Cybersecurity experts have stumbled upon the eight-year-old Azorult malware. This malware steals information and collects sensitive data, and has been down since late 2021. But will the old dog keep up to new tricks?
Azorult Malware Resurfaces After 2 Years
A recent research in the cyber threat landscape has brought to light concerning news about the Azorult malware. First identified in 2016, this malware gained quite an image back in the days>. Among its most noticeable campaigns is spreading together with STOP/Djvu ransomware. However, its activity was declining since early 2020, with activity curve going flat in late 2021.
Being a stealer malware from the mid-10’s, it originally carried functionality that suited the times. Azorult specializes in stealing sensitive information. It includes things such as browsing history, cookies, and login credentials. No crypto wallets, no session and 2FA tokens – those were not that valuable back in the days.
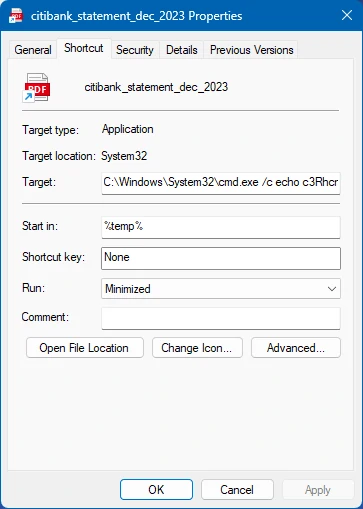
Among the key news of the resurfaced version are more sophisticated and stealthy methods, which could make it very difficult to detect. It also uses a new infection chain and uses RAM as a springboard for deploying and executing the entire payload. Researchers stumbled upon shortcut files masquerading as PDF files, eventually leading to Azorult infecting the device. As for the distribution method, experts suggest using classic means like email phishing.
What is Azorult Malware?
The Azorult malware is a spyware that can steal various data types, including credentials for applications and cryptocurrencies. It is known for its capabilities in harvesting sensitive data from infected systems. Azorult can also download and execute additional payloads, increasing its threat to compromised systems.
In its latest variant, Azorult uses process injection and “Living Off the Land” (LotL) techniques to evade detection by security tools and is primarily sold on Russian underground hacker forums. Data stolen with Azorult is also sold on Russian Dark Web marketplaces. In addition to stealing information, >the malware captured data for a service that sells ready-made virtual identities. This included as much detailed data as possible about users’ online behavior: history of website visits, information about the operating system, browser, installed plugins, etc.
In particular, researchers found that 90% of all digital footprints provided on an infamous Genesis Market were associated with Azorult. However, in February 2020, Google released a Chrome update that enforced the use of AES-256 for password encryption. This affected Azorult ability to retrieve passwords from Chrome. As the development of AZORult was discontinued in 2018, this release was concidered a “death” of AZORult, impacting Genesis’s business as well.
Azorult Uses Email Spam and LNK Files
The reviewed example of Azorult, as I mentioned above, came as an .lnk file disguised as a PDF document through the double extension tricks. A file named citibank_statement_dec_2023.lnk triggers a sequence of events that downloads and executes a JavaScript file from a remote server. The JavaScript file downloads two PowerShell scripts, one of which retrieves an executable file and initiates a new thread to execute the injected code. The loader file terminates if the user’s language code matches specific codes linked to Russia – the most probable region of its developers. The final payload is, obviously, the Azorult infostealer.
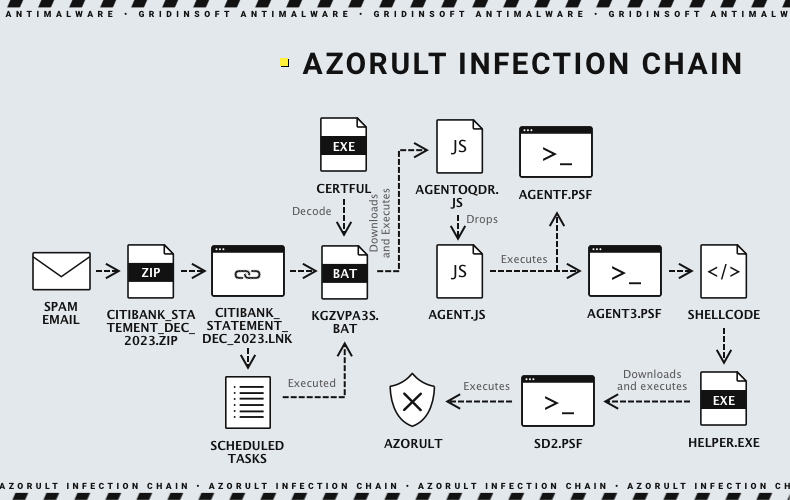
Upon execution, it generates a unique identifier for the victim and collects system information, including crypto wallets. Azorult terminates execution if certain conditions are met, such as the presence of a mutex or a file named “password.txt” on the Desktop. It also checks for specific machine names and usernames on the victim’s system. If any of the checks return true, the binary terminates. Azorult captures screenshots and targets multiple applications. The data is compressed, encrypted, and sent to a remote server.
Safety Recommendations
Since human error is mostly to blame, the most important recommendation is to beware of phishing. To elaborate, the following points will be helpful:
- Unsolicited Emails. Always be skeptical and cautious of emails from unknown sources. Especially those that request personal information or urge you to click on a link.
- Verify Email Sources. Before responding or clicking any links, verify the sender’s email address and ensure it’s legitimate. Don’t click on links in emails, especially if they seem suspicious or too good to be true.
- Educate Yourself. Stay informed about phishing methods and various phishing-based scam techniques.




