Experts noticed that this week Emotet resumed its activity and after a three-month “rest” began to send malicious spam again. So far, information security specialists have not found any additional payloads.
It looks like the malware is just collecting data for future spam campaigns.
Let me remind you that we also wrote that Emotet Malware Operators Found a Bug in Their Bootloader.
The resumption of malware activity was reported by Cofense analysts and specialists from the Cryptolaemus group, which includes more than 20 experts from around the world, who united in 2018 for a common goal – to fight Emotet.
The researchers recalled that the last Emotet spam campaign was observed in November 2022, and then spamming lasted only two weeks. Now the malware has continued to recover and collects new credentials for use, as well as stealing information from address books for targeting.
This time, instead of using chained response emails, as in the previous campaign, the attackers are using emails that mimic various invoices.
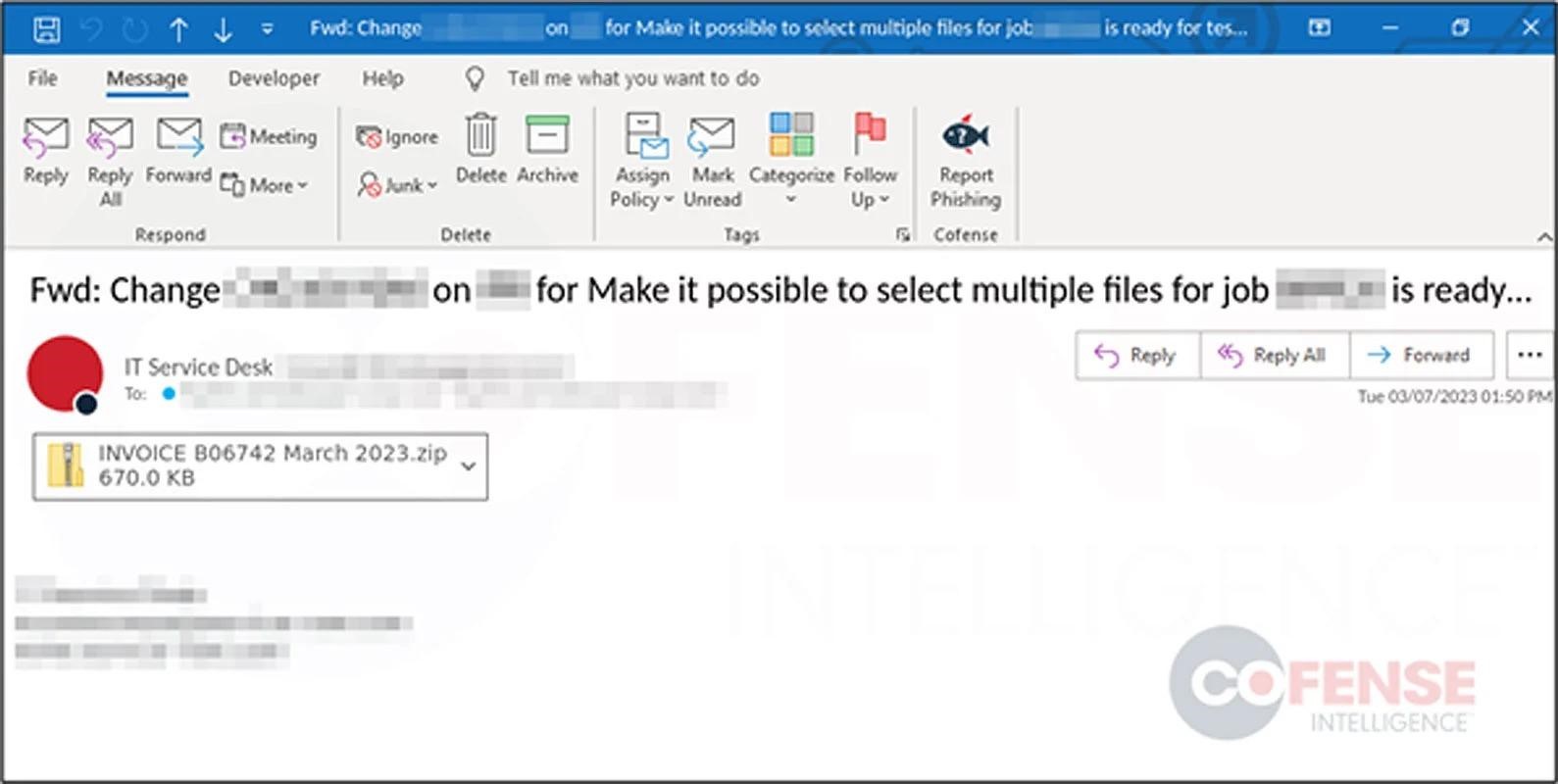
ZIP archives containing intentionally “bloated” Word documents larger than 500 MB are attached to such emails. Documents are deliberately filled with unused data to make the files bigger and harder for antivirus solutions to scan and detect malware.
