Cryptocurrency is a rapidly changing world where people can make fortunes by exchanging digital assets. However, seasoned investors and newcomers alike are at risk of falling prey to crypto phishing scams. These scams exploit people’s trust and vulnerability and aim to trick them into revealing sensitive information or giving up their hard-earned crypto holdings.
What are cryptocurrency scams?
Crypto scams are investment frauds that can take many forms, from phishing scams to rug pulls. Since a central authority like a bank doesn’t regulate crypto’s blockchain technology, bad actors can easily exploit hopeful investors. That, actually, has made cryptocurrencies and all related topics an ideal harbor for different scams. Due to the lack of experience, people were prone to falling victims even to the least complicated schemes – leave alone tricky ones.
With time, cybercriminals become more sophisticated in their phishing techniques. Primary reason for that is the uprising of average folks’ knowledge – it just became not that easy to scam someone. They impersonate legitimate exchanges and wallets and use convincing social engineering tactics to gain unauthorized access to digital assets. These scammers use various social engineering methods to manipulate users’ emotions and create a sense of trust and urgency. It’s essential to be aware of these tactics and take the necessary measures to protect yourself.
Hot and Cold Wallets Difference
To assess the risks, let’s review the different types of wallets. First, it’s important to note that wallets do not hold the actual crypto assets. Instead, the blockchain records information about the support, while the wallet provides secure storage for the private (secret) key.
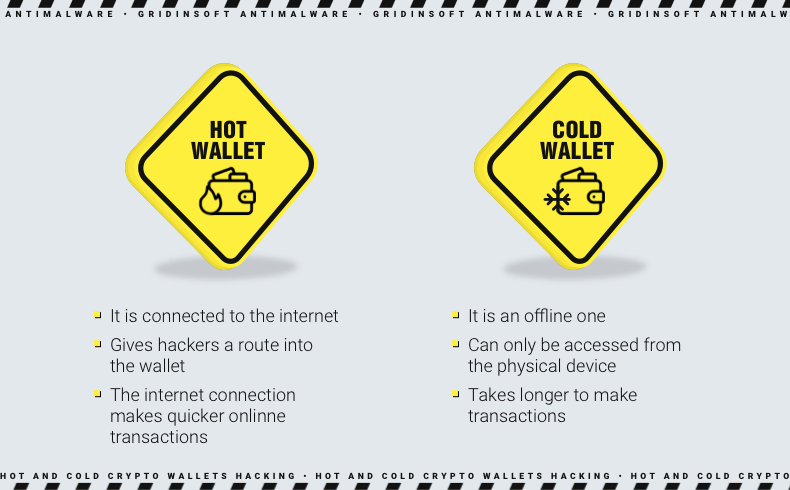
The “Hot” wallets.
A hot wallet is a cryptocurrency wallet that has constant internet access. It includes any online service that offers cryptocurrency storage, such as crypto exchanges and specialized apps. The keys in a hot wallet are stored encrypted on the server. These are online or custodial wallets offered by popular exchanges, including Binance and Coinbase.
The key can be used to sign a transaction on the blockchain anytime.
The “Cold” wallets.
In the case of a cold wallet, the keys are stored on a standalone device or as an alphanumeric sequence written on a piece of paper. A device solely for storing keys is known as a hardware wallet, while software wallets are applications designed to store keys on regular computers and smartphones.
Attack on “Hot” wallets
Many people use hot wallets to store their cryptocurrency because they are easy to create and convenient. However, cybercriminals often target hot wallets because they are frequently online and popular. Storing large amounts in hot wallets is not recommended due to their susceptibility to attacks. Although cybercriminals may use phishing techniques to attack hot wallets, their tactics are often simple and aimed at less experienced users.
