Gridinsoft LLC is proud to be one of 68 partners of VirusTotal, Google’s Information Security Service, in the array of malware scanners. Currently, Gridinsoft is the second information security company in Ukraine to be in an equal position with the world’s technology giants in this field. VirusTotal is a free online service provided by Google,… Continue reading Gridinsoft becomes Google’s information security partner
Author: Vladimir Krasnogolovy
Vladimir is a technical specialist who loves giving qualified advices and tips on GridinSoft's products. He's available 24/7 to assist you in any question regarding internet security.
Microsoft has released an update to remove Adobe Flash from Windows
As you know, very soon, on December 31, 2020, support for Adobe Flash Player will be completely discontinued, after which it will no longer be supported by all modern browsers. Now Microsoft has released an update to remove Adobe Flash from Windows. Let me remind you that work on a complete rejection of Flash Player… Continue reading Microsoft has released an update to remove Adobe Flash from Windows
KashmirBlack botnet is behind attacks on popular CMS including WordPress, Joomla and Drupal
Researchers from Imperva have found that the KashmirBlack botnet, active since the end of 2019, is behind attacks on hundreds of thousands of websites powered by popular CMS, including WordPress, Joomla, PrestaShop, Magneto, Drupal, vBulletin, osCommerce, OpenCart and Yeager. As a rule, a botnet uses the servers of infected resources to mine cryptocurrency, redirects legitimate… Continue reading KashmirBlack botnet is behind attacks on popular CMS including WordPress, Joomla and Drupal
Attackers again deceived Apple’s notarization process
In September 2020, I talked about how the Shlayer malware successfully passed the notarization process and was able to run on any Mac running macOS Catalina and newer. Now there is information that the attackers again deceived the notarization process. Apple introduced the “notarization process” security mechanism in February of this year: any Mac software… Continue reading Attackers again deceived Apple’s notarization process
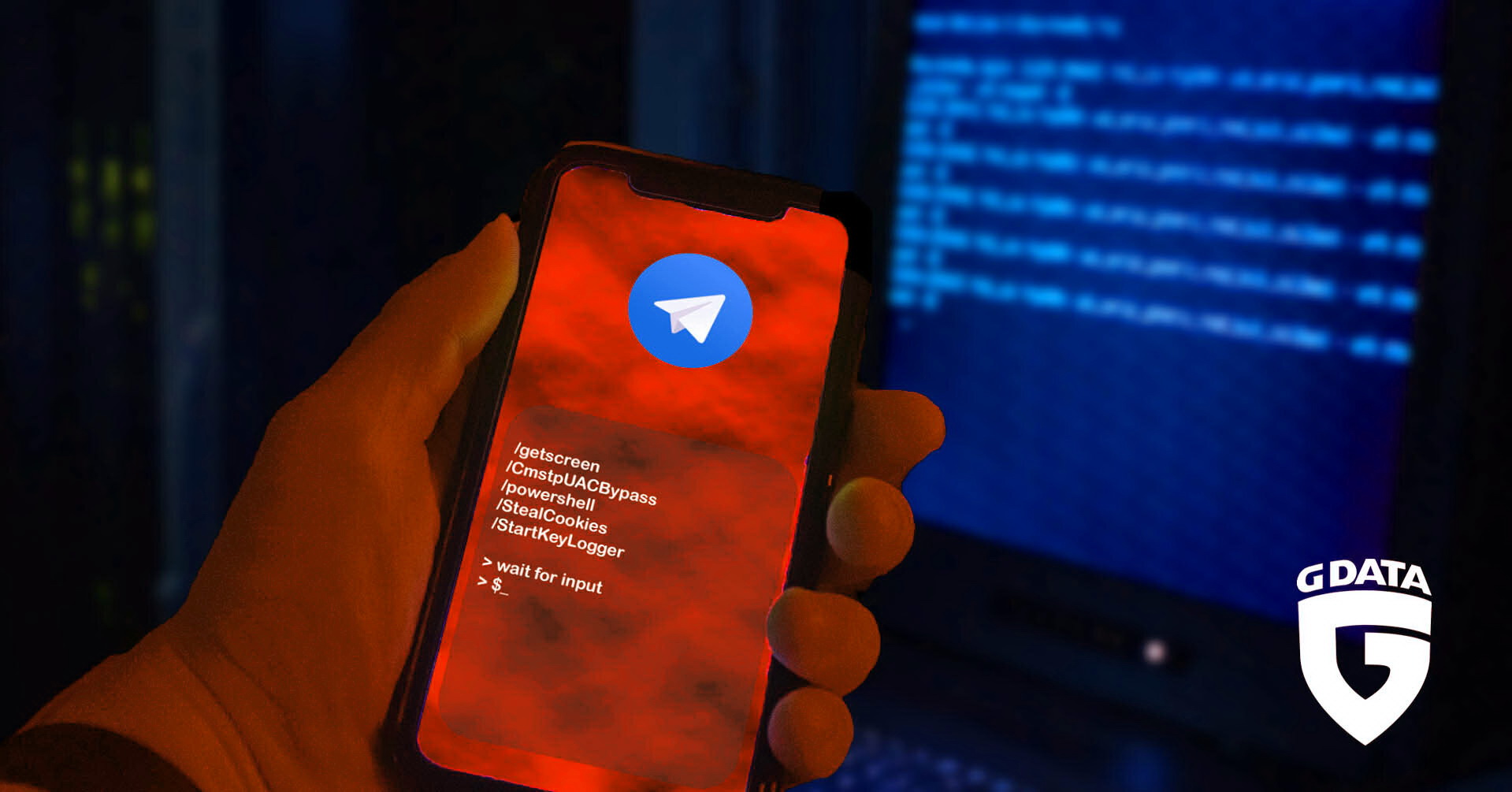
New T-RAT malware can be controlled via Telegram
G DATA’s specialists have published a report on the new T-RAT malware, which is being distributed for only $45. The main feature of the malware is that T-RAT allows controlling infected systems through the Telegram channel, and not through the web administration panel, as it is usually done. Malware creators claim that this provides faster… Continue reading New T-RAT malware can be controlled via Telegram