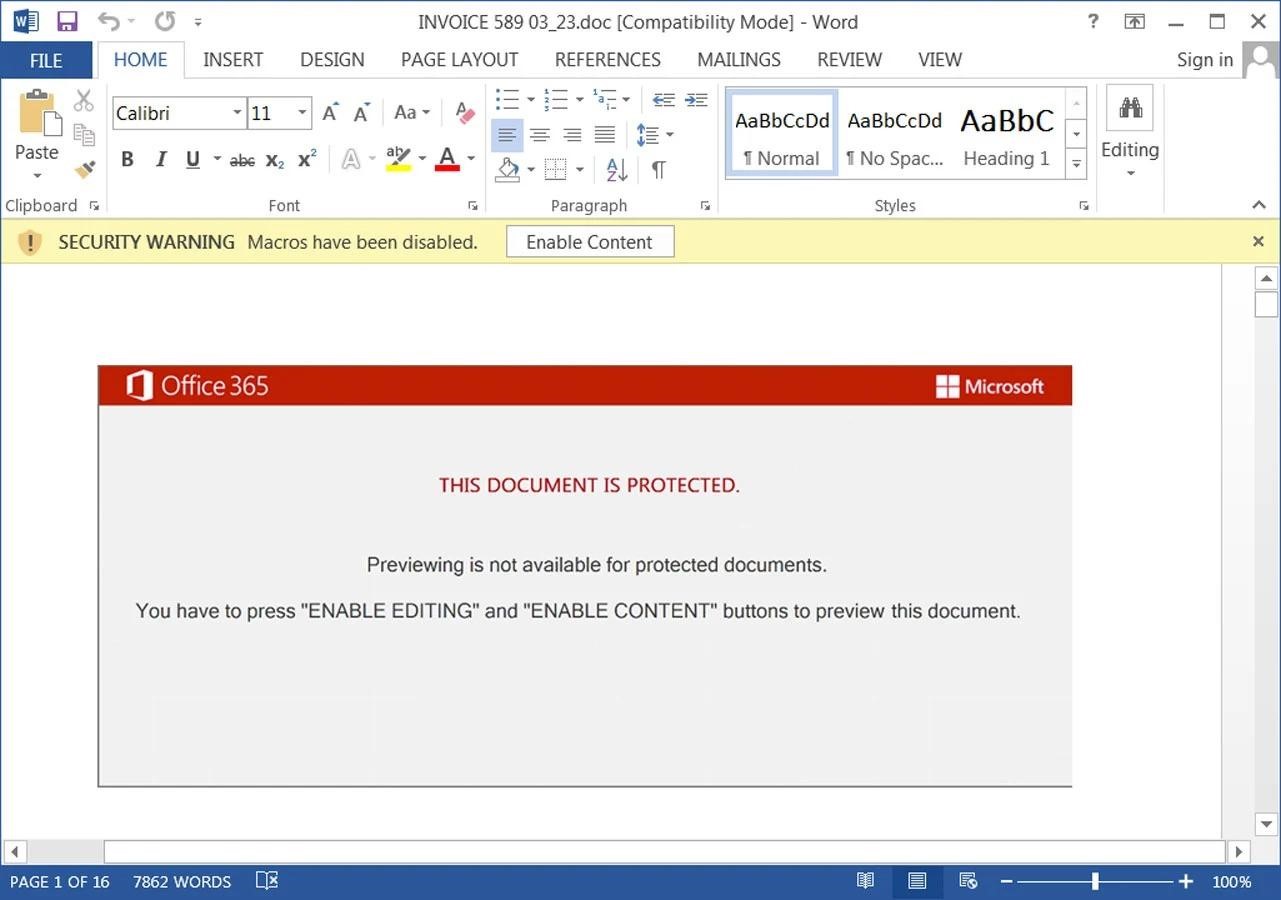
In fact, such documents contain many macros that download the Emotet loader as a DLL from compromised sites (mostly hacked WordPress blogs). After downloading, the malware will be saved in a folder with a random name in %LocalAppData% and launched using regsvr32.exe.
At the same time, the malware DLL file is also deliberately increased to 526 MB in order to prevent security software from identifying the file as malicious. As noted by Bleeping Computer, this method of evading detection works great: according to VirusTotal, so far the malware has been detected by only one provider of security solutions out of 64. At the same time, this provider defines the threat only as Malware.SwollenFile.
Once launched on an infected device, Emotet will run in the background, waiting for commands from its operators, which will likely result in additional payloads being installed. Although Cofense experts note that they have not yet observed any additional payloads, and now the malware seems to be simply collecting data for future spam campaigns.