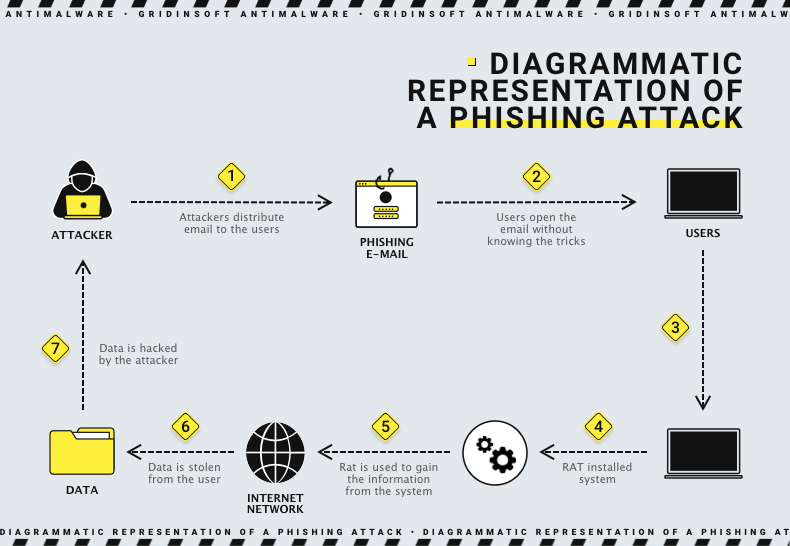
A standard method in crypto phishing scams is impersonating trusted entities, like cryptocurrency exchanges or wallet providers. The scammers send emails or messages that look like they come from these legitimate organizations, using similar branding, logos, and email addresses. Their goal is to trick people into thinking they are receiving a message from a trustworthy source.
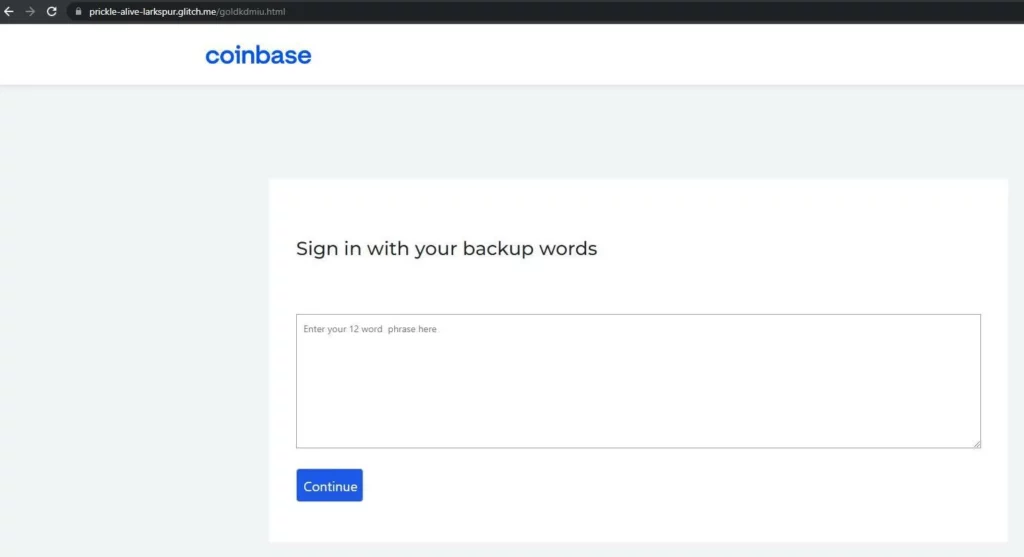
One common phishing scam targets users of hot wallets. Scammers will send emails posing as a well-known crypto exchange, asking users to confirm a transaction or verify their purse. Once the user clicks the link, they are taken to a page. Then they are asked to enter their seed phrase. A seed phrase consisting of either 12 or 24 words is required to regain access to a crypto wallet. This is the primary password for the wallet and should be kept secure. If the seed phrase is lost or given to scammers, the user risks permanently losing access to their wallet and compromising their account.
Scams that are straightforward and don’t involve software or social engineering tactics are usually aimed at people who are not tech-savvy. The form for entering a seed phrase usually looks simple, with just an input field and a logo for a cryptocurrency exchange.
Phishing attacks targeting cold wallets
Cold wallets seem to be more safe because they are not always connected to the Internet. However, it would be a mistake to assume that a hardware wallet can only be hacked by stealing or physically accessing it. As with hot wallets, scammers use social engineering techniques to access users’ funds. Recently, experts noticed an email campaign explicitly targeting hardware cold wallet owners.
A typical attack involves a crypto email campaign where the user is sent an email from a cryptocurrency exchange inviting them to participate in a giveaway of XRP tokens, the platform’s internal cryptocurrency. When the user clicks on the link, they will be directed to a blog page with a post outlining the “giveaway” rules. This post also includes a direct link for registration. Where scammers are already finding sophisticated methods to trick the user.
Fake support requests
Beware of crypto phishing scams where scammers pretend to be customer support reps from real cryptocurrency exchanges or wallet providers. They may send messages or emails to users, tricking them into believing there’s a problem with their account or a transaction that needs urgent attention. These scammers often provide a link to a fake support website or contact method, where users are asked to provide their login credentials or sensitive information. Stay vigilant, and avoid falling for these tactics.
