Zscaler analysts reported about the new DreamBus botnet that attacks corporate applications on Linux servers. It is a variation of the SystemdMiner malware that appeared back in 2019. DreamBus has received a number of improvements over SystemdMiner. For example, the botnet mainly targets enterprise applications running on Linux systems, including PostgreSQL, Redis, Hadoop YARN, Apache… Continue reading DreamBus botnet attacks corporate applications on Linux servers
Author: Vladimir Krasnogolovy
Vladimir is a technical specialist who loves giving qualified advices and tips on GridinSoft's products. He's available 24/7 to assist you in any question regarding internet security.
Authorities of South Africa create their own browser to continue to use Flash
ZDNet reports that the South Africa Revenue service has created its own browser to continue using the Adobe Flash Player on the existing site, taking some web forms from Flash to HTML. Let me remind you that Flash Player support was finally discontinued on December 31, 2020. In addition, a unique mechanism for self-destruction was… Continue reading Authorities of South Africa create their own browser to continue to use Flash
End of support for Adobe Flash caused interruptions in the Chinese railway system
As you know, back in 2017, Apple, Facebook, Google, Microsoft, Mozilla, as well as Adobe itself announced the end of support for Adobe Flash. The technology was officially “killed” on December 31, 2020, after which support for Adobe Flash Player was finally discontinued. In December, Adobe released the latest Flash update and has become more… Continue reading End of support for Adobe Flash caused interruptions in the Chinese railway system
New worm for Android spreads rapidly via WhatsApp
ESET security researcher Lukas Stefanko reported a new malware: he said that a new worm for Android automatically spreads through WhatsApp messages. The main purpose of malware is to trick users into adware or subscription scams. The link to the fake Huawei Mobile app redirects users to a site that is very similar to the… Continue reading New worm for Android spreads rapidly via WhatsApp
Researcher Found Three Bugs Allowing Hacking Amazon Kindle
Researcher Yogev Bar-On from Israeli consulting firm Realmode Labs talked about his KindleDrip attack technique and three Amazon Kindle bugs (already fixed) that underlie it. For discovery of these vulnerabilities the expert received $18,000 under the bug bounty program. Let me remind you that I also talked about IS researcher earned more than $2000000 on… Continue reading Researcher Found Three Bugs Allowing Hacking Amazon Kindle
