Cloak ransomware is malware that encrypts user data and demands ransom. While some ransomware targets giant corporations, this specific instance mostly caters to small and medium-sized businesses in Europe. In this post, I will discuss this threat in more detail, show how to remove the malware and explain the ways to recover the encrypted files.
Cloak Ransomware Overview
Cloak is a highly sophisticated ransomware strain designed to encrypt user files and demand ransom for decryption. It primarily targets small to medium-sized businesses in Europe, with Germany as a key focus. The group has also expanded its operations to countries in Asia. It targets various sectors, including healthcare, real estate, construction, IT, food, and manufacturing.
Once executed, it systematically scans the system for files to encrypt, appends a “.crYpt” extension to them, and leaves a ransom note titled “readme_for_unlock.txt.” This note provides instructions for victims on how to regain access to their files by purchasing a decryption tool.
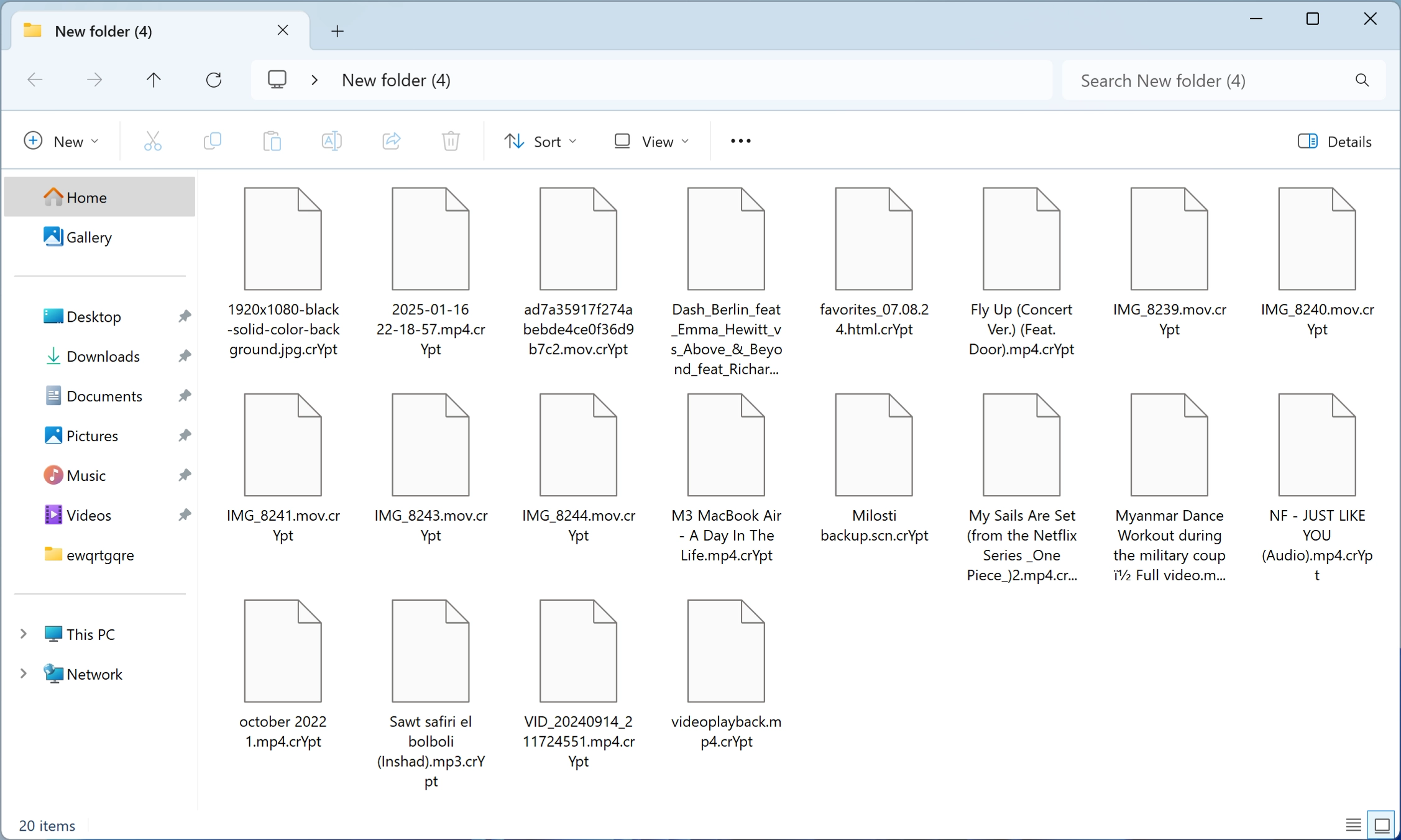
A notable aspect of Cloak ransomware is its association with a Darknet website with data leaks. This suggests that it might also engage in double extortion. While the ransom note does not explicitly mention data theft, the presence of a leak site indicates that stolen data could be exposed if the ransom is not paid. Additionally, this ransomware employs evasion tactics to disable security tools. It also removes backups, further complicating recovery efforts.
