How to Remove Cryptocurrency Mining Malware from Windows 11: Complete Guide
If you're seeing cryptocurrency mining malware detected by your antivirus, don't panic. Your Windows 11 computer is running slow. The CPU fan won't stop spinning. You see processes eating up…
Virus Protection Hints & Advices in 2023
Tired of your OS Widows behaving strangely and slowing down suddenly? I can understand the pains of removing the viruses infecting your system and then sustaining the damage done by…
End of support for Adobe Flash caused interruptions in the Chinese railway system
As you know, back in 2017, Apple, Facebook, Google, Microsoft, Mozilla, as well as Adobe itself announced the end of support for Adobe Flash. The technology was officially "killed" on…
New worm for Android spreads rapidly via WhatsApp
ESET security researcher Lukas Stefanko reported a new malware: he said that a new worm for Android automatically spreads through WhatsApp messages. The main purpose of malware is to trick…
Researcher Found Three Bugs Allowing Hacking Amazon Kindle
Researcher Yogev Bar-On from Israeli consulting firm Realmode Labs talked about his KindleDrip attack technique and three Amazon Kindle bugs (already fixed) that underlie it. For discovery of these vulnerabilities…
Chinese hack group Chimera steals data from air passengers
According to reports of cybersecurity researchers, the Chinese hack group Chimera is stealing data from air passengers. The NCC Group and its subsidiary Fox-IT have published a joint report on…
Raindrop is another malware detected during the SolarWinds hack
