Azurestaticapps.net is a selection of pages registered on genuine Microsoft hosting, that try scaring the user by false malware infection claims. In fact, it is nothing but intimidation that ends up with a call to fake tech support, that eventually steals personal information or installs unwanted software. In this post, I will debunk all the elements of that fraudulent site, and explain how to avoid them in future.
Azurestaticapps.net Scam Website Overview
As I’ve mentioned in the introduction, Azurestaticapps.net is not about a sole page, but rather a whole network of scam sites, operated by the same group of fraudulent actors. They use genuine Microsoft Azure hosting as a way to get better disguise and organize the operations. All of them designed for making users believe their system is infected with viruses, and Microsoft thus locked the computer and now asks to contact their hotline. Here is how it typically looks:
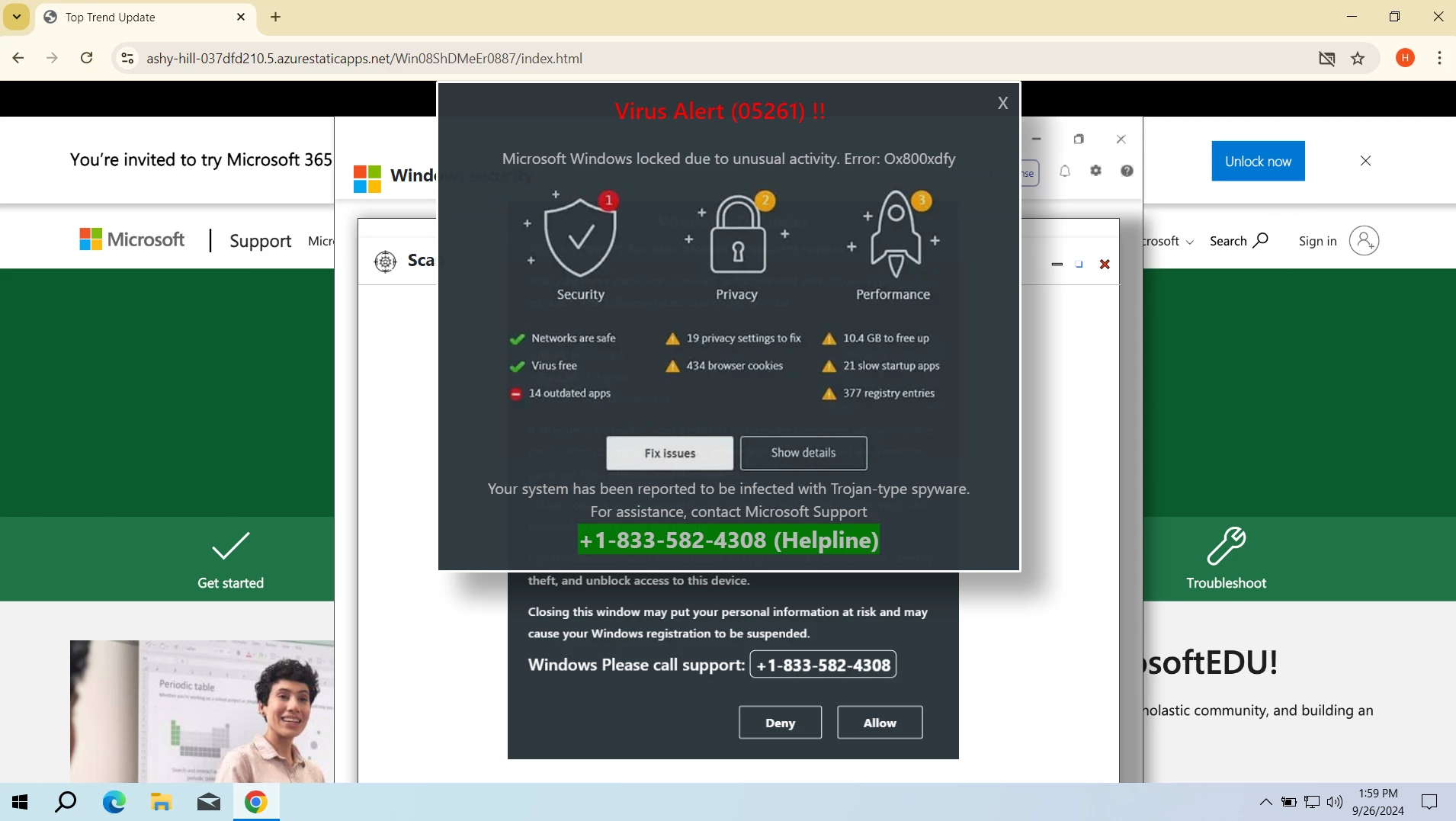
To make the victim believe everything is real, scammers not only parody the visual style of Microsoft sites, but also launch a scary robotic voice message that repeats the content of the banner. Once you click the site, it extends into a full screen mode and blocks all the typical ways out, including pressing the Esc button. This is what creates the sense that there’s no way out, pushing the victim to follow the instructions from the banner.
And these instructions are what leads the user to the main part of the scam – a call to a pseudo tech support. The specified number differs from one site to another, but they are essentially the same: a US number that redirects the call to a scam call center somewhere in India or another Asian country. There is a whole infrastructure built around these fake support scams, that was at one point disrupted by the FBI, but fraudulent activity is back up again.
Azurestaticapps.net Fake Tech Support Contact
People that pretend to be tech support agents of Microsoft in fact work with one single purpose: force the user into installing questionable software. They will either instruct the caller to install a “fix tool” by themselves or ask for providing them remote access to the system to do this by themselves. As a result, the user ends up with a non-existent problem solved and a dodgy program running in their system.
The key danger of all this is, in fact, not only forcing users into this call by fake alerts, but this program that gets installed in the end. They range from fake antiviruses to “system tweakers” that can cripple system stability and performance, and quite often dare to ask to buy a license to keep using them. Fake support and the Azurestaticapps.net sites are, in fact, the main ways for such applications to propagate to user systems.
How did I get to the Azurestaticapps.net?
As you may already guess, you won’t typically get to sites like Azurestaticapps.net in a normal way, i.e. through search results or regular links on other sites. Instead, they rely on spontaneous redirects from shady websites, particularly ones that have illegal content of some sort. Cracked games and programs, pirated movies, cheats or some strange game mods – offerings like this are quite often synonymous with a fishy site with redirects or outright malware.
In certain cases, fake virus alarm pages are getting opened because of adware activity. Typical signs of this situation include repeated appearance of this or similar scams in absence of any user interaction. In simple words, if strange things happen with your browser or system, while you are not doing anything, that may be the sign of malware presence.
Scan your system for malware
The best way to clear things up is to use a dedicated security software. GridinSoft Anti-Malware will check the entire system and delete all the detected malicious programs. A Full Scan will be the best option for that case: this way, the program will check even the most remote folders, down to system configuration files.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.