How To Make Google Chrome Faster 2024
Have you ever noticed Google Chrome running much slower than usual? And productivity is markedly lower than it used to be. For example, after a Windows update, Google Chrome starts…
Google Tricks For Better Searching
Google is an iconic search engine. You use it every day, as well as 8.5 billion people who are connected to the Internet, use it, too. But there are a…
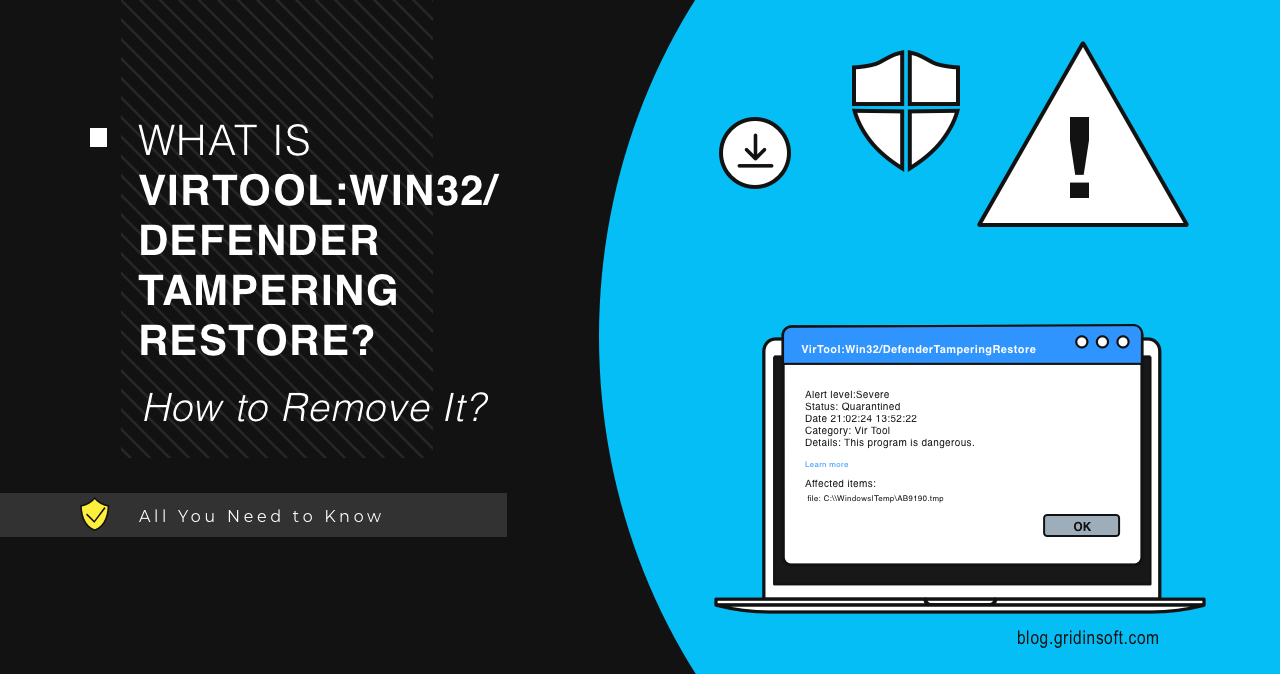
VirTool:Win32/DefenderTamperingRestore
VirTool:Win32/DefenderTamperingRestore is the name of the Microsoft Defender detection of a malicious element present in the system. Usually, it marks a thing that can weaken the system's security and make…
Dell Hacked, 49 Million Users Exposed
On Friday, May 10, Dell Technologies released a claim regarding the massive data leak that happened in their internal network. Data breach allegedly touches up to 49 million users, and…
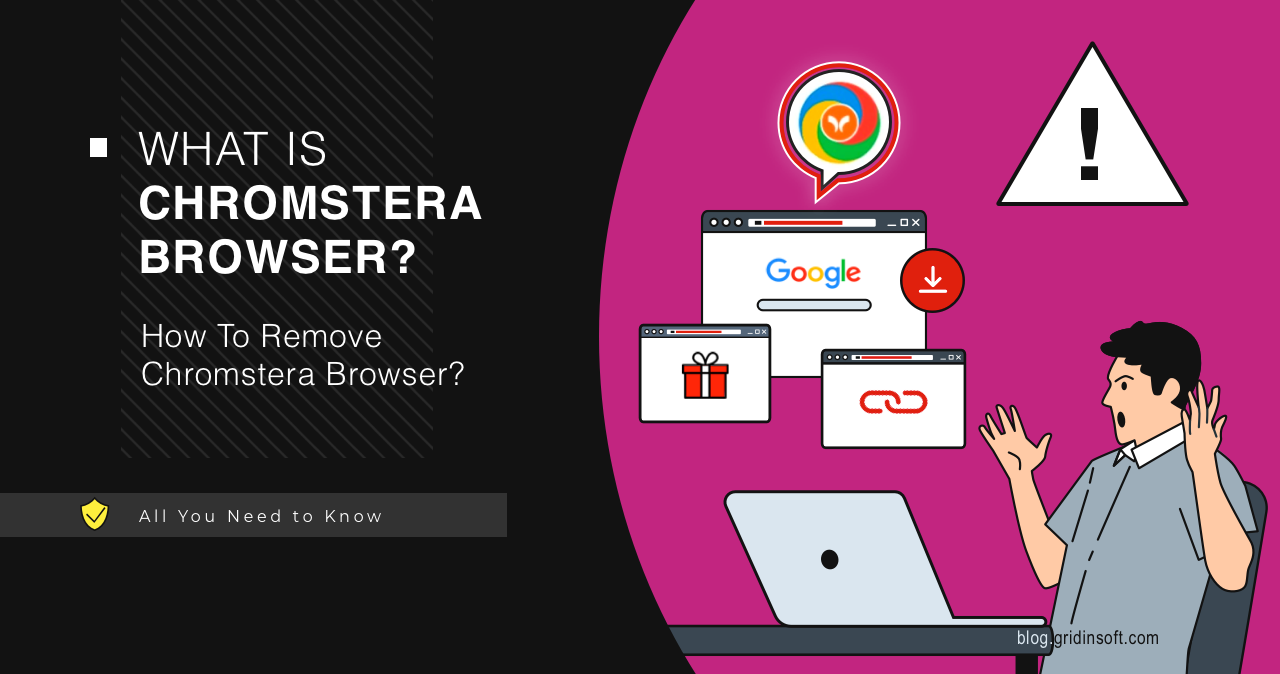
Chromstera Browser
Chromstera Browser a rogue browser that mimics Google Chrome, and spams ads, redirects search queries and collects data about the user's online activity. Like the majority of such software, it…
Reset Browser Chrome, Opera, Edge, Firefox and Safari to Default
Browser performance issues, unwanted redirects, and strange behavior are common signs that your browser settings may have been compromised. Resetting your browser to default settings is an effective way to…