Symantec specialists detected Raindrop malware, which was used during the attack on SolarWinds along with other malware. According to the researchers, Raindrop was used by cybercriminals in the last stages…
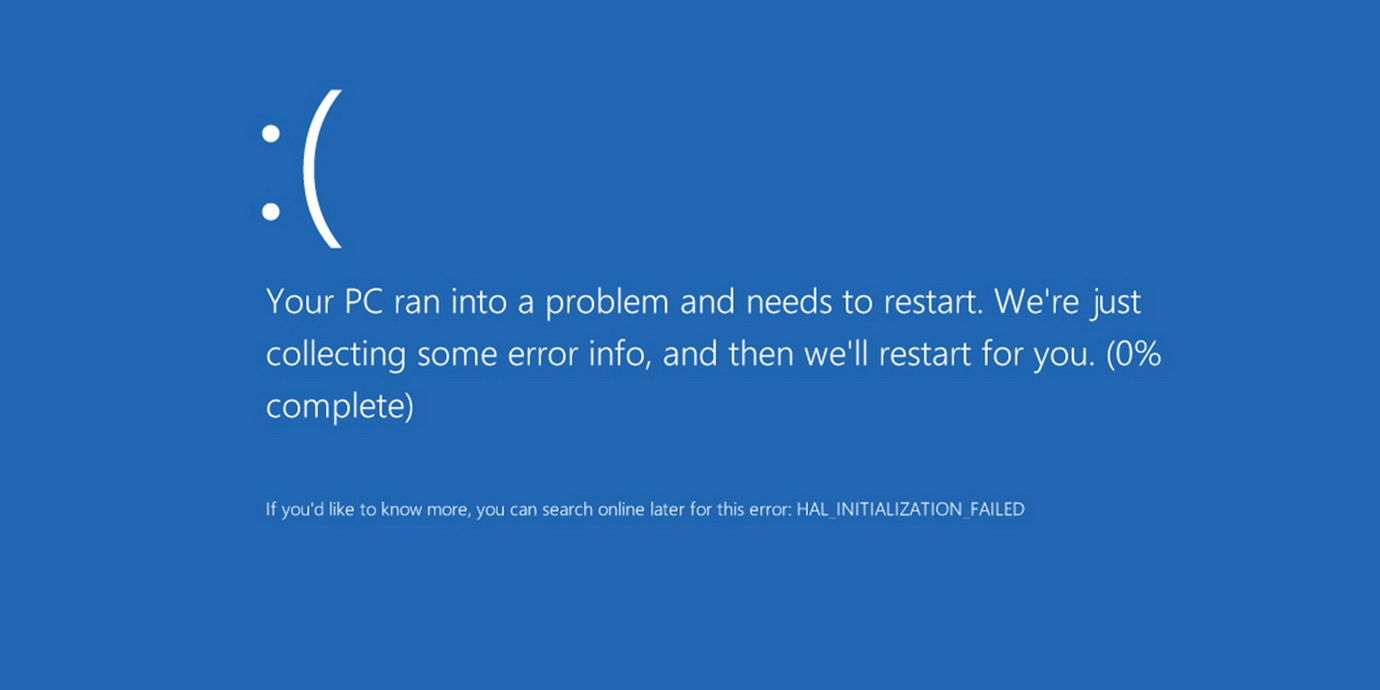
Windows 10 bug causes BSOD when opening a specific path
A bug in Windows 10 causes the OS to crash with a blue screen of death (BSOD) if the user tries to open a specific path in the address bar…
Hackers majorly use Microsoft and DHL brands in phishing attacks
Hackers majorly use the Microsoft and DHL brands in phishing attacks. In Q4 2020, cybercriminals used more brands from the tech industry, followed by shipping and retail businesses. Information security…
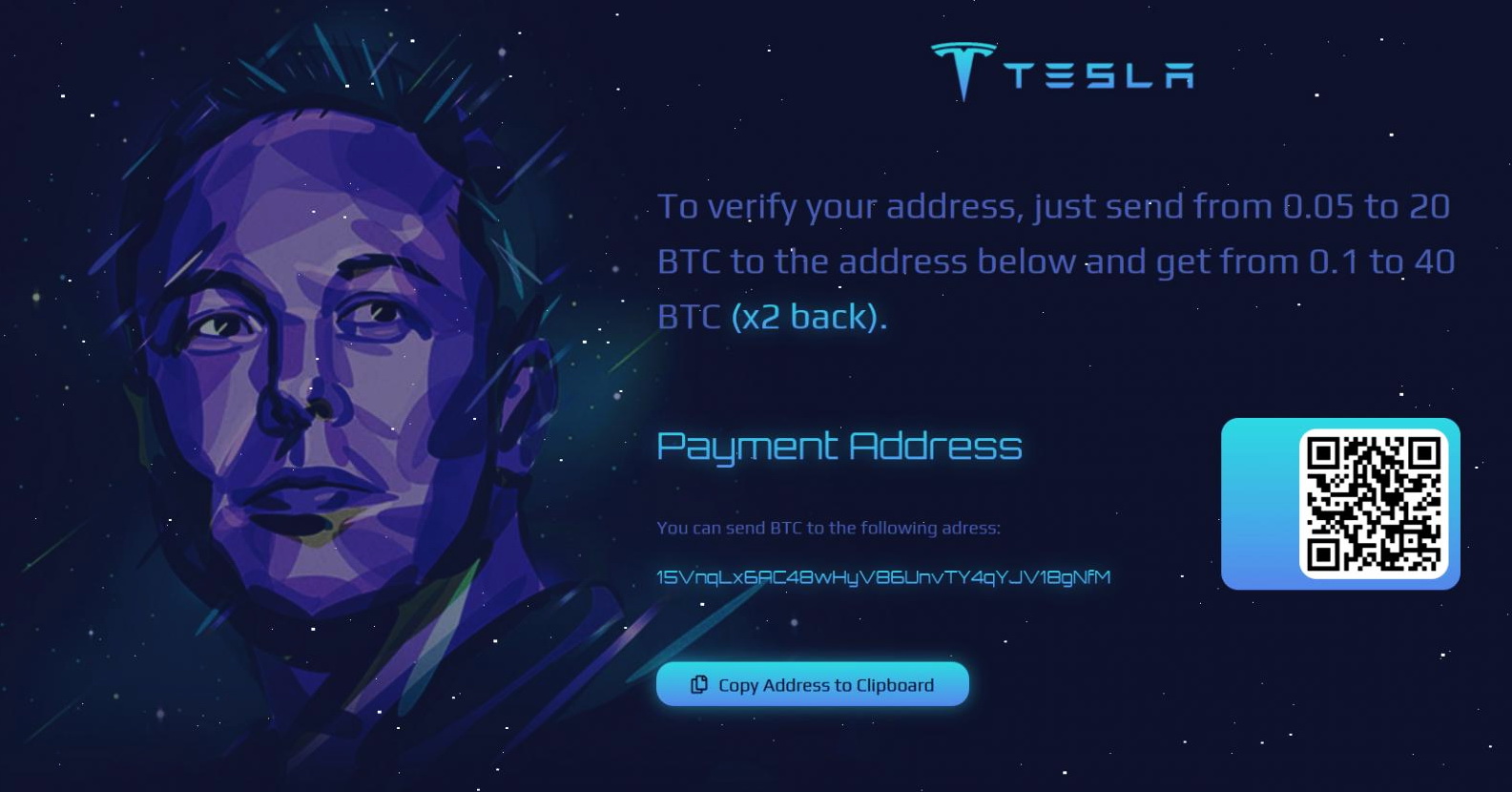
Fake cryptocurrency giveaways on behalf of Elon Musk brought scammers $580,000
The media have repeatedly written that scammers sometimes impersonate famous people. For example, last year, cybercriminals arranged fake giveaways of cryptocurrency on behalf of Elon Musk or SpaceX that had…
Google experts exposed sophisticated hacking campaign against Windows and Android users
Google published a large report detailing how they exposed a sophisticated hacking campaign that was discovered back in early 2020. The campaign targeted Android and Windows users, and attackers exploited…
Experts discovered SolarLeaks website with data stolen in a recent massive hacker attack
Bleeping Computer reports the discovery of the SolarLeaks website (solarleaksnet), where unidentified individuals claim to be selling data allegedly stolen from SolarWinds, Microsoft, Cisco, and FireEye during a recent supply…