What is Microsoft Security Warning Scam?
Fraudsteds massively employ Microsoft Azure hosting to start Microsoft Security scam pages.…
SecuriDropper Bypasses Google Play & Android Defenses
SecuriDropper is a rare example of the Android dropper malware that operates…
Socks5Systemz Proxy Service Infects 10,000 Systems Worldwide
A proxy botnet, "Socks5Systemz", uses malware loaders to infiltrate computers across the…
Top Maine Lobster Scam on Facebook
Another fraudulent scheme related to the sale of seafood has appeared on…
Boeing Hack Confirmed, LockBit Group Resposible
Boeing, a major aircraft manufacturer and aerospace & defence contractor in the…
Malicious WhatsApp Mods Spread Through Telegram
Some WhatsApp mods, which are unofficial versions of the app, have been…
New F5 BIG-IP Vulnerabilities Exploited In The Wild
Two new vulnerabilities in F5 BIG-IP reportedly allow for remote code execution…
WeChat and Kaspersky Ban in Canada – What You Should Know?
The Canadian government has instituted a ban on the use of WeChat…
New Confluence Vulnerability Leads to Unauthorised Access
Another vulnerability in the flagship product of Atlassian corporation, Confluence, allows hackers…
Octo Tempest Threat Actor – The Most Dangerous Cybercrime Gang?
Octo Tempest, a financially-motivated hacking group, has been labeled "one of the…
IoT Malware Attacks Grow by 400% in 2023
IoT malware has been a major concern over the last decade. However,…
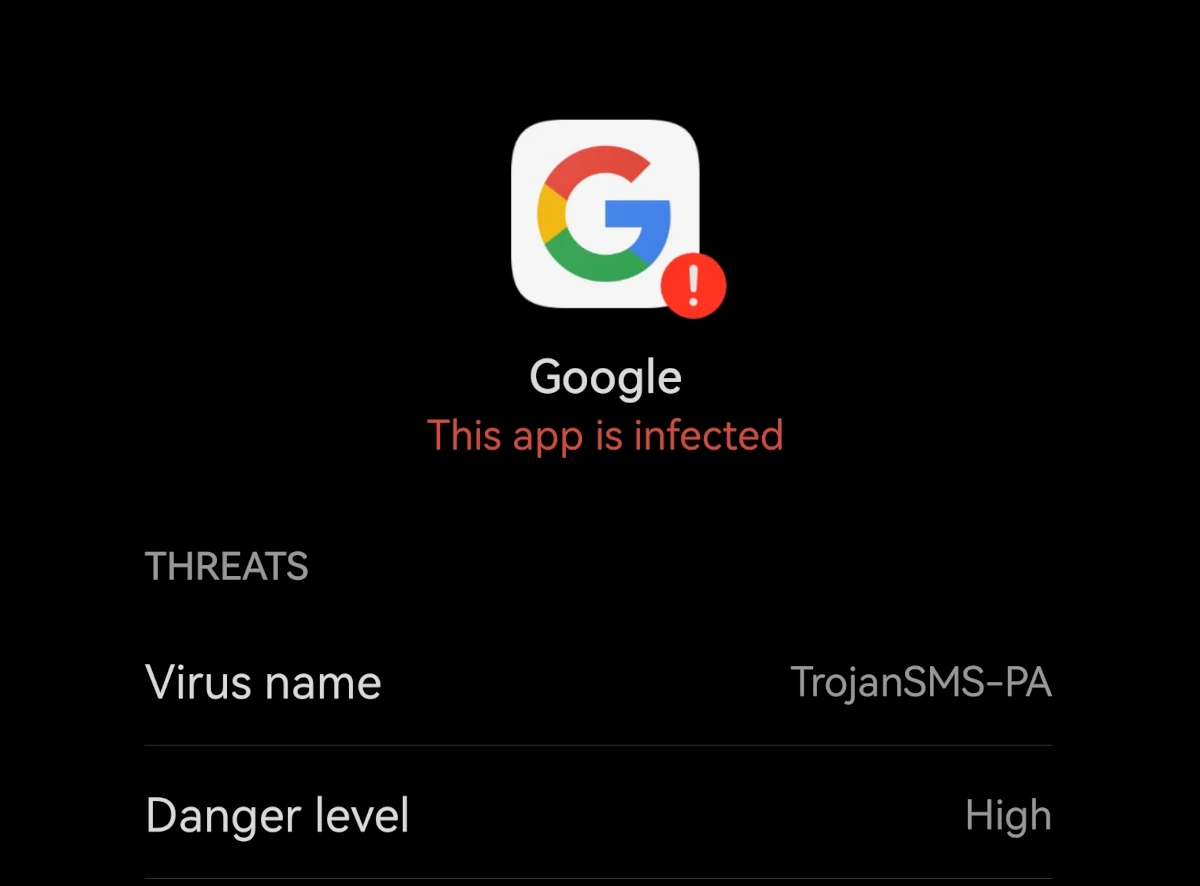
What is Android:TrojanSMS-PA detection?
Android:TrojanSMS-PA is a detection name from a built-in Huawei security tool. This…