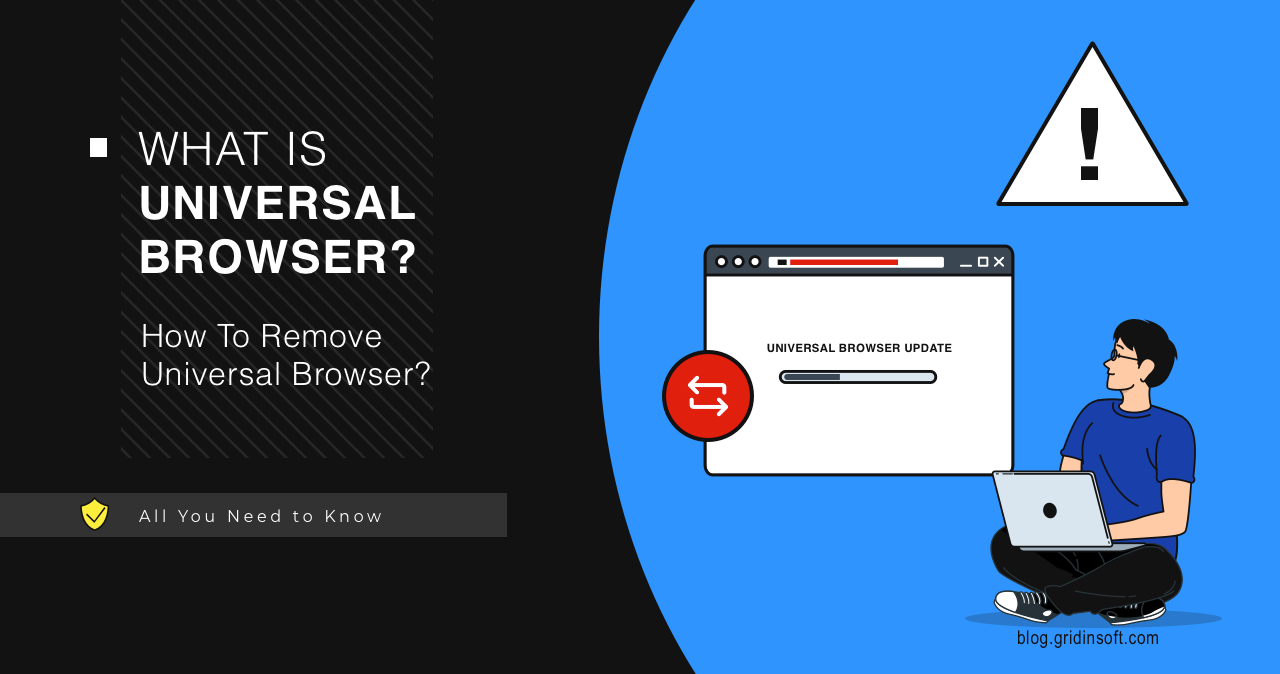
Universal Browser
Universal Browser is a name of a browser that users spectate in a strange update window that pops up in the system, occasionally reporting an update error. This window is…
LockBit Leader Identity Revealed, NCA Publishes More Data
On May 7, 2024, UK National Crime Agency published the detailed dossier on the LockBit ransomware group’s leader. Dmitry Khoroshev, known as LockBitSupp, leads one of the most vicious ransomware…
Wave Browser
Wave Browser is an unwanted browser application that tries to look as a yet another Chromium-based project. Although it performs its function, according to users' reviews, there are more problems…
eBay Scams
Among the vast amount of online shopping platforms, eBay stands off as a trusted and well-known one. Such a massive popularity obviously attracts fraudulent activities, causing eBay scams to appear.…
PUA:Win32/Conduit
PUA:Win32/Conduit is a potentially unwanted application that performs suspicious activity with the browser. It changes the homepage and search engine and installs extensions. It is distributed through hacked software or…
GitHub Vulnerability Exploited in the Wild, CISA Notifies
GitLab has a critical vulnerability that affects all authentication mechanisms. Without two-factor authentication, users are at significant risk. The vulnerability is currently fixed, and users are recommended to update to…