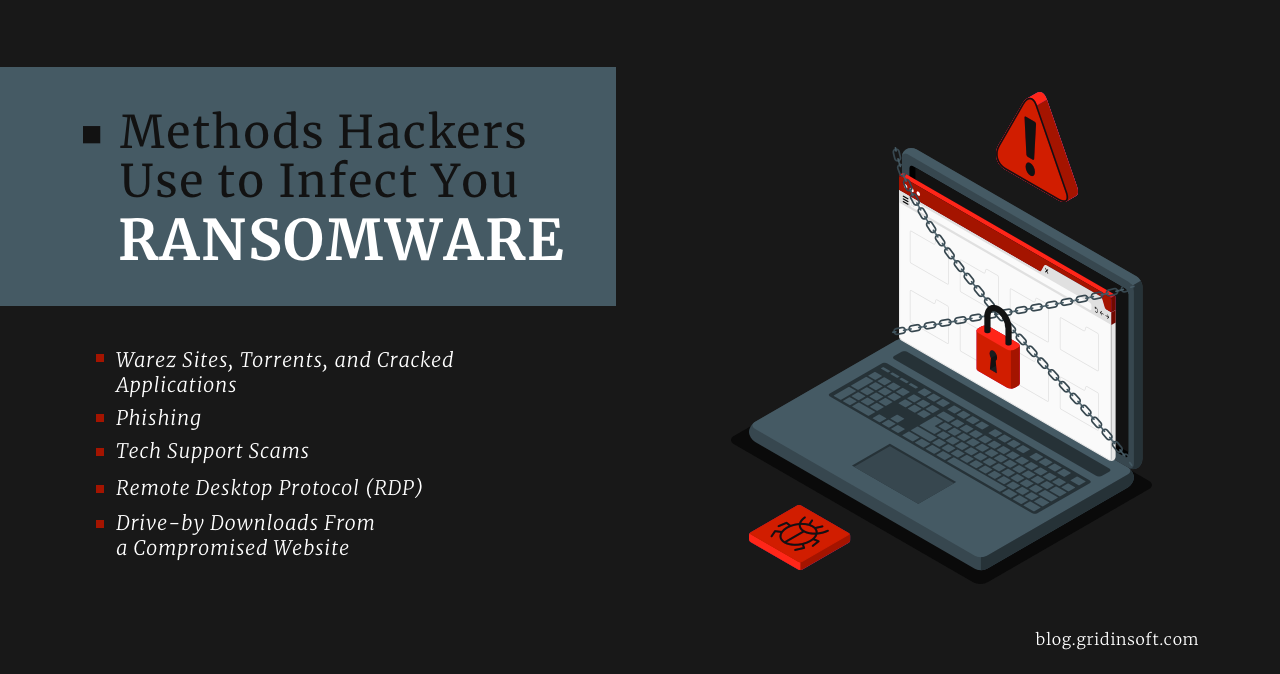
Methods Hackers Use to Infect You Ransomware
Ransomware hits the headlines almost daily. And most incidents target large corporations with enough capital to justify the attack. But sometimes ordinary people get infected as well. Some attackers choose…
Stores Are under Attack due to 0-Day Vulnerability in PrestaShop
Hackers exploit a 0-day vulnerability in the open-source e-commerce platform PrestaShop and introduce web skimmers to websites designed to steal sensitive information. Last Friday, the PrestaShop team issued an urgent…
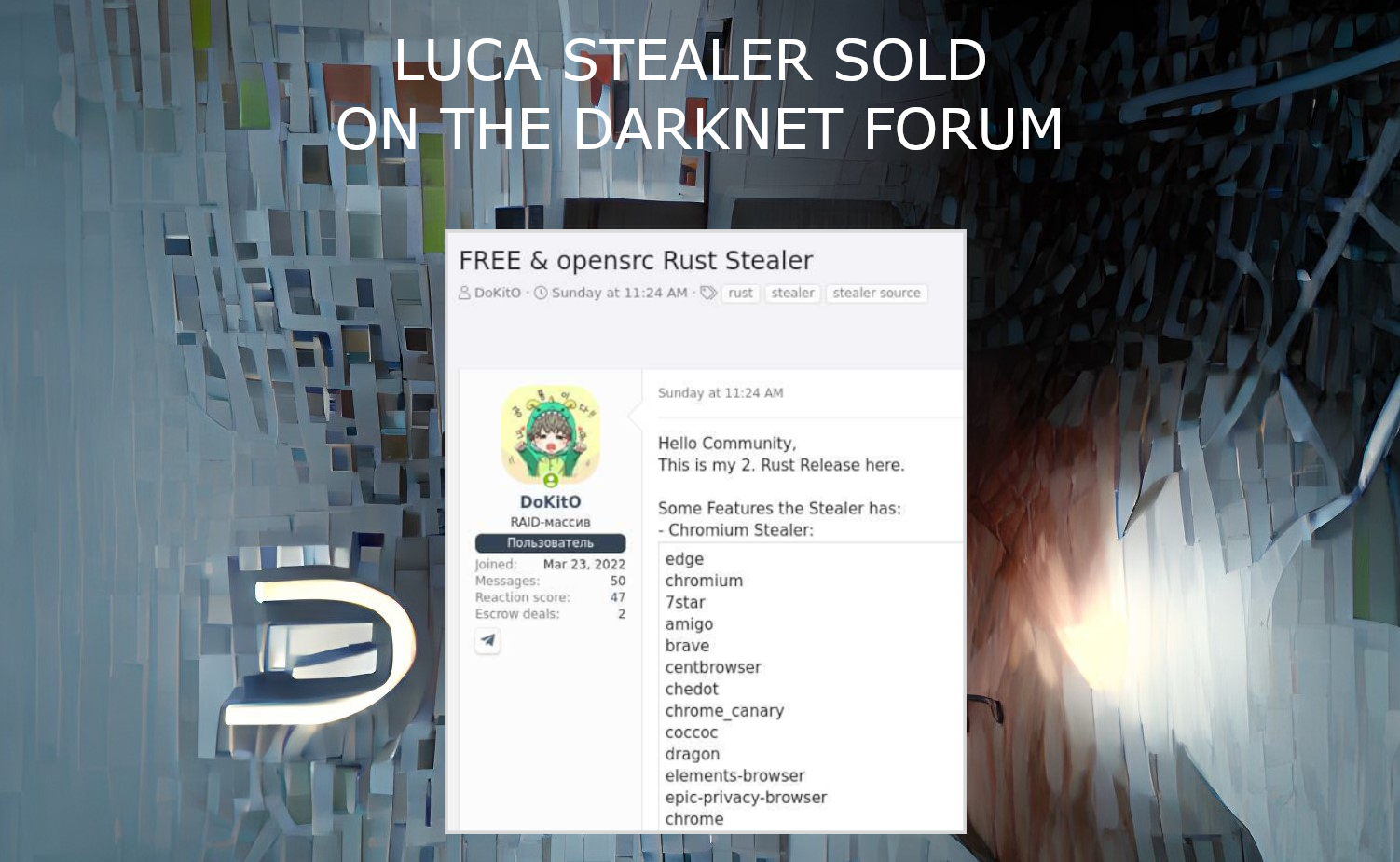
Luca Stealer Source Code Published In The Darknet
Luca Stealer, an omni-purpose stealing malware programmed on Rust, was published on the Darknet forum in recent days. The source code of a well-done stealing tool is now available for…
New Linux Malware Lightning Framework Installs Backdoors and Rootkits
Intezer analysts call the new Linux malware Lightning Framework a real "Swiss knife" because of its modular architecture, as well as the ability to install rootkits and backdoors. Let me…
Can Someone Track My Device When Location Settings Off?
Any smartphone already has built-in location tracking services. At the beginning location tracking was created for navigation, but it was later used for other purposes. This feature is very convenient…
How To Know If Your Phone is Hacked?
If your phone stopped working correctly and started showing obvious performance errors, then something is wrong. If you notice that your smartphone has begun to turn itself off or on,…
