LockBit Weaponizes Its Victims’ Clients – Brett Callow
Brett Callow, a cybersecurity analyst at Emsisoft, shared information on his Twitter…
Conti vs. LockBit 2.0 – a Trend Micro Research in Brief
Trend Micro, a Japanese IT security company, has published a thorough comparison…
Conti Ransomware Shutdown, Site Disabled
Conti operators shut down the remnants of the public infrastructure. Two servers…
Copyright Claims Used as Bait by LockBit 2.0 Affiliates in Korea
A new type of email-bait has been invented by the affiliates of…
How to Prevent Crimeware Attacks: Users` Guide
You may come across the term "Crimeware" and understandably get confused as…
NCC Group’s May 2022 Threat Report Reflects Conti’s End
NCC Group's monthly report on cyber threats features some curious news, namely…
Privacy Access Tokens to Replace CAPTCHA Real Soon
CAPTCHA, a well-known test for website visitors to prove they are humans,…
8 Symptoms Of Adware: How to Avoid it
What is adware meaning? It is an agressive software whose goal is…
Google Report Companies Creating Mobile Spyware for Governments
Google Reveals An Italian Company to Sell Android and iOS Spyware to…
WiFi-Hacking by Neighbours is Rampant in the UK, Research Says
WiFi-Hacking by Neighbors is Rampant in the UK, Research Says The research…
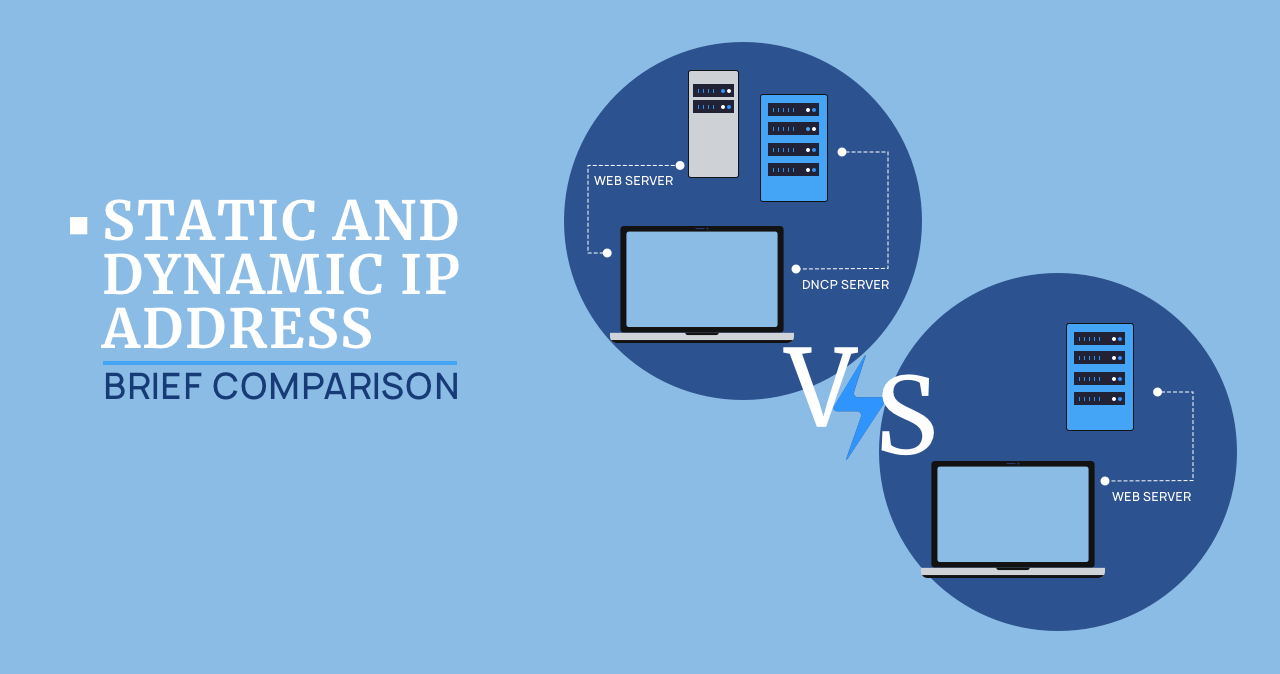
Static And Dynamic Ip Address: Brief Comparison
The Internet is built on IP addresses. They are divided into dynamic…
Nine Web Scammers Arrested by Dutch Police in a Europol Operation
Nine Internet scammers arrested in the Netherlands during Dutch-Belgian joint operation Belgium…