Fortinet researchers studied the recently appeared open-source cryptor Cryptonite, distributed for free on GitHub.
It turned out that the creator of the malware made a mistake in the code, and the malware did not encrypt, but destroyed the data of the victims.
Let me remind you that we also wrote about FBI Says Cuba Ransomware ‘Made’ $60 Million by Attacking More Than 100 Organizations, as well as Security Experts Secretly Helped Zeppelin Ransomware Victims for Two Years.
Unlike other ransomware, Cryptonite was not sold on the darknet, but was distributed openly: it was published on GitHub by someone under the nickname CYBERDEVILZ (since then, the source code of the malware and its forks have already been removed).
The researchers say that the malware written in Python was extremely simple: it used the Fernet module to encrypt files and replaced their extension with .cryptn8.
The Cryptonite ransomware sample implements only basic ransomware functionality. The operator can set up a few things such as the exclusion list, server URL, email address, and bitcoin wallet. However, encryption and decryption are very simple and unreliable.
It also doesn’t provide any of the typical (but more sophisticated) ransomware features, such as:
- Removing Windows Shadow Copy
- Unlock files for more thorough exposure
- Anti-analysis
- Defensive evasion (bypass AMSI, disable event logging, etc.)
While this ransomware variant has given newcomers easy access to the cybercriminal business, it is not a serious tool.
However, something went wrong in the latest version of the malware: a sample of Cryptonite studied by experts blocked files beyond recovery, in fact, acting as a wiper.
The researchers say that the destructive behavior of the malware was not intended by its author. Rather, this is due to its low qualification, as errors in the code cause the program to crash when trying to display a ransom note (after the encryption process is completed).
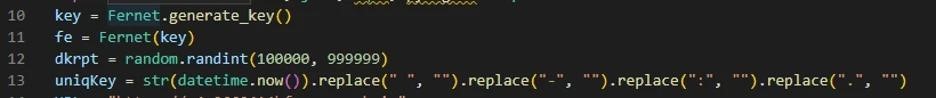
In addition, an error that occurs during the operation of the encryptor leads to the fact that the key used to encrypt files is not transmitted to the malware operator at all. That is, access to the victim’s data is blocked completely and permanently.