Chrome 0-day Vulnerability Used to Attack Candiru Malware
Avast has discovered that DevilsTongue spyware, created by Israeli company Candiru, exploited a 0-day vulnerability in Google Chrome to spy on journalists and others in the Middle East. The vulnerability…
Candiru Malware Uses 0-day Vulnerability In Chrome
Following Microsoft, Google and Citizen Lab, another revelation came from Avast researchers. They discovered that the Israeli spyware Candiru used a 0-day vulnerability in Google Chrome. Their main target was…
Spam Phone Calls Revenge: Prevent Spam Risk Phone Calls
Statistics show that an average of 1,900 spam calls are made every second. Given recent statistics about it, it is clear that it is another problem in the head of…
Fraudsters Are Running a Malicious Advertising Campaign through Google Search
Malwarebytes, an information security company, has discovered a large malicious campaign that skillfully uses ads and Google search. A phishing campaign using Windows tech support is spreading through Google Ads.…
Fake DDoS App Targets Pro-Ukrainian Hacktivists
Google Threat Analysis Group (TAG) specialists reported that the Russian-speaking group Turla (aka Waterbug and Venomous Bear) created a fake Android application, allegedly designed to carry out DDoS attacks and…
CloudMensis Malware Attacks MacOS Users
ESET experts have discovered the CloudMensis malware, which is used to create backdoors on devices running macOS and subsequently steal information. The malware received its name due to the fact…