“Your Account Has Been Locked”: Top 5 Signs of a Phishing Scam
The topic of our article will be how to understand that you have become a victim of a phishing attack. Below, you will learn what is discussed in our main…
Cybersecurity Researchers Discovered a New Phishing Kit targeting PayPal Users
Akamai has identified a new phishing kit that is being installed on hacked WordPress sites and targets PayPal users. The malware tries to steal the personal information of the victims,…
Microsoft Releases PoC Exploit to Escape MacOS Sandbox
Microsoft has detailed a recently patched vulnerability affecting Apple operating systems and published a PoC exploit to escape the macOS sandbox. If successfully exploited, this bug allows to leavei the…
5 Security Mistakes You’re Making On Social Media
Leading digital life on various social media platforms can sometimes be a challenging task. And the challenges come not only from the efforts of maintaining presentable digital selves. It is…
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It Before considering how to prevent DDoS attacks, we first consider this definition. Because without understanding what is at stake, it will…
100% Disk Usage Windows 10: How to Fix Disk Issue
100% disk usage is a widespread problem among Windows users that has several possible origins. Having your disk 100% loaded is unhealthy and leads to PC usage problems. Let’s figure…
U2K Ransomware Strikes, Thousands Of Victims
U2K ransomware, probably the rising star on the ransomware arena, appeared on July 10, 2022. It instantly infected a huge number of users and keeps spreading, despite the massive alarms…
Emsisoft Released a Free Tool to Decrypt Data Corrupted by AstraLocker and Yashma
Emsisoft has released a free decryption tool for files affected by AstraLocker and Yashma ransomware attacks. Let me remind you that last week AstraLocker operators announced that the malware was…
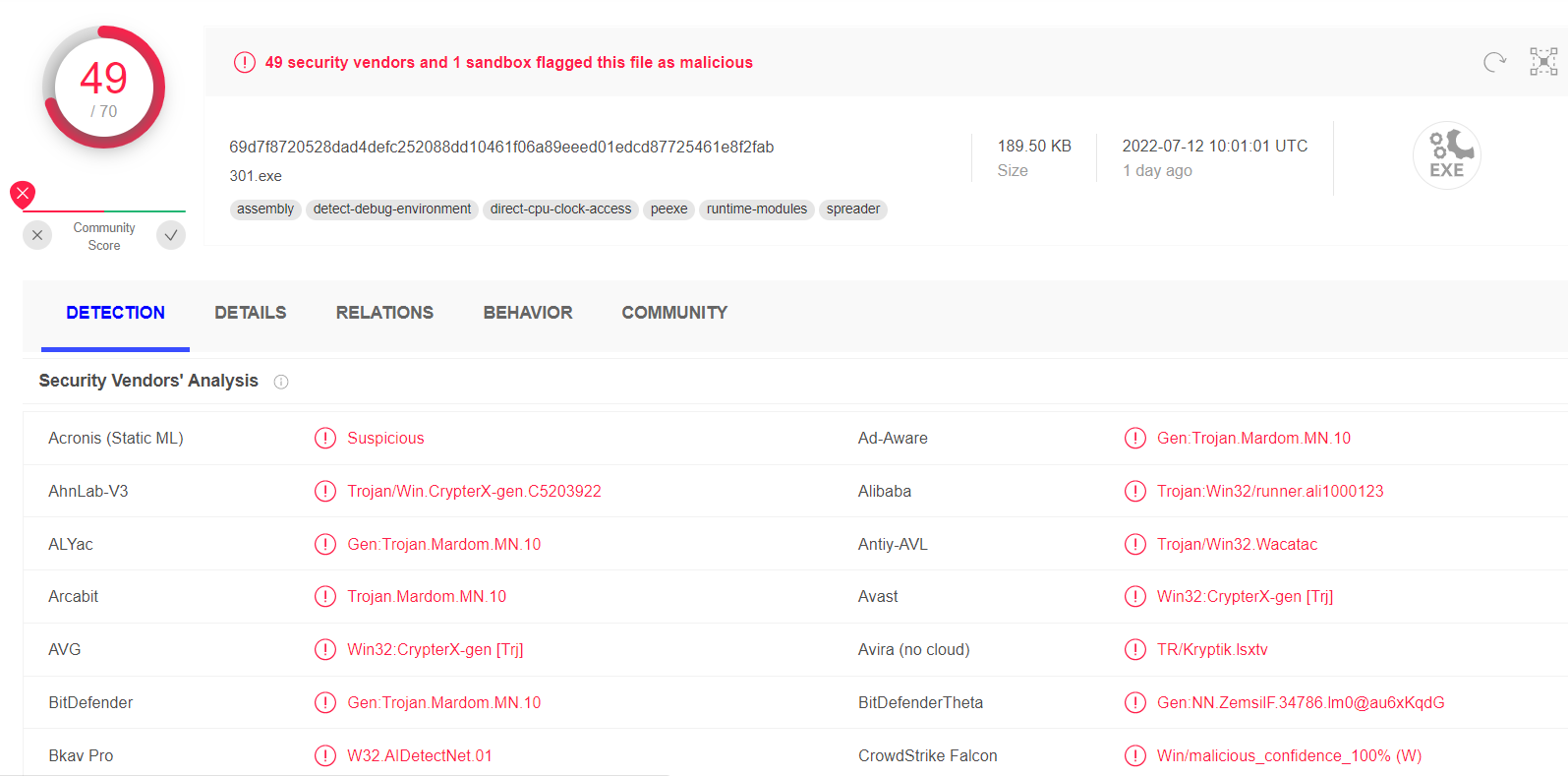
How to Report a False Positive Detection?
Gridinsoft is an antivirus software company that provides powerful solutions for detecting and removing malware from computers. However, sometimes our software may generate false positive detections, which can frustrate users.…
Types of Computer Virus
Computer viruses can steal and facilitate the dissemination of your confidential information, and reduce your computer performance and any other threats. To understand what viruses are and how to get…
TrickBot Hack Group Systematically Attacks Ukraine
IBM Security X-Force experts noticed that from the very beginning of the full-scale Russian invasion, the TrickBot hack group “systematically attacks” Ukraine, which has not been observed before. It is…
Bandai Namco Hacked, ALPHV Group Claims
On Monday, June 11, 2022, the information about the cyberattack on the video game publisher Bandai Namco appeared. Reportedly, a novice cybercrime group BlackCat/ALPHV ciphered the company's files and leaked…