Ransom Note Overview
The ransom note, “readme_for_unlock.txt,” informs victims that their files have been encrypted and that decryption is only possible by purchasing a tool from the attackers. The exact ransom amount is not specified in the note, but must be paid in Bitcoin. Victims are given the option to decrypt two small files for free as proof that decryption is possible.
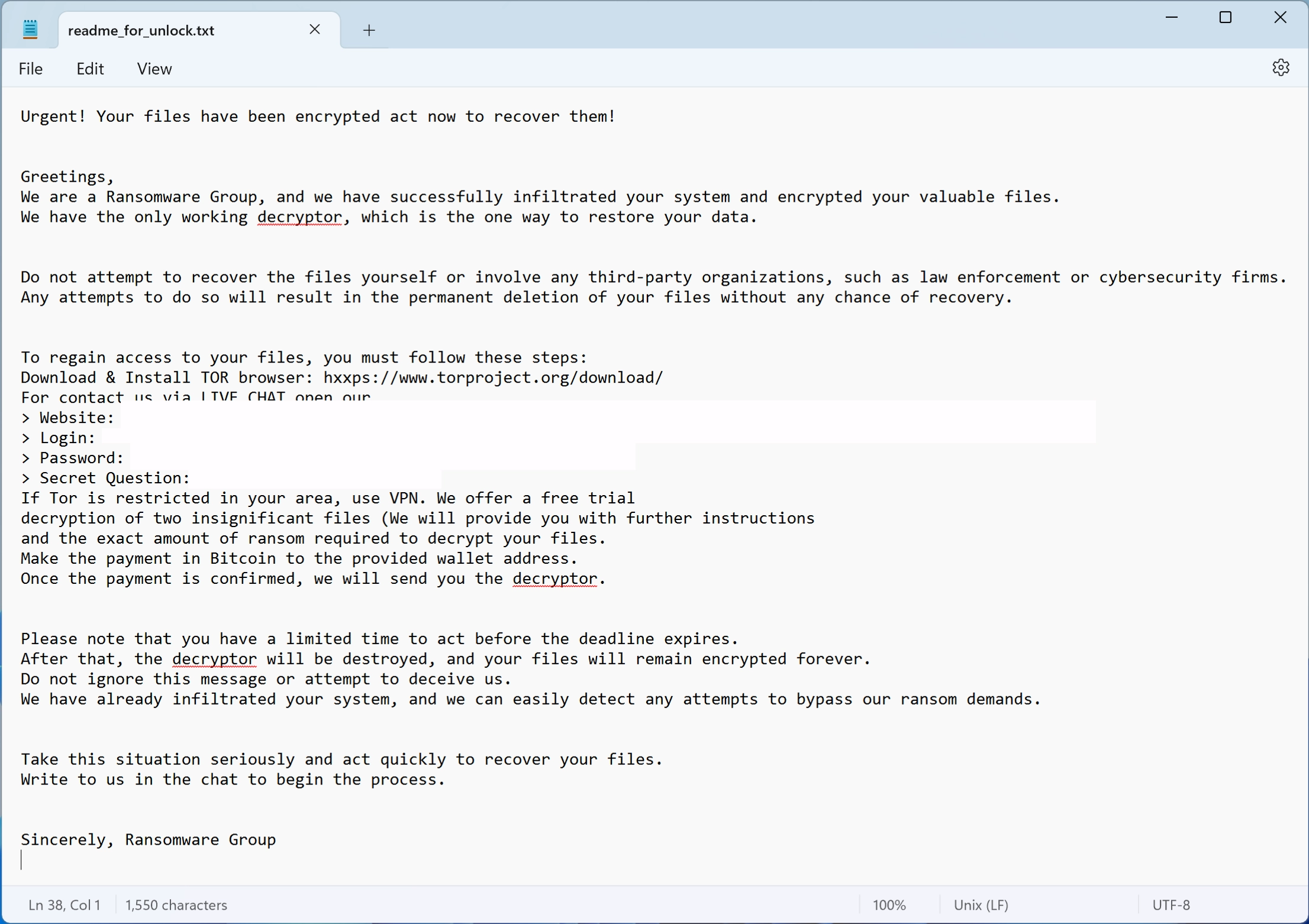
The note also warns against seeking help from cybersecurity experts or law enforcement, claiming that doing so will result in permanent data loss. This is a common intimidation tactic used to dissuade victims from attempting alternative recovery methods. Additionally, the note provides a link to a Tor-based contact page.
How Does It Work?
Cloak ransomware follows a structured process to maximize damage. Based on the analysis, this ransomware is derived from the leaked Babuk source code. It starts by identifying and queuing files for encryption, specifically avoiding system-critical folders like “Windows” and “ProgramData.”
The ransomware supports two encryption modes: full encryption for smaller files and intermittent encryption for larger ones. This selective encryption approach increases efficiency while ensuring that files remain unusable without the correct decryption key.
The encryption process relies on a combination of Curve25519 for key exchange and HC-128 for encrypting file contents. Cloak generates a unique 32-byte private key for each infection, derives a public key using Curve25519_donna, and then creates a shared key to encrypt files. Encrypted files have a 0x48-byte footer structure appended to them, storing cryptographic details essential for decryption.
To enforce persistence, Cloak modifies the system registry, ensuring that it runs on every startup. It also deletes volume shadow copies to prevent file recovery. Additionally, it modifies system policies to block users from logging out, shutting down, or accessing the Task Manager. Furthermore, the ransomware sets a custom wallpaper displaying the ransom demand, adding psychological pressure to the victim.
