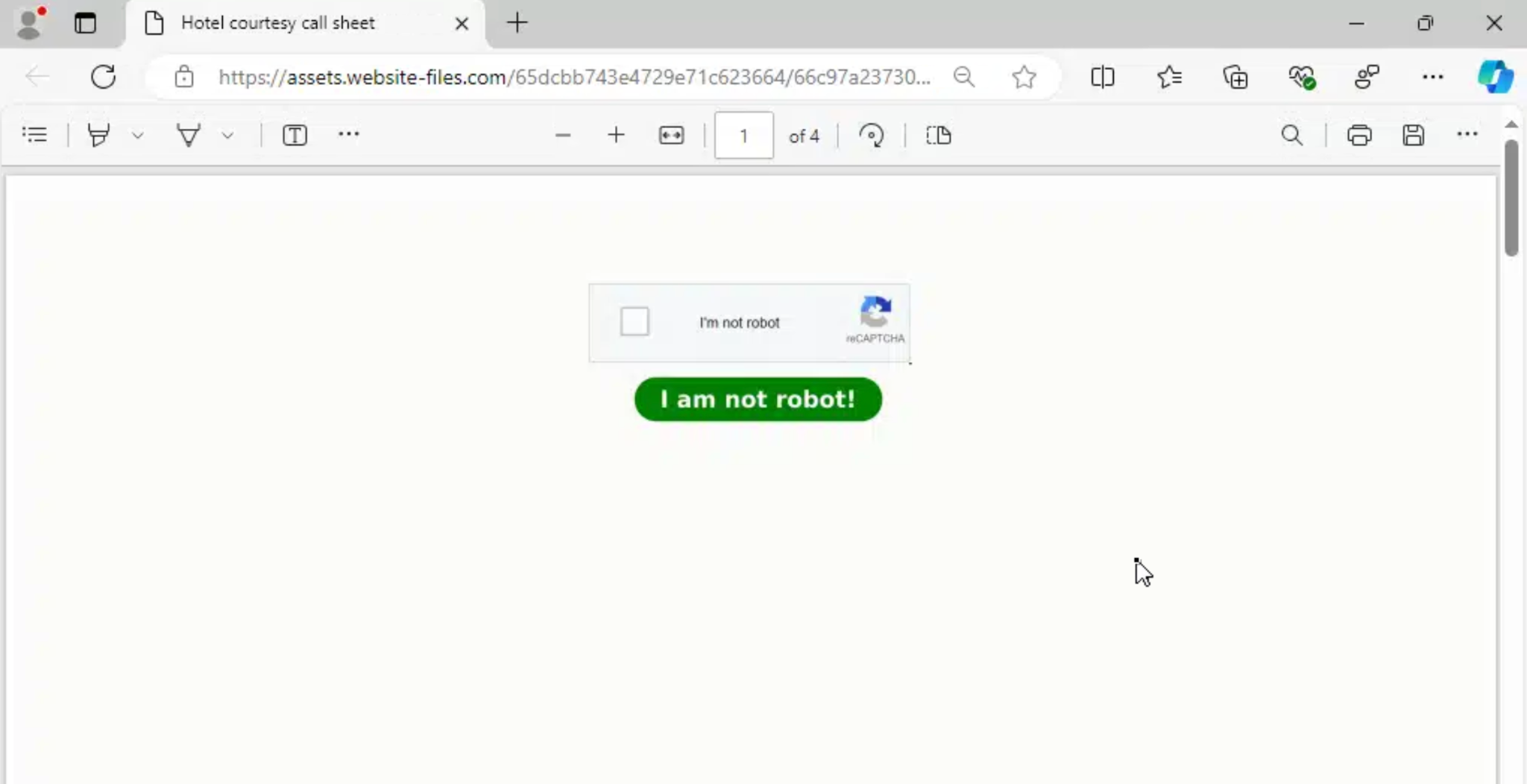
Upon opening, the PDF displays a fake CAPTCHA image. However, it’s just an image with a link. So, when users attempt to solve this CAPTCHA, they are redirected to a website that is protected with an actual Cloudflare Turnstile CAPTCHA. This step creates an illusion of legitimacy.
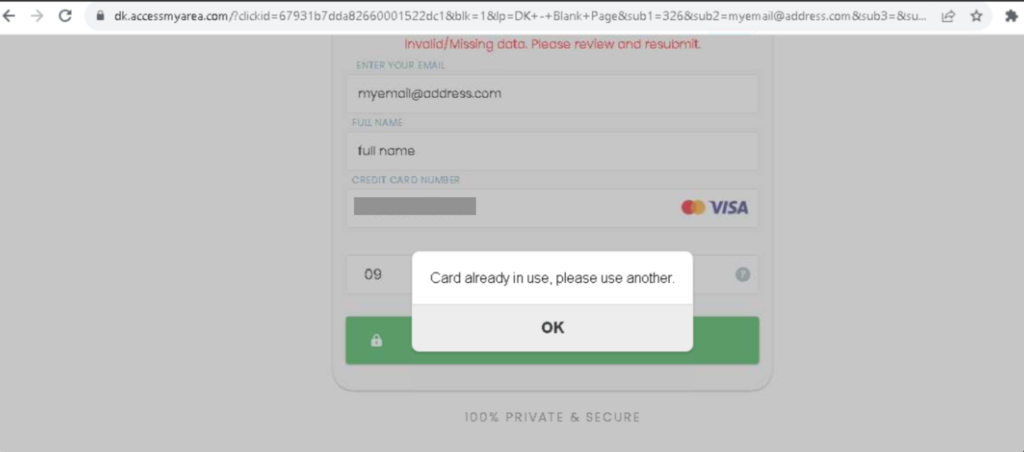
After completing this step, users are taken to a forum offering a file named after their search query. To download the document, users are prompted to sign up by providing their email address and full name. Subsequently, they are asked to enter their credit card details to complete the sign-up process. At this point, the user should be suspicious.
Once users provide this information, an error message is displayed, prompting users to resubmit their credit card details multiple times. Nevertheless, the entered data was sent to the attackers as early as the first time. Eventually, they are redirected to an HTTP 500 error page, leaving them unaware that their information has been compromised.
Where can this data go?
Stolen data has only two paths: the first is for scammers to directly try to use it, and the second is to sell it on the Darknet. Depending on the chosen option, the time of receiving a “read report” in the form of online payment attempts with the entered card will be sooner or later. If payment attempts followed almost immediately after the leak – the fraudsters decided not to bother.
On the other hand, if the attackers plan to resell the stolen data on thematic forums, there may be no feedback for a long time. Although this may suggest that nobody stole anything, I strongly recommend blocking the leaked card and reissuing it. If this is not possible, it is very important to disable the credit limit on the card as well as the ability to pay online without confirmation.
How To Stay Safe?
To avoid falling victim to such phishing scams, it is crucial to incorporate critical thinking. Be cautious if a PDF file presents a CAPTCHA, as this is unusual for PDFs and should raise a red flag. First, I strongly recommend avoiding clicking on links labeled as “Sponsored” in search engine results. These links almost always lead to malicious sites. Instead, consider use an ad blocker and a reputable anti-malware solution to enhance your protection against such threats.
Continuing about protection against such threats, I would recommend using GridinSoft Anti-Malware. Foremost, it is a reliable solution that has an Internet Security module that is designed to protect against such scams. Secondly, it is a comprehensive solution that will provide all-round protection of your system from all kinds of cyber threats.