Experts discovered that many mobile browsers are vulnerable to url spoofing
Rapid7 analysts and independent information security expert Rafay Baloch discovered that seven popular mobile browsers are vulnerable to url spoofing. They allow malicious sites to change the URL and display a spoofed address in the address bar. Basically, the problem of address bar spoofing existed since emergence of the Internet. With the ever-increasing sophistication of… Continue reading Experts discovered that many mobile browsers are vulnerable to url spoofing
Google engineers fixed Chrome 0-day vulnerability that was already under attacks
Google engineers have released an updated version of Google Chrome (86.0.4240.111) and warn that they have fixed in browser 0-day vulnerability that has been already under active attacks. The error was discovered internally by Google Project Zero. It is identified as CVE-2020-15999 and is associated with the FreeType font rendering library included with standard Chrome… Continue reading Google engineers fixed Chrome 0-day vulnerability that was already under attacks
Bughunter stole a Monero exploit from another cybersecurity specialist and received a reward for it
Bleeping Computer reporters drew attention to an interesting case that occurred as part of the bug bounty of the Monero program on HackerOne. Bughunter stole a Monero vulnerability exploit discovered by another person and received a reward. The publication notes that bug hunting is not just a good cause that benefits the community, but also… Continue reading Bughunter stole a Monero exploit from another cybersecurity specialist and received a reward for it
P2P botnet Interplanetary Storm accounts more than 9000 devices
Bitdefender experts gave a detailed description of the work of the P2P botnet Interplanetary Storm (aka IPStorm), which uses infected devices as a proxy. According to researchers, the botnet includes more than 9,000 hosts (according to other sources, the number of infected devices exceeds 13,500), the vast majority of which are running Android, and about… Continue reading P2P botnet Interplanetary Storm accounts more than 9000 devices
Google revealed the most powerful DDoS attack in history
This week, the Google Cloud team talked about a previously unknown DDoS attack that targeted a Google service back in September 2017 and peaked at 2.54 TB/sec, making it the most powerful recorded attack in history. Soon, analysts from the Google Threat Analysis Group (TAG) published their report on the incident, in which they said… Continue reading Google revealed the most powerful DDoS attack in history