How to Recover Cloak Ransomware Files?
Before all, it is crucial to eliminate Cloak ransomware from the system. As long as the malware remains active, any newly created or restored files may be re-encrypted. The best approach is to disconnect the infected system from the internet and boot into Safe Mode. From there, running a full system scan with a GridinSoft Anti-Malware, that can help detect and remove the ransomware.
Manual removal is not recommended, as Cloak modifies system settings and registry keys. Additionally, after removal, users should restore their systems from a clean offline backup if available. Ensuring that all security updates are installed and using strong, updated passwords can help prevent reinfection.
Can I Recover Files?
Unfortunately, decryption without the attacker’s private key is virtually impossible due to the strong cryptographic algorithms used by Cloak. While paying the ransom might seem like an option, I would strongly advise you not to do this. Many victims who pay never receive the promised decryption key, and funding cybercriminals only encourages further attacks.
If a backup exists on an external device or cloud storage, or conversations in messengers, files can be restored from there. While this does not guarantee a full file recovery, you will likely be able to get back at least some files. Having 30% of your files recovered is way better than having none at all.
For users without backups, there may be a slim chance of recovery if security researchers discover a flaw in Cloak’s encryption implementation. Regularly checking cybersecurity forums and trusted security researchers’ websites may provide updates on potential decryption solutions.
As I said at the beginning, this grouping steals files before encrypting them. If the ransom is not paid, the attackers publish the files on their Data Leak Site. So users can find their files for free. Meanwhile, practicing safe browsing habits and avoiding suspicious email attachments can help prevent future infections.