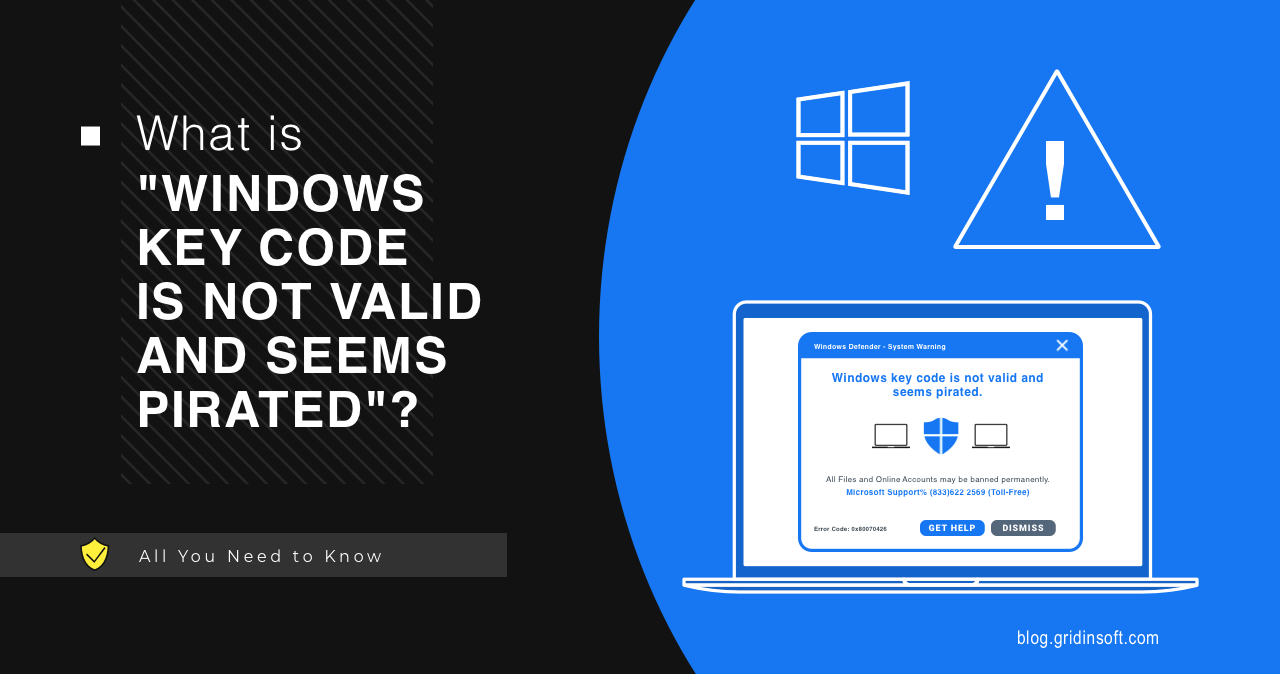
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears to be…
How to Defeat Insider Threat?
In the current digital world, organizations face more risks than ever due…
ChatGPT has become a New tool for Cybercriminals in Social Engineering
Artificial intelligence has become an advanced tool in today's digital world. It…
Conti Ransomware Heritage in 2023 – What is Left?
Ransomware groups come and go, but the people behind them continue to…
What is Business Email Compromise (BEC) Attack?
Business email compromise attack, or shortly BEC, is a relatively new vector…
MOVEit MFT 0-day Vulnerability is Used to Steal Corporate Data
MOVEit managed file transfer (MFT) solution appears to contain a 0-day vulnerability,…
New iOS Vulnerability Allows “Triangulation” Attack
New iOS vulnerability allows executing a zero-click malware delivery through the built-in…
DDoS-for-Hire: Booter, Stresser and DDoSer
Most people think you must be a hacker to participate in cyberattacks.…
Android Malware With Almost 500M Downloads Resides in Google Play
Millions of Android users may be at risk of a cyberattack because…
RarBG Torrenting Site Is Shut Down, Admins Explain Why
RarBG, one of the most famous torrent tracker websites in the world,…
Ransomware Attacks in 2023: What to Expect?
Cybersecurity experts have published a report on worrying ransomware statistics. A survey…
RaidForums Leaked, Data of Almost 500,000 Users Published
RaidForums, the former leader among the underground forums, now suffers the user…