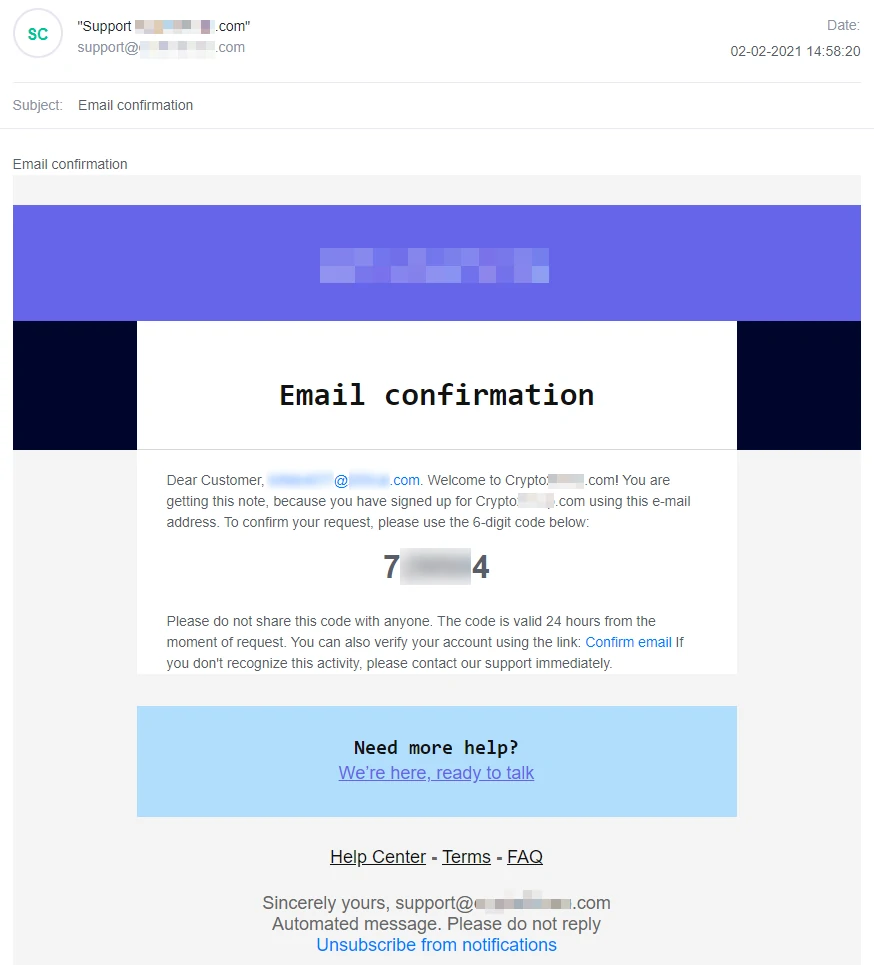
Scammers exploit users’ trust in legitimate customer support channels by pretending to be support personnel. They also capitalize on users’ eagerness to resolve issues promptly, which leads them to reveal their private information willingly. Scammers can then use this information for malicious purposes.
How to protect users from crypto-phishing
To stay safe while using cryptocurrency, there are measures users can take. One is enabling two-factor authentication, a helpful tool to prevent phishing scams from compromising their crypto accounts.
- Use of hardware or software authenticators. Hardware authenticators, or security keys, are physical devices that generate one-time passwords and provide an extra layer of security. Software-based authenticators, such as Google Authenticator, generate time-based codes on users’ smartphones.
- Be careful with links and attachments. Phishing scammers use a trick where they display a different URL text to what the actual destination is. To avoid falling for this, users can hover over the link to check for inconsistencies and suspicious URLs that may indicate a phishing attempt.
- Scanning attachments with antivirus. To protect your device and cryptocurrency accounts from malware, always be careful when downloading and opening attachments, particularly from unknown or suspicious sources. Attachments may contain harmful software, such as keyloggers or trojans, which can jeopardize security. To reduce this risk, scanning all attachments with trustworthy antivirus software is advisable before opening them.
- Keep software updated. It is crucial to keep the operating systems, web browsers, devices, and other software up to date to ensure the security of the user’s devices. These updates may contain security patches to address known vulnerabilities and protect against new threats.
As crypto phishing scams constantly change, users must stay current on the latest tactics and scams targeting the cryptocurrency community. Educating yourself on these techniques and staying informed about recent phishing incidents and security best practices can help keep you safe. To stay informed about phishing scams, security vulnerabilities, and how to protect your crypto assets, it’s essential to follow trustworthy sources that provide accurate information and alerts.




