Palo Alto Networks warns its customers regarding a vulnerability in their PAN-OS, that leads to command injection. Residing in their GlobalProtect feature, and requiring some specific configurations, this flaw still manages to hit the max CVSS score of 10/10. Fixes for the issue are already in development, the company says.
PAN-OS Command Injection Vulnerability Exploited in the Wild
On April 12, 2024, Palo Alto Networks released a report regarding the CVE-2024-3400 – a critical vulnerability in their PAN-OS. This operating system is a basis for the company’s firewall solutions, which is in turn a rather popular option for network protection among companies around the world. By exploiting the flaw, adversaries get the ability to execute arbitrary code with maximum (root) privileges. This explains the extremely high CVSS score, as well as the fact that cybersecurity is set abuzz about it.
The worst part about this flaw is that it is already exploited in real-world attacks. Palo Alto Networks do not mention any specific attack cases, but the fact that the vendor confirms this makes the fact hardly doubtful. The company also specifies that for the successful exploitation, the affected PAN-OS instance should have two things configured: device telemetry feature and the GlobalProtect gateway.
Arbitrary code execution vulnerabilities may be used for both gaining initial access and performing lateral movement. In the case of its residence in the firewall software, the result may lead to misconfiguration of the network protection or its complete disabling. The former is most probable though, as it allows for creating a stealth communication channel(s) with the infected environment.
Affected Versions and Patches
Palo Alto Networks confirms the vulnerability being present in the grand total of 3 PAN-OS versions – 10.2, 11.0 and 11.1. Earlier versions, as well as some of the auxiliary software used together with the firewall are not affected. Problem is – there are no patches available for the flawed versions at the moment.
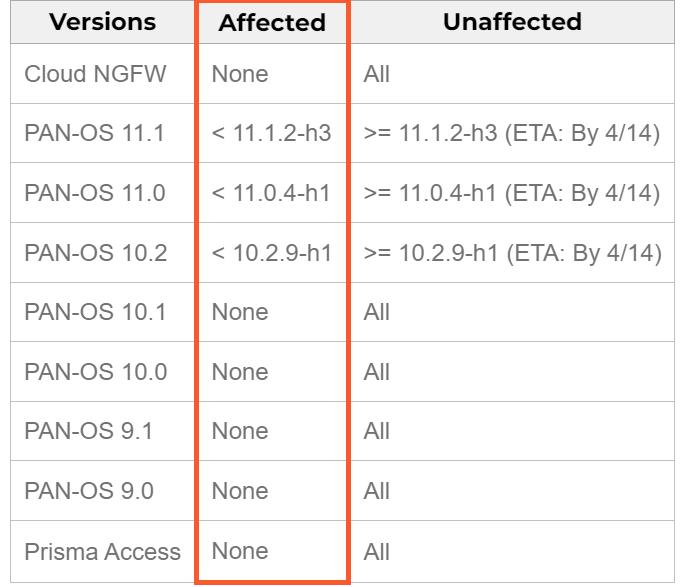
The company promises to release corresponding fixes for all the vulnerable versions on April 14, 2024. They also offer the possible mitigation of the issue, through disabling the device telemetry feature. This will diminish the potential impact of a successful exploitation. For the subscribers of their Threat Prevention service, the company provides the ability to block the potential exploitation cases.
Protecting Against Vulnerability Exploitation
Any software may contain vulnerabilities, and even the top-notched solutions from worldwide known vendors are not an exclusion. There are no soothsayers among us, so predicting which program will have a vulnerability is rather difficult. For that reason, reactive measures are the best possible way to avoid the attacks that use vulnerability exploitation.
Stay in touch with the latest security news. Whenever a flaw in widely used software becomes public, it hits the titles of all cybersecurity newsletters. Thing is – the vast majority of vulnerability exploitation happens after the information about it becomes public. Rapid reaction to the new discovery and patching the flaw as the instruction says will most definitely secure your environment.