Chinese hack group Chimera steals data from air passengers
According to reports of cybersecurity researchers, the Chinese hack group Chimera is stealing data from air passengers. The NCC Group and its subsidiary Fox-IT have published a joint report on the activity of Asian hackers. For the first time, experts from the cybersecurity firm CyCraft spoke about this group last year, presenting their findings at… Continue reading Chinese hack group Chimera steals data from air passengers
Raindrop is another malware detected during the SolarWinds hack
Symantec specialists detected Raindrop malware, which was used during the attack on SolarWinds along with other malware. According to the researchers, Raindrop was used by cybercriminals in the last stages of the attack and was deployed only on the networks of a few selected targets (only four malware samples were found). Let me remind you… Continue reading Raindrop is another malware detected during the SolarWinds hack
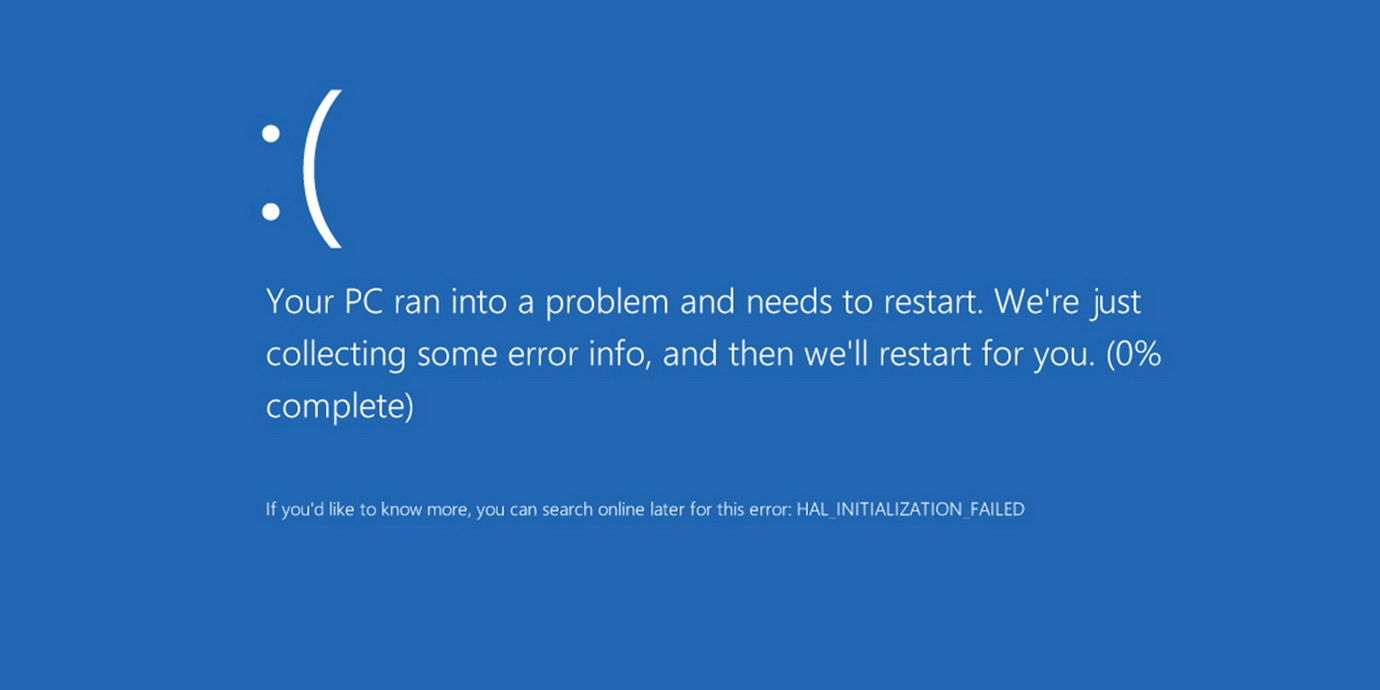
Windows 10 bug causes BSOD when opening a specific path
A bug in Windows 10 causes the OS to crash with a blue screen of death (BSOD) if the user tries to open a specific path in the address bar of the browser or uses other Windows commands. Last week, Twitter posted messages from a security researcher about two vulnerabilities in Windows that could be… Continue reading Windows 10 bug causes BSOD when opening a specific path
Hackers majorly use Microsoft and DHL brands in phishing attacks
Hackers majorly use the Microsoft and DHL brands in phishing attacks. In Q4 2020, cybercriminals used more brands from the tech industry, followed by shipping and retail businesses. Information security researchers from the Check Point Software team said that phishers love the Microsoft brand. 43% of all attempts at phishing attacks were associated with it… Continue reading Hackers majorly use Microsoft and DHL brands in phishing attacks
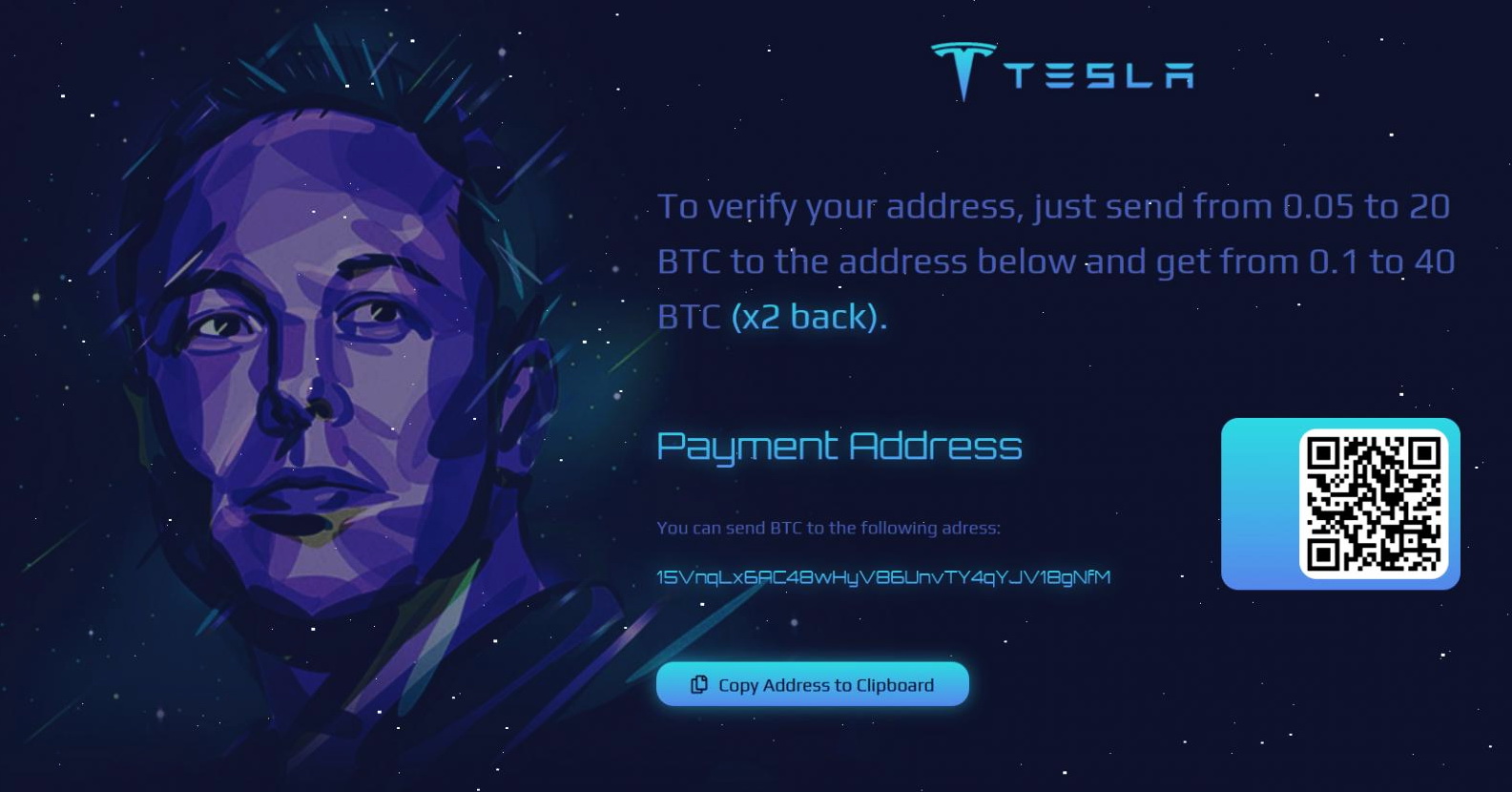
Fake cryptocurrency giveaways on behalf of Elon Musk brought scammers $580,000
The media have repeatedly written that scammers sometimes impersonate famous people. For example, last year, cybercriminals arranged fake giveaways of cryptocurrency on behalf of Elon Musk or SpaceX that had hard consequences for naive users. In particular, criminals are very fond of conducting fake distributions of cryptocurrencies on social networks on behalf of Mask, promising… Continue reading Fake cryptocurrency giveaways on behalf of Elon Musk brought